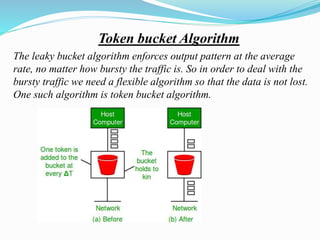
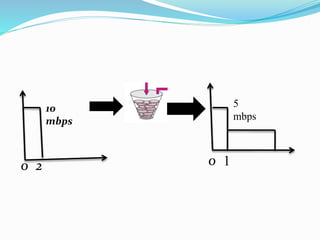
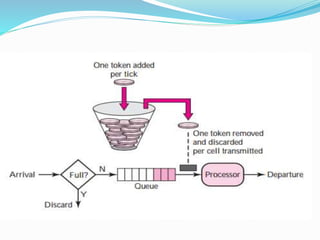
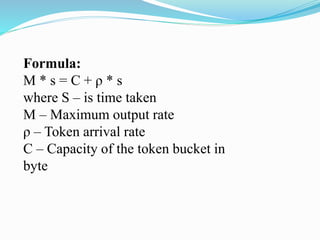
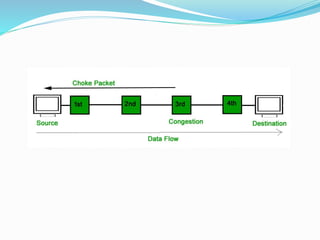
The document discusses network congestion, which occurs when heavy traffic slows down response times, and explores traffic shaping as a management technique to optimize bandwidth for critical applications. It outlines two congestion control algorithms: the leaky bucket algorithm, which maintains a steady output rate regardless of input bursts, and the token bucket algorithm, which allows for flexible output based on token generation. Additionally, it describes choke packets used for informing nodes to reduce their transmission rates in response to congestion.