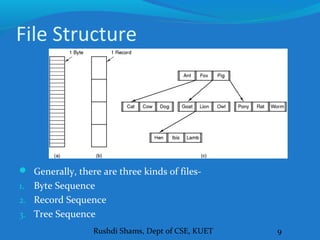
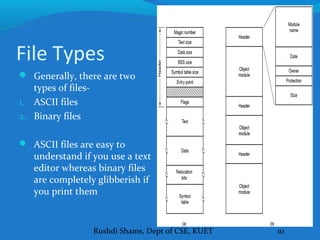
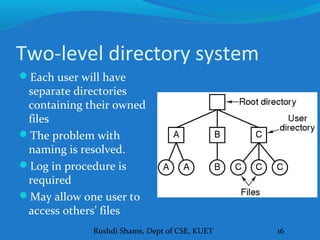
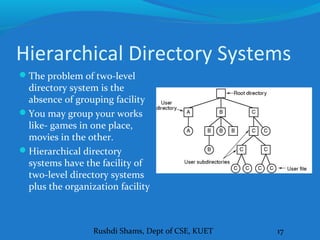
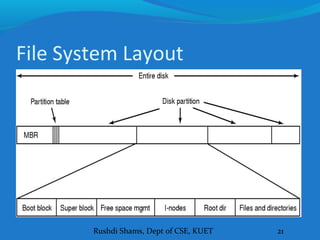
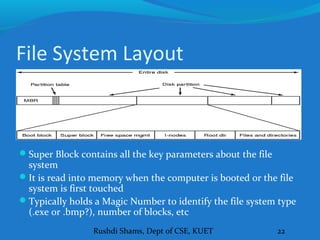
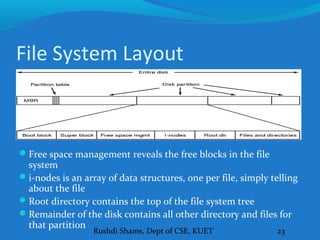
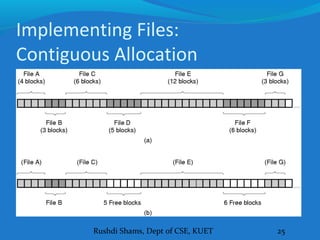
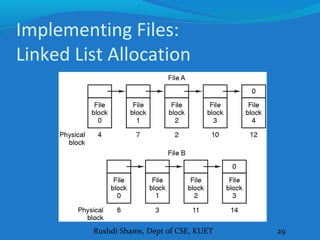
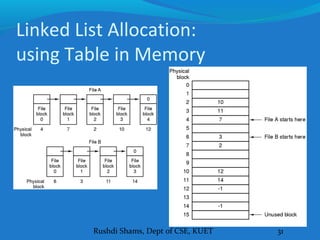
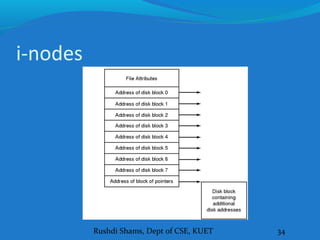
This document discusses file systems and how they are implemented in operating systems. It introduces the need for file systems due to limitations in process address spaces. There are three main requirements for long-term information storage: storing large amounts of data, persistence of data, and concurrent access. Files fulfill these requirements through hierarchical directory structures and various allocation methods like contiguous, linked lists, and inode-based systems. The document provides examples of these allocation techniques and how they map files to disk blocks.