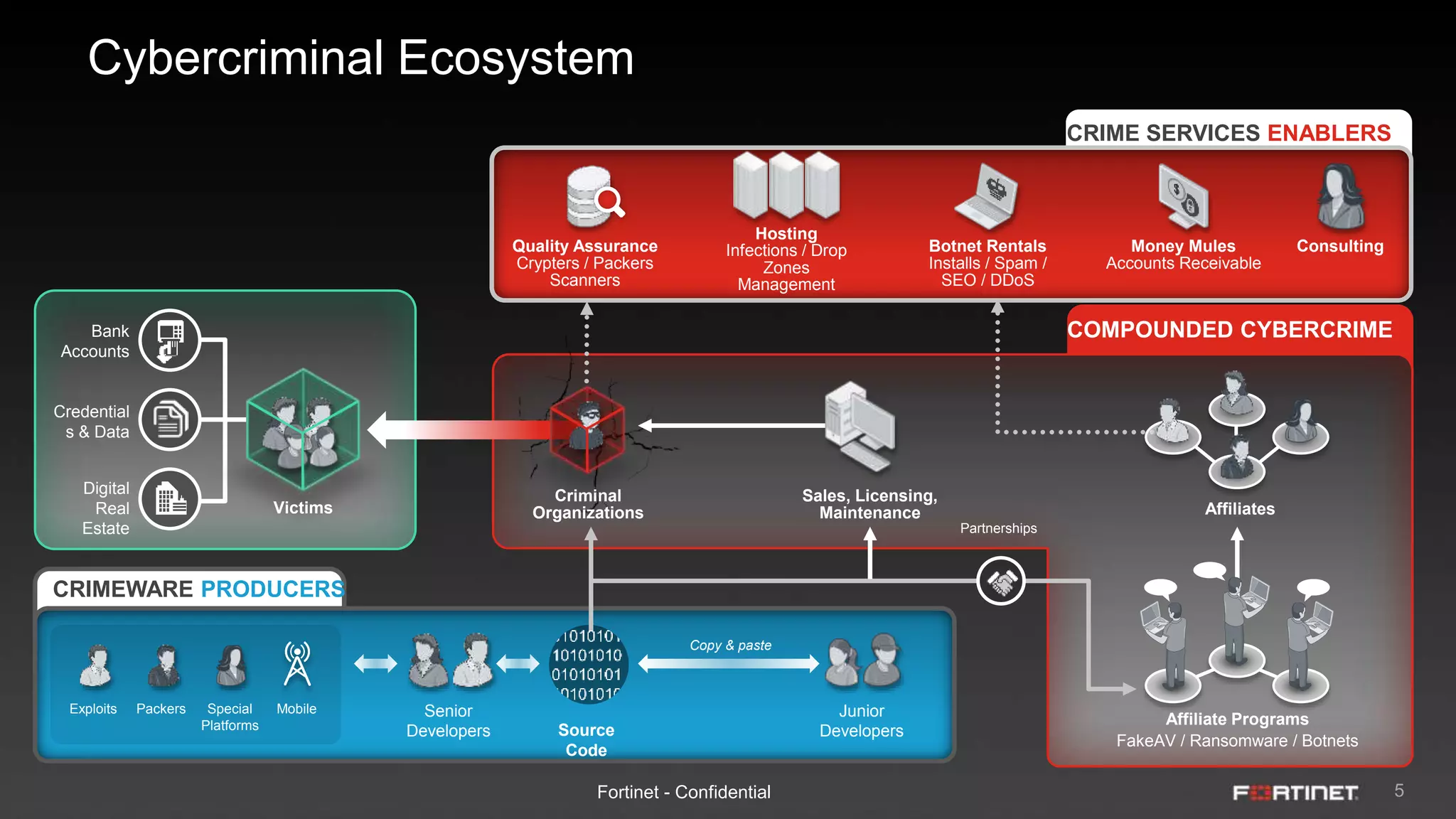
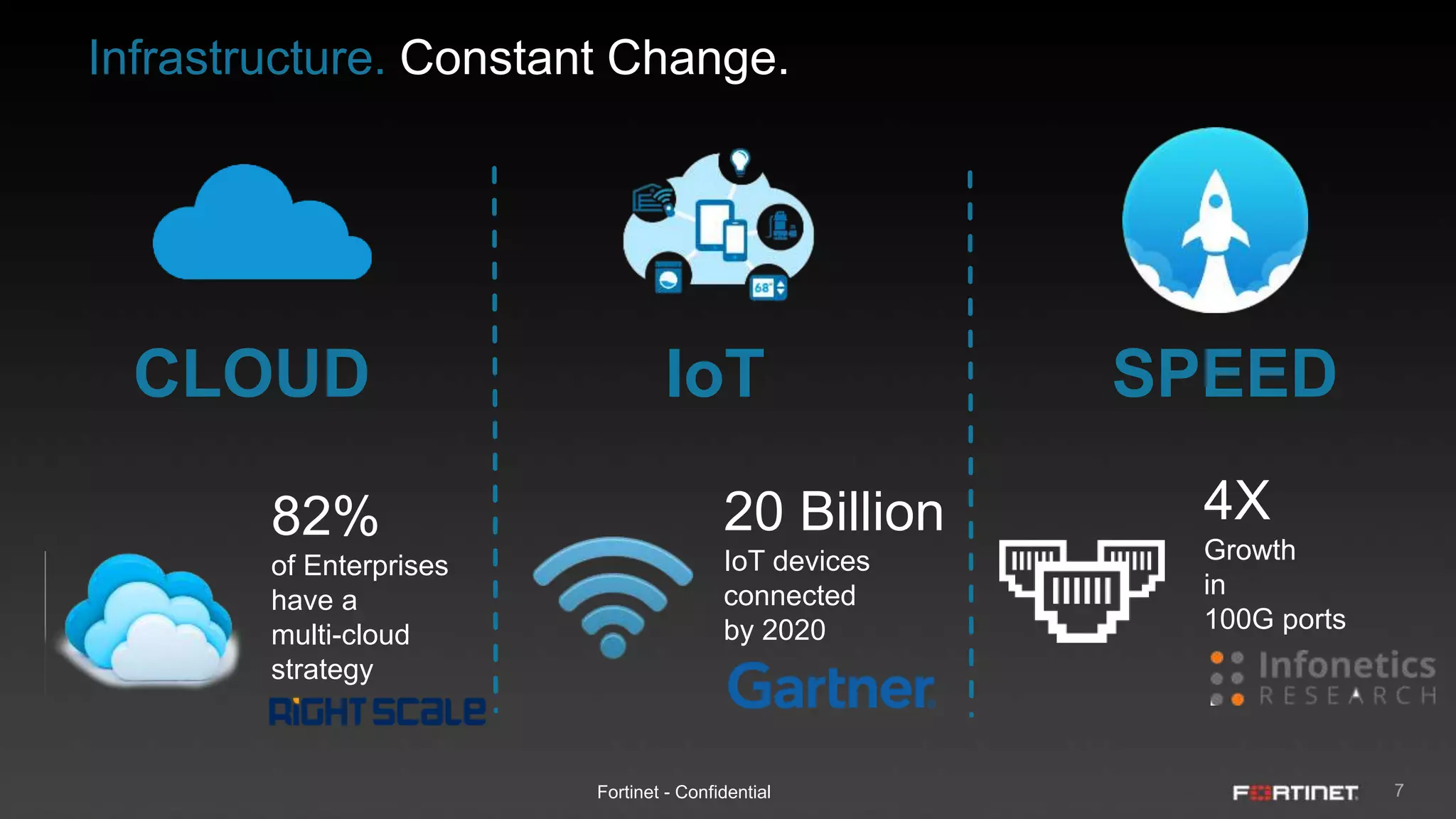
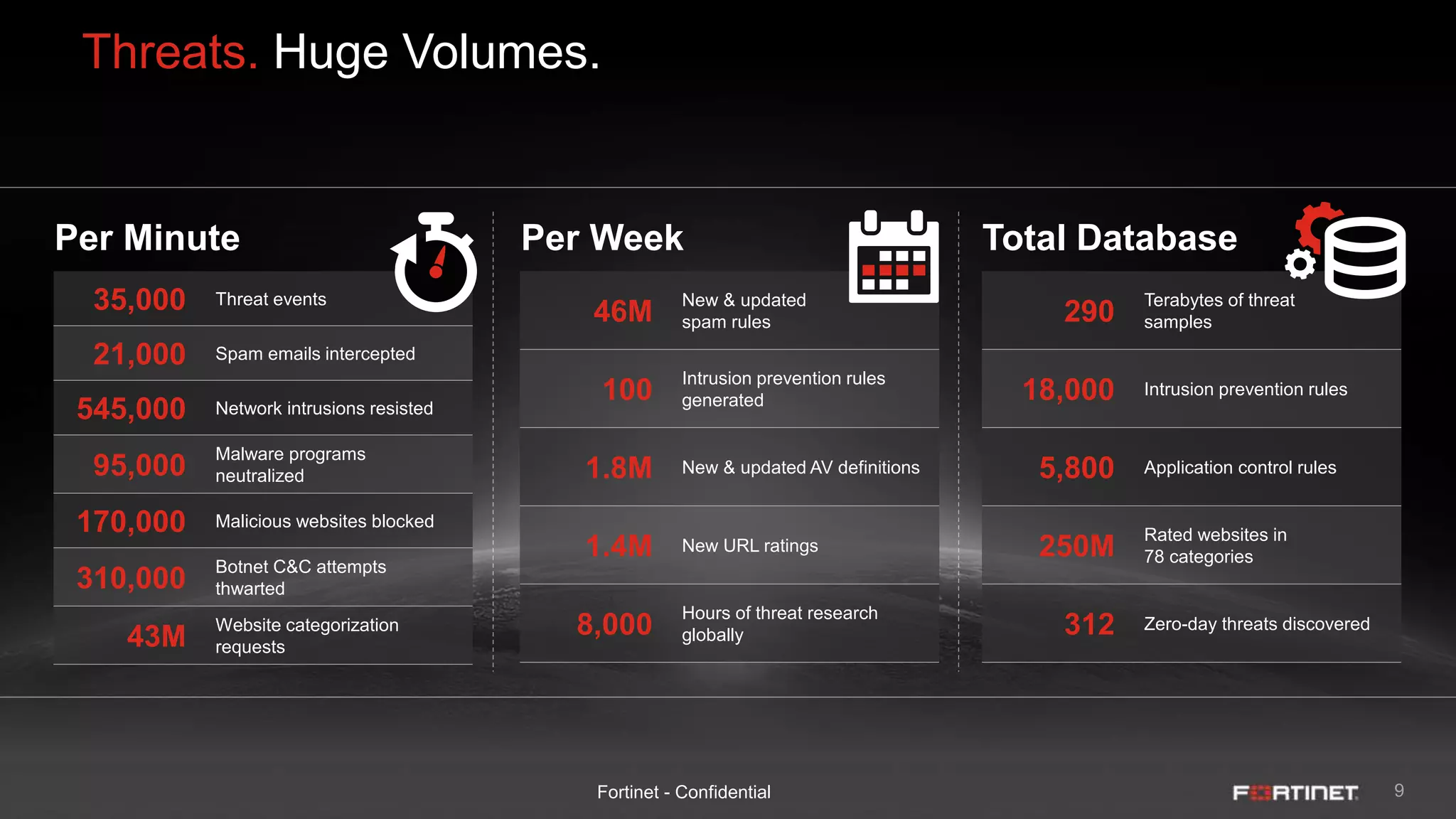
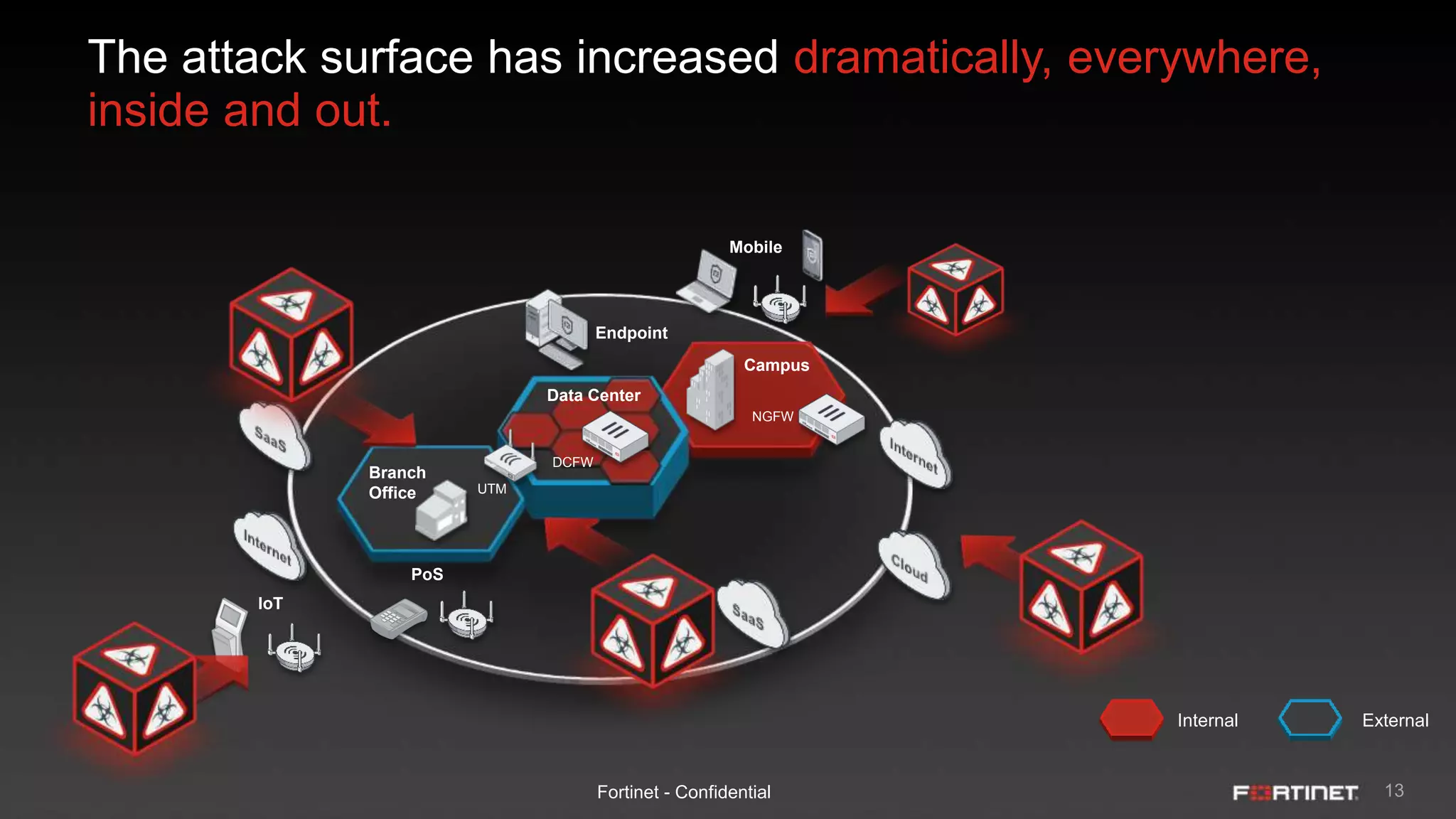
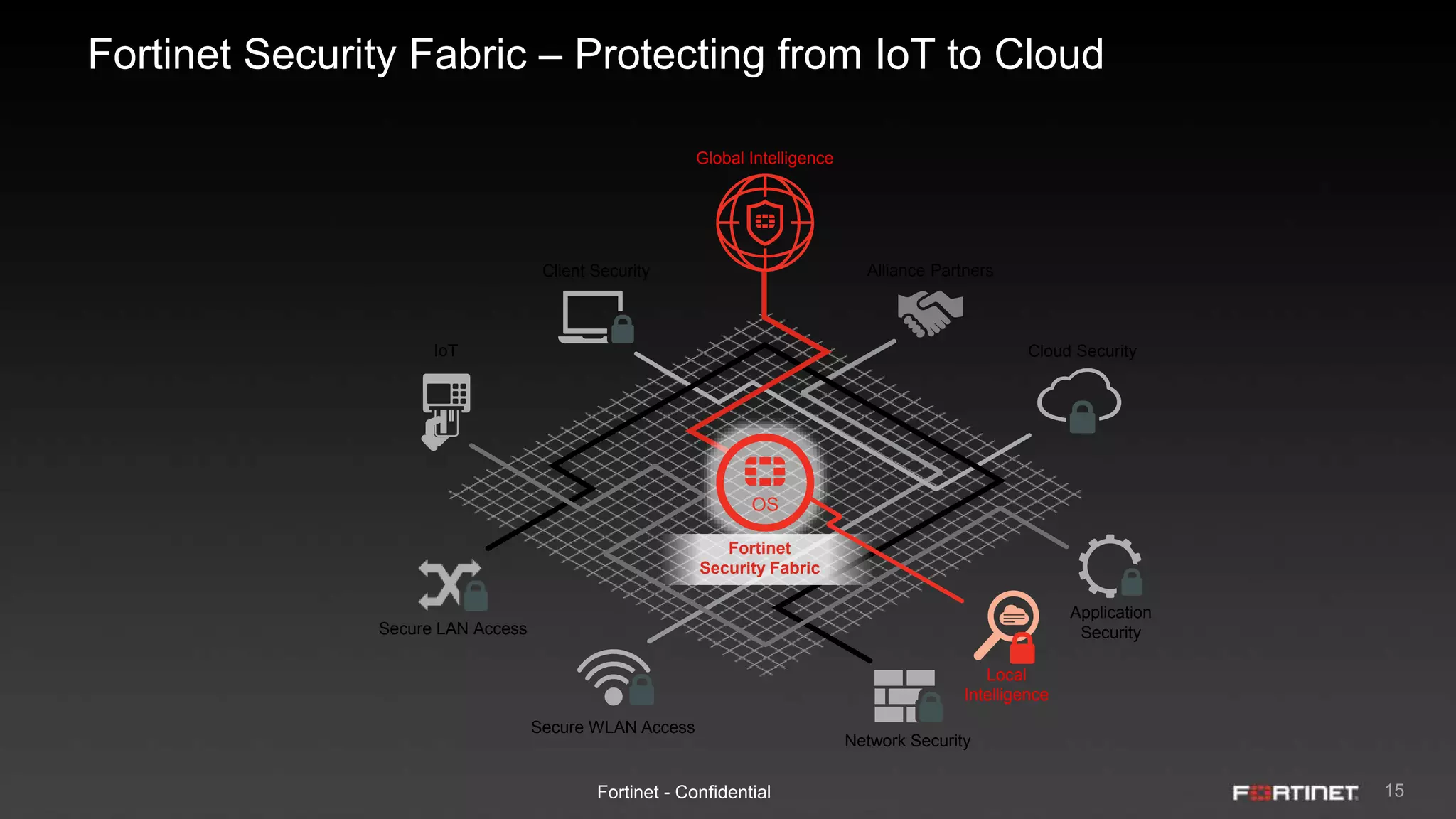
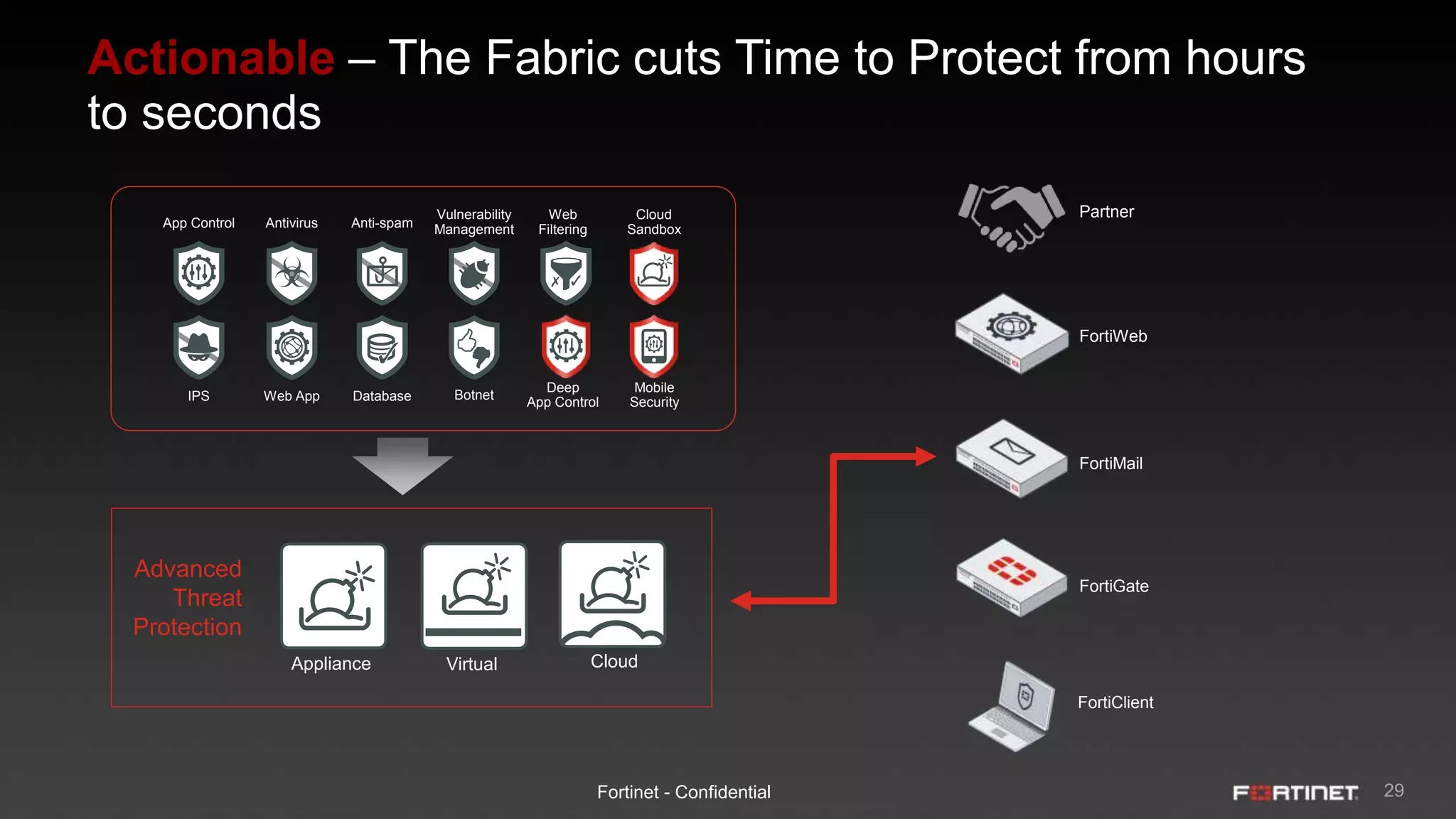
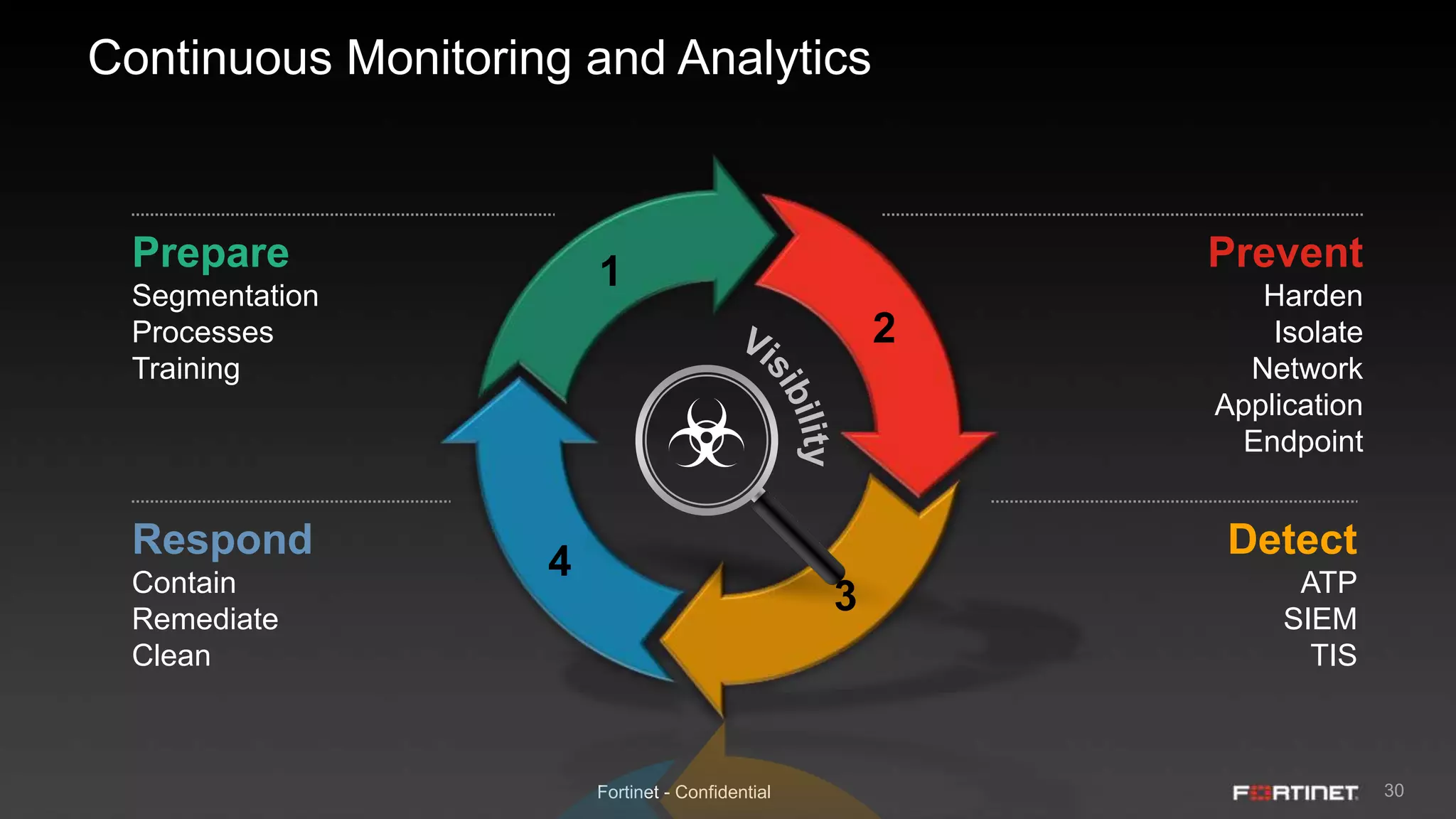
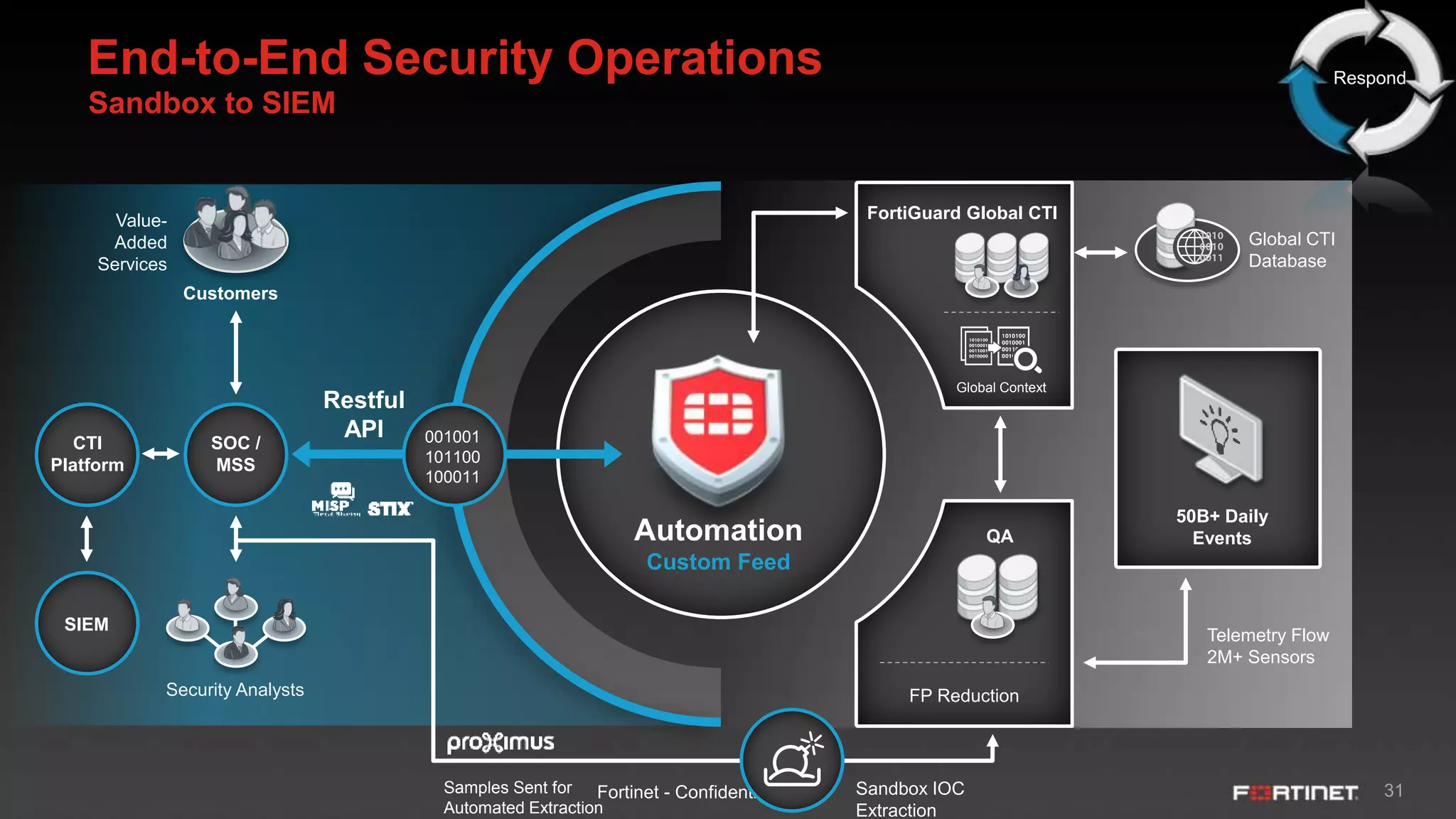
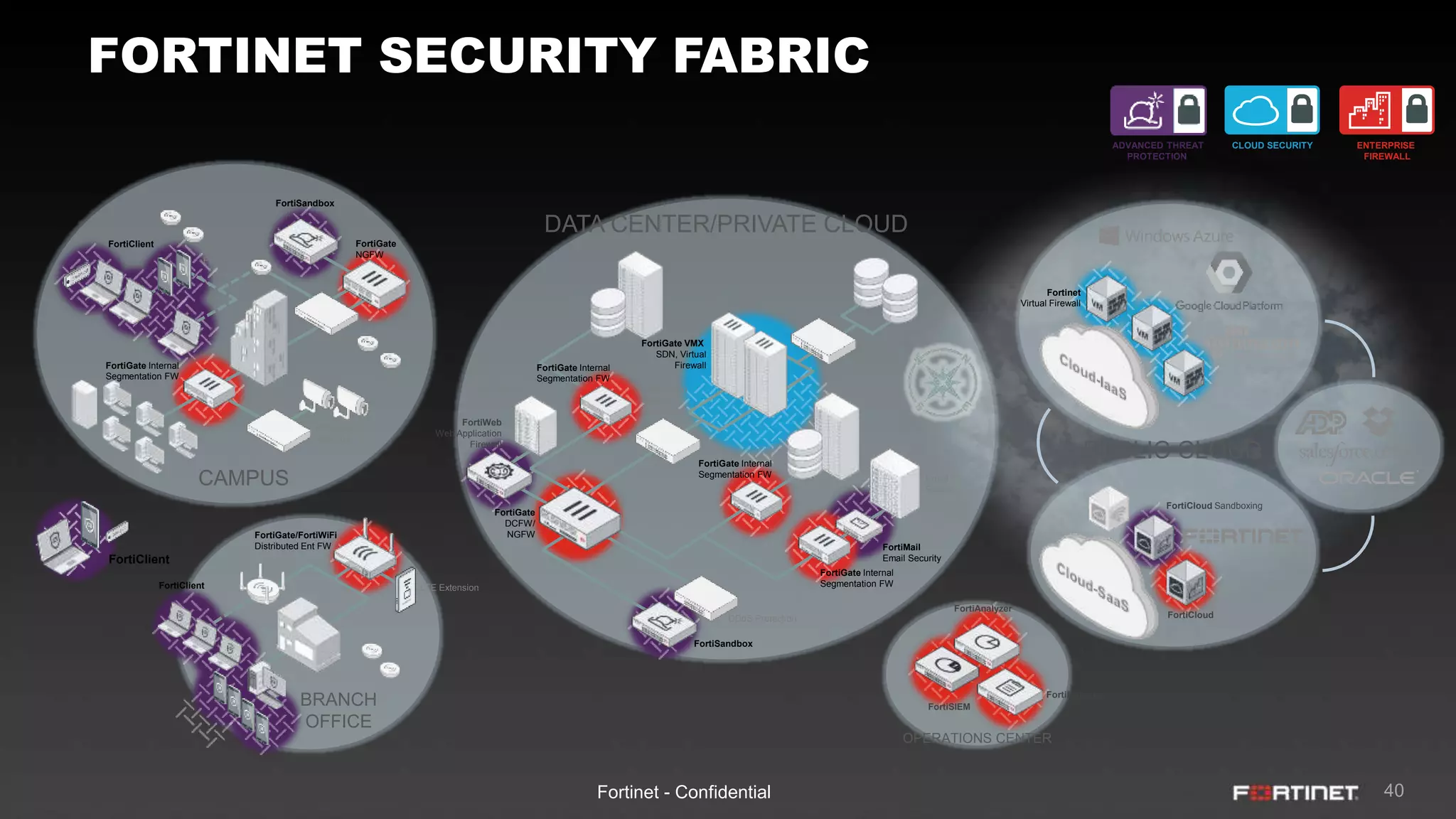
This document provides an overview of the Fortinet Security Fabric. It discusses how the Security Fabric provides end-to-end security across the entire network from IoT to cloud by integrating Fortinet's security solutions. It also highlights key capabilities of the Security Fabric such as being scalable, aware, secure, actionable and open.