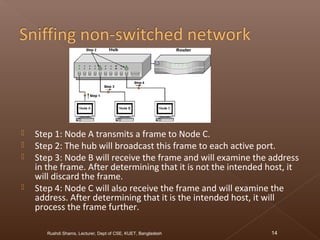
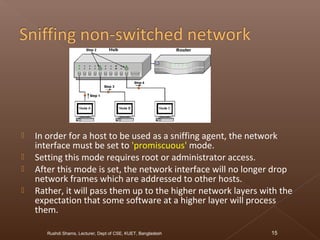
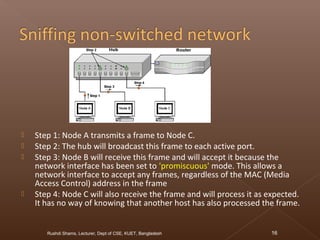
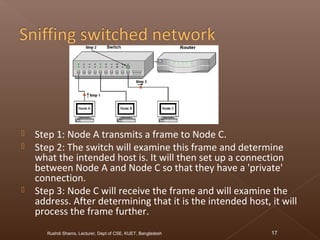
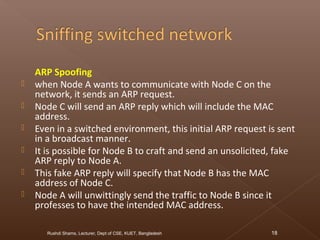
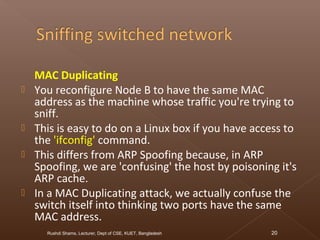
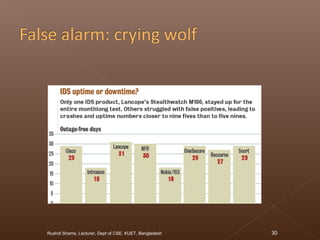
The document discusses network security and intrusion detection. It states that security must use a layered "defense in depth" strategy, as no single measure is sufficient on its own. While firewalls are common, simply allowing all web traffic enables malicious activity. Intrusion detection systems (IDS) monitor traffic for attack signatures. IDS gather information from systems and networks to identify breaches from outside or within an organization. Knowledge-based IDS apply information about known vulnerabilities and attacks to detect exploitation attempts.