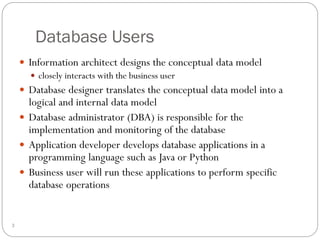
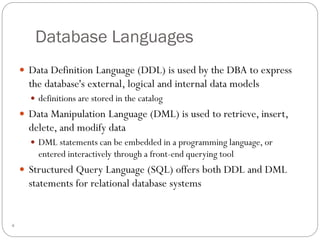
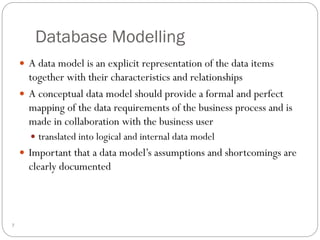
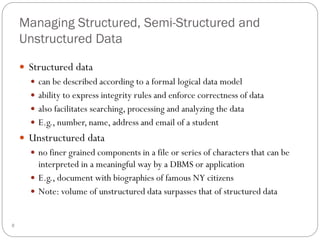
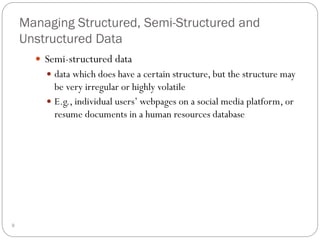
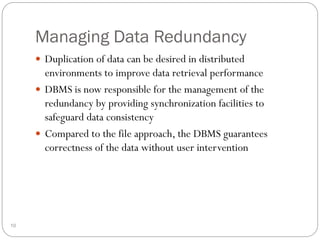
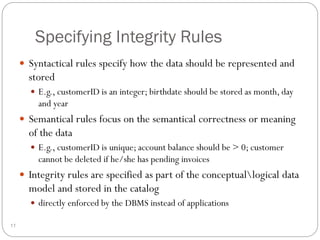
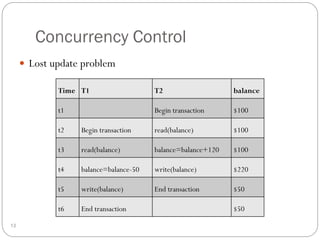
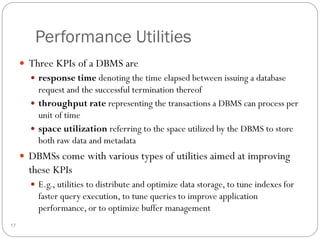
This document outlines fundamental concepts of database management, covering definitions of databases and database management systems (DBMS), roles of database users, and database languages such as DDL and DML. It discusses the advantages of database systems including data independence, concurrency control, and backup facilities, while also addressing the management of different types of data and the importance of integrity rules and data security. Additionally, it highlights performance utilities and the role of DBMS in improving key performance indicators.