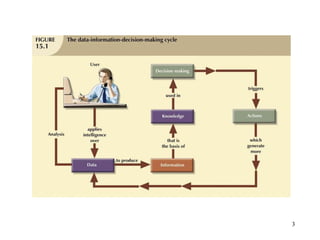
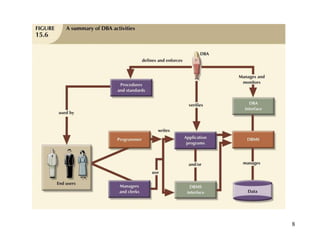
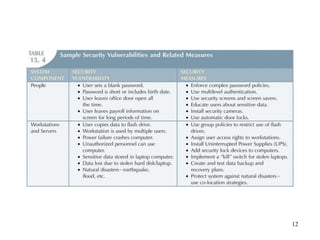
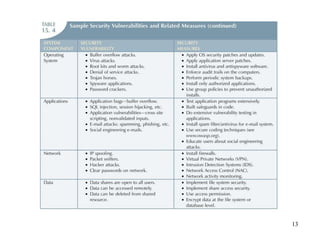
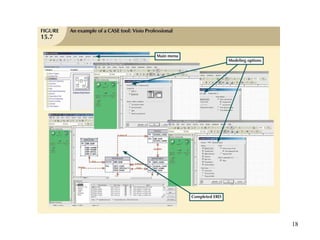
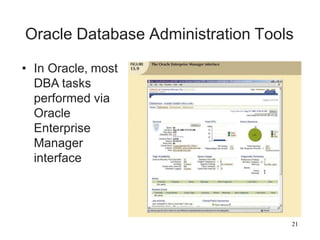
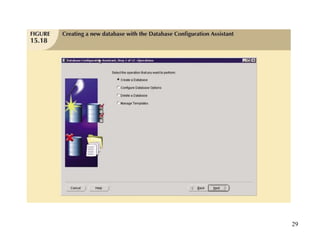
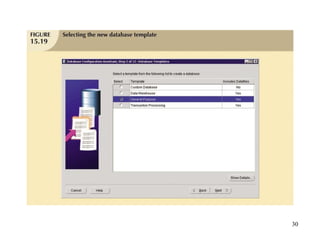
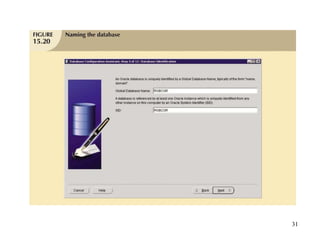
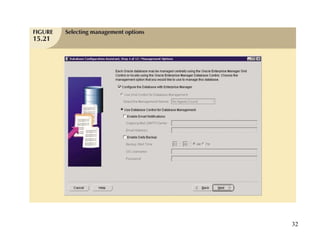
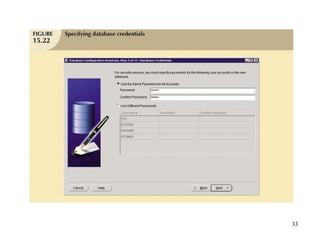
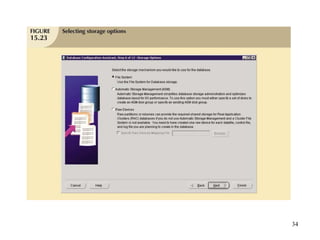
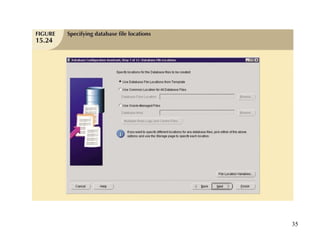
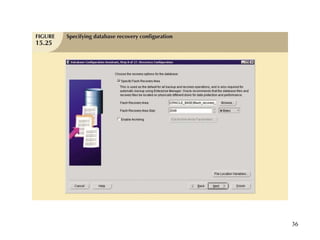
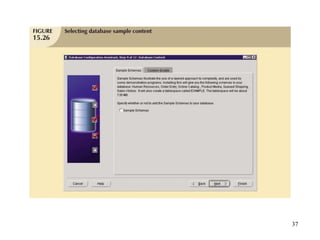
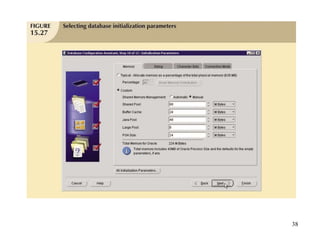
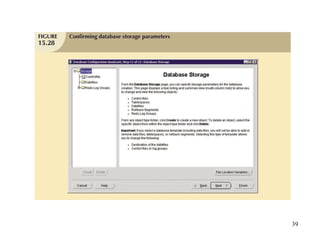
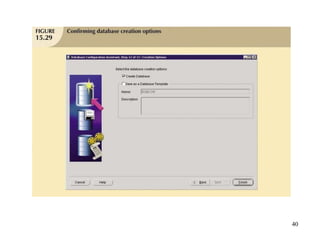
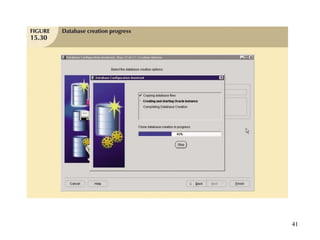
Database management is a critical corporate activity where data is treated as a valuable asset. A database management system (DBMS) is commonly used to support decision making across management levels by facilitating data interpretation, distribution, preservation, and access control. The database administrator (DBA) manages the corporate database through technical tasks like storage management and user administration, while the data administrator (DA) handles broader data management through a more managerial role. Security policies are developed to maintain data confidentiality, integrity and availability.