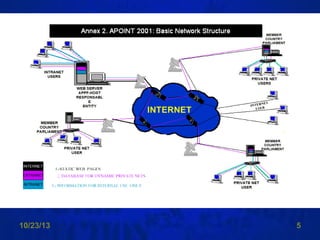
The document discusses network security and outlines various topics that will be covered, including the basics of networks, data packets, virtual private networks, defending against common attacks, and computer espionage. It explains that networks are vulnerable to attacks on data packets and network devices. The basics section defines typical network components like NICs, hubs, switches, and routers, and explains how data is packaged into packets with headers and trailers for transmission between devices. Port scanning and vulnerability scanning tools are also introduced.