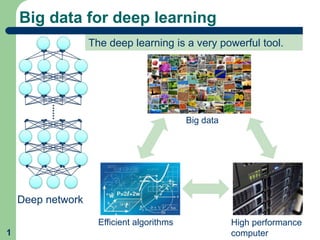
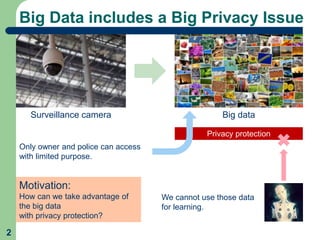
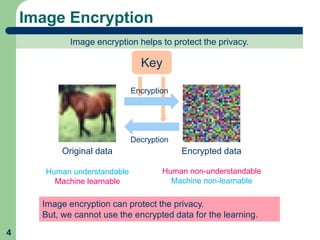
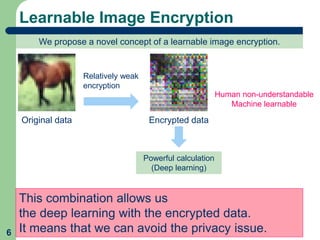
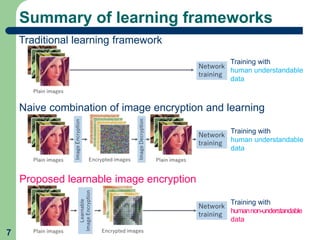
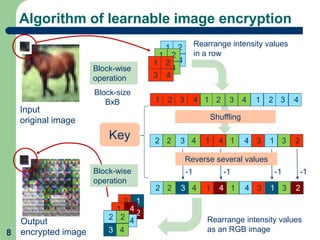
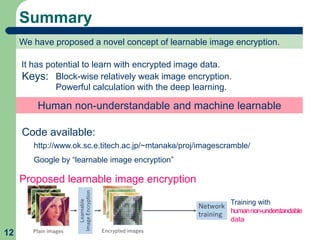
This document proposes a method called learnable image encryption that allows deep learning to be performed on encrypted images while protecting privacy. It works by applying weak block-wise encryption to images before training deep learning models. The models can still learn meaningful patterns from the encrypted images. This approach could help shopping malls analyze customer behavior from security camera footage or allow companies to develop AI systems using encrypted data without compromising privacy. The method achieves comparable accuracy to training on plain images while keeping the encrypted images unintelligible to humans. Code and details on the block-wise encryption and decryption algorithms are available online.