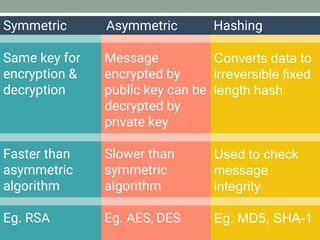
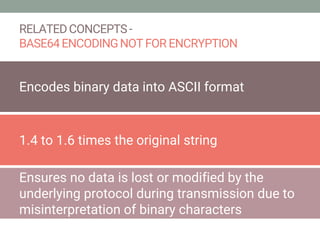
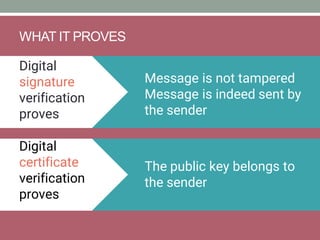
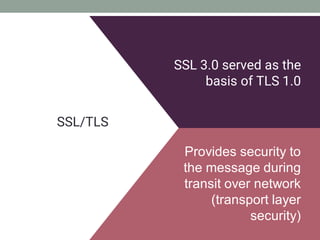
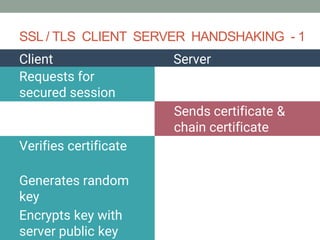
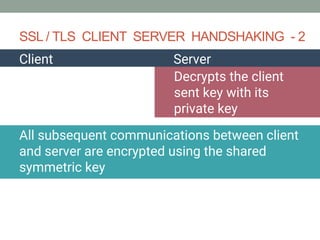
The document explains how SSL/TLS works, detailing encryption algorithms, digital certificates, and the role of certificate authorities in ensuring secure communications. It outlines the processes for creating and verifying digital signatures, which validate the integrity and authenticity of messages. The document further describes the client-server handshake in SSL/TLS, emphasizing the exchange of certificates and the establishment of shared symmetric keys for secure data transmission.