This document discusses key concepts related to digital transmission including:
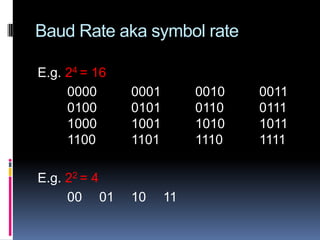
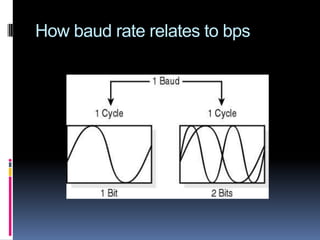
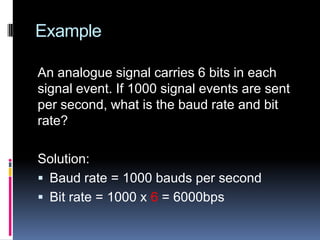
- Bits per second and baud rate which measure transmission speed and signal changes.
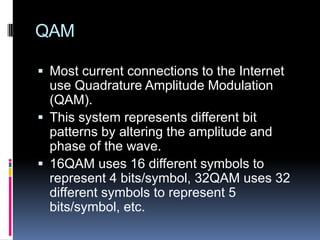
- Modulation techniques like QAM that represent data using signal amplitude and phase.
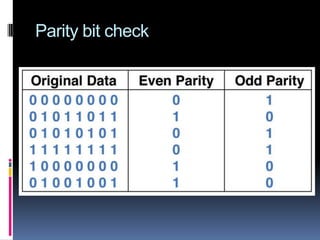
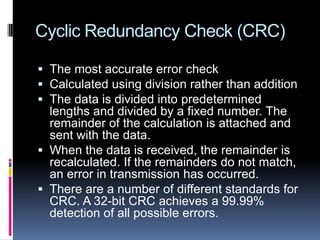
- Error checking methods like parity bits, checksums, and CRC that detect errors in transmission.
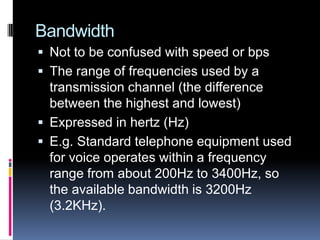
- Factors that affect transmission times like bandwidth, distance, and error checking overhead.