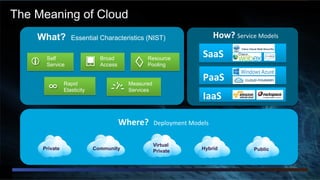
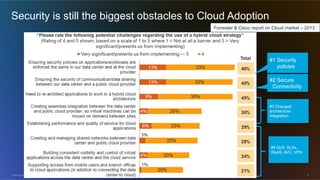
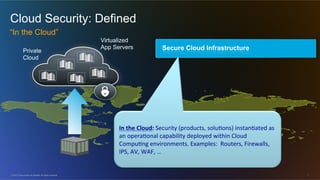
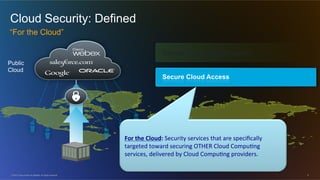
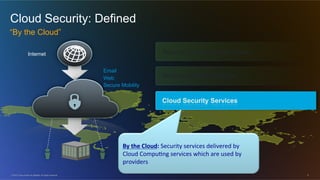
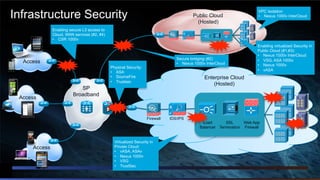
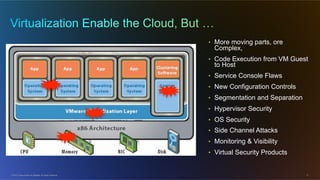
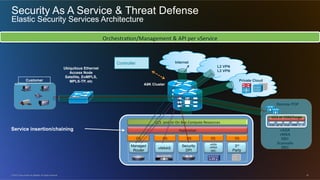
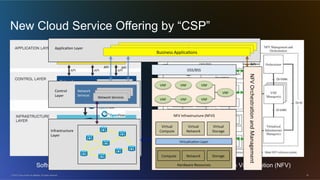
The document discusses cloud security from the perspective of Wen-Pai Lu, a technical leader at Cisco. It defines cloud security as security products and solutions deployed within cloud computing environments ("in the cloud") or targeted at securing other cloud services ("for the cloud"). It also discusses security services delivered by cloud computing services ("by the cloud"). The document outlines many considerations for cloud security, including infrastructure security, applications and software, physical security, human risks, compliance, disaster recovery, threats, and perspectives from both enterprises and service providers.