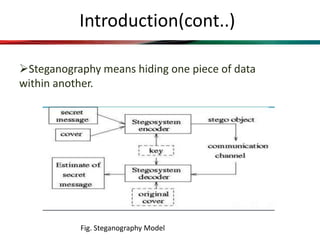
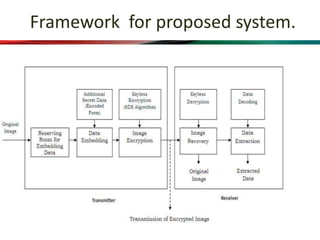
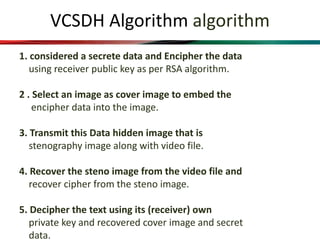
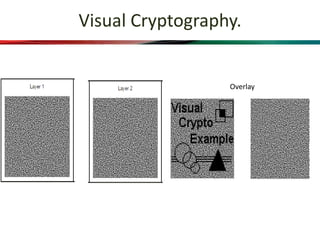
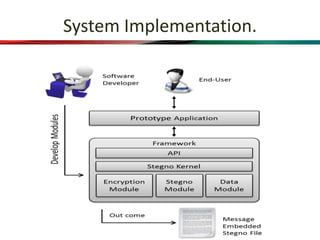
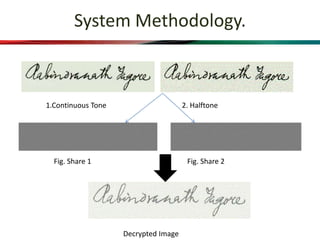
This document proposes a system that combines visual cryptography and steganography to provide multiple levels of security. It aims to overcome the limitations of single-level hiding approaches. The proposed system first encrypts a secret message using RSA encryption and then hides the cipher text in an image using steganography. This stego image is transmitted along with a cover video. The receiver extracts the stego image from the video and decrypts the cipher text using their private key to retrieve the original secret message. The system implements visual cryptography to allow decryption through human vision without requiring any computation.