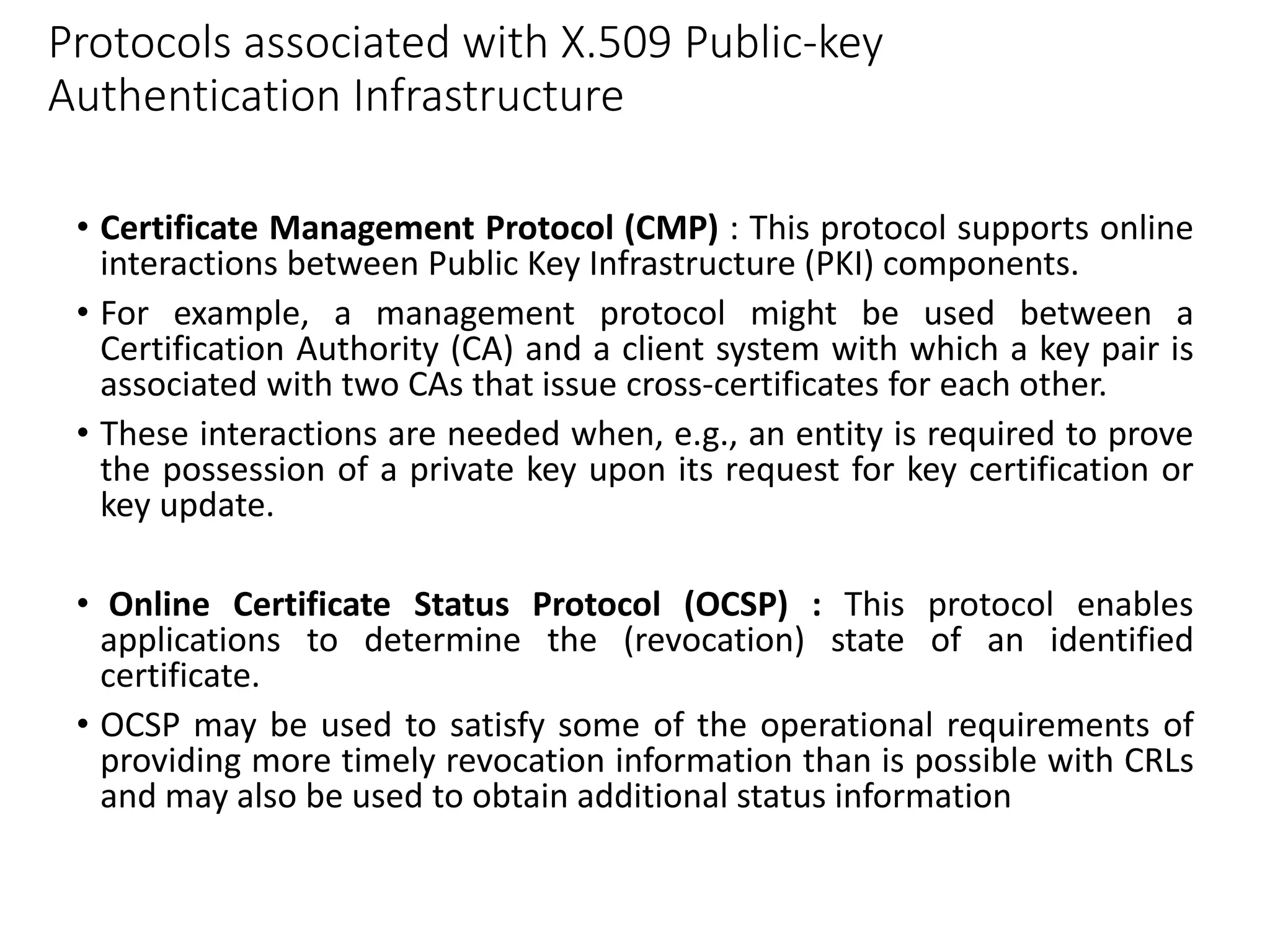
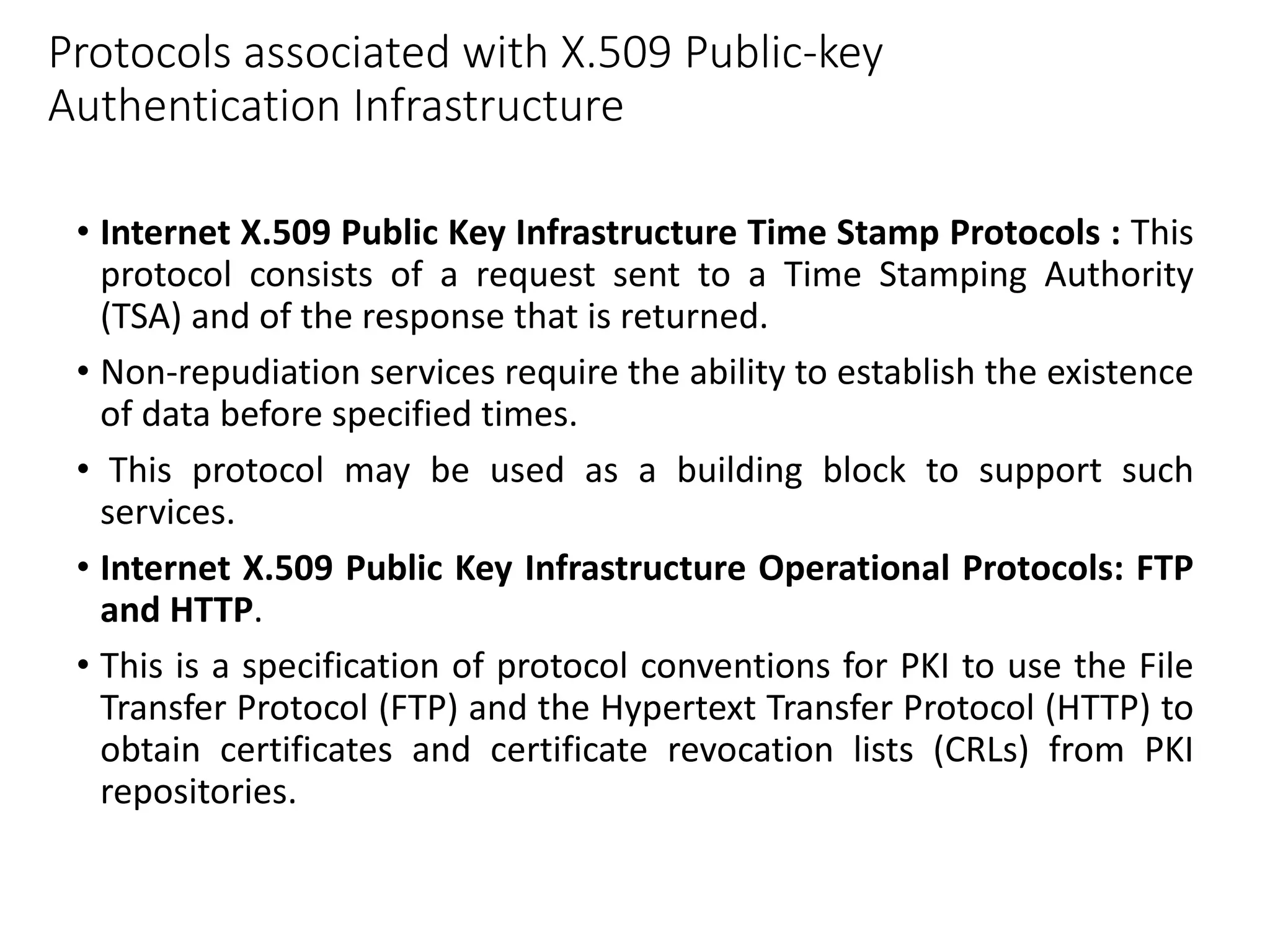
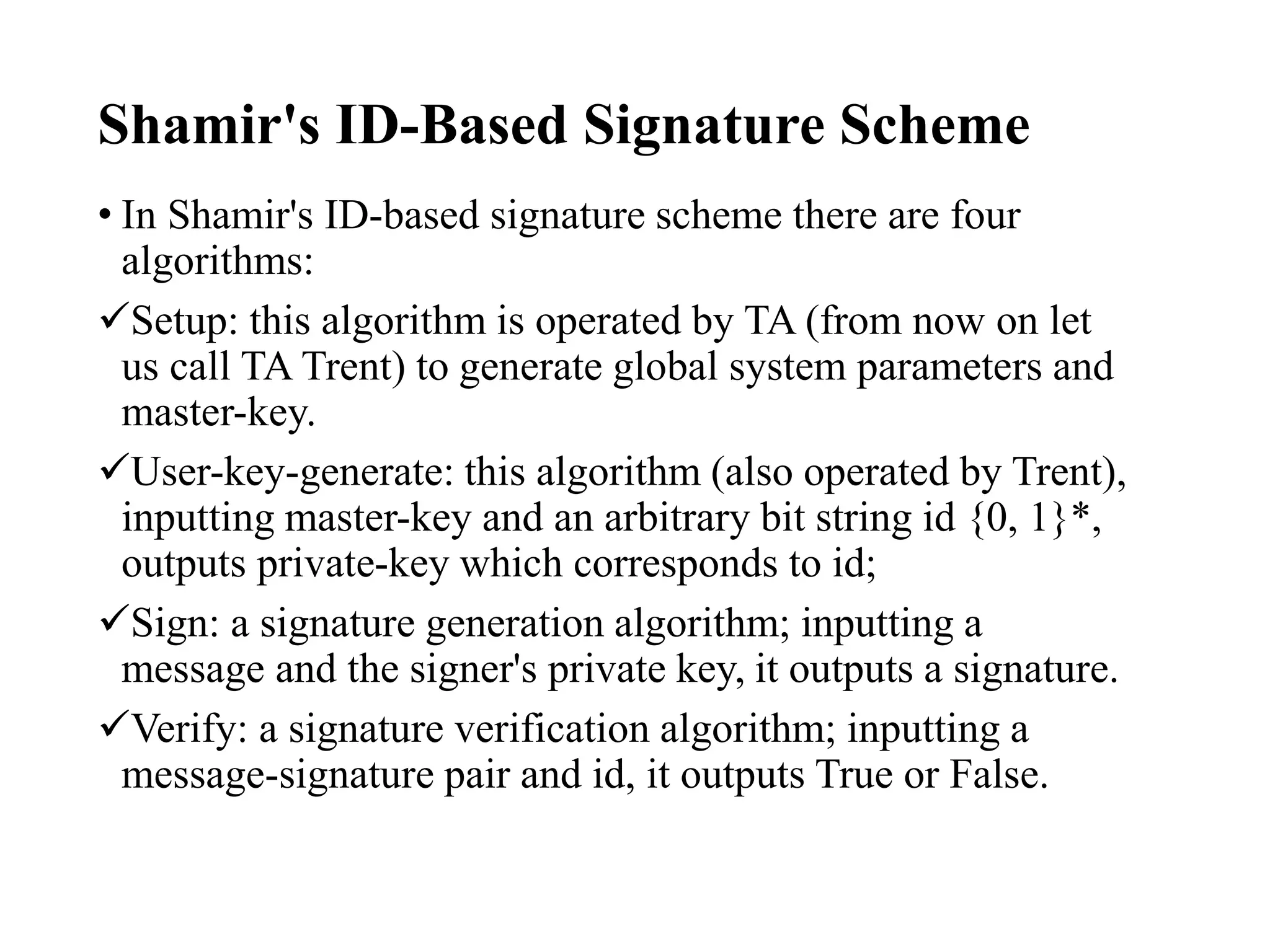
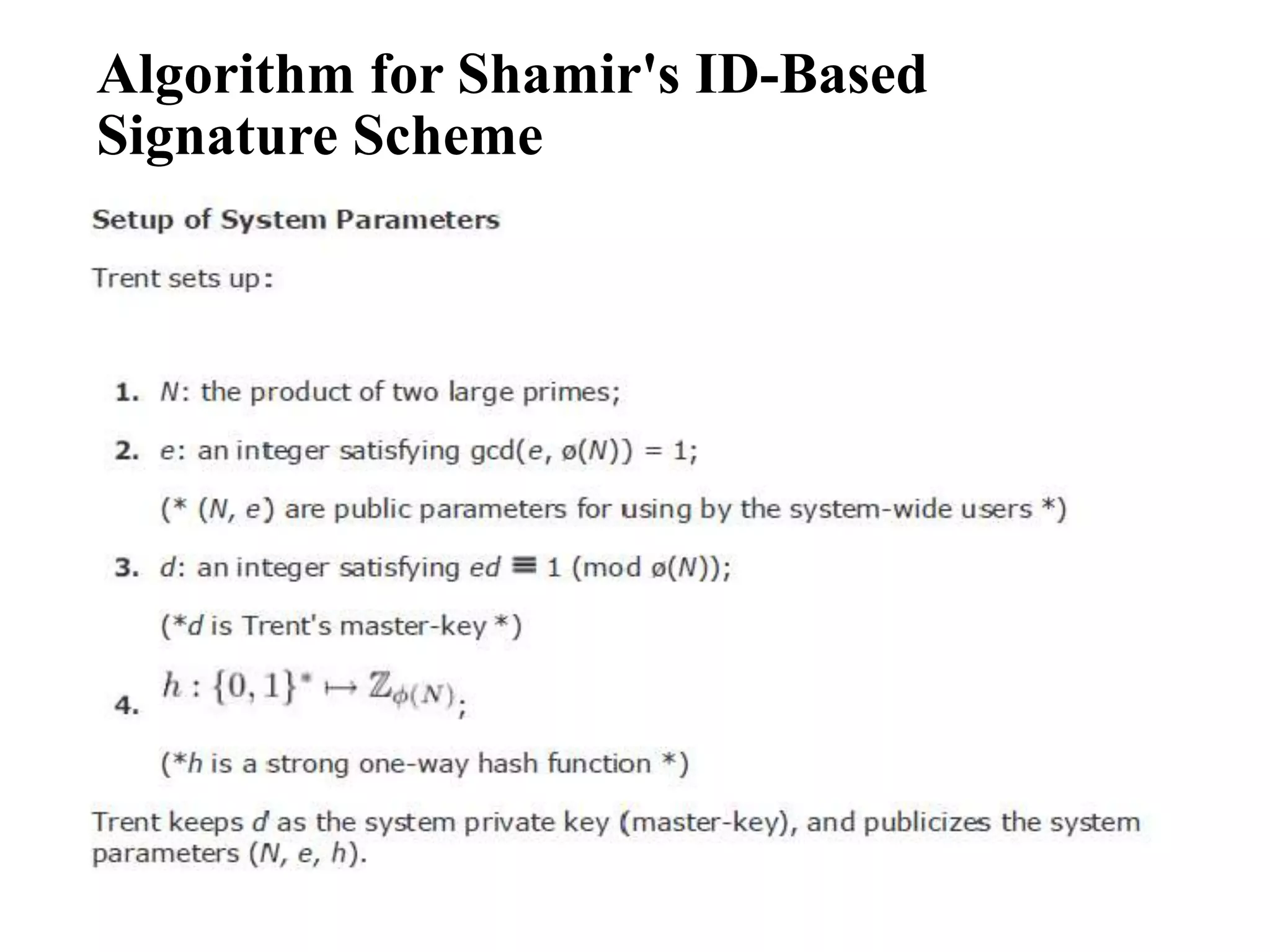
This document discusses public key cryptography and authentication frameworks. It covers:
- Public key cryptography uses key pairs (public and private keys) to authenticate identity and encrypt/sign data.
- Authentication frameworks like X.509 use a certification authority to issue certificates that bind users' identities to their public keys.
- PGP uses a "web of trust" where users can sign each other's keys rather than relying on a central authority.
- ID-based cryptography aims to simplify authentication frameworks by deriving public keys directly from users' identities.









![Framework - X.509 Public-key Certification
Framework
• The standard public-key certification framework, called the X.509 [152]
certification infrastructure, called a directory information tree (DIT).
• In such a tree hierarchy, each node represents a principal whose public-
key certificate is issued by its immediate parent node.
• The leaf nodes are end-user principals.
• The non-leaf nodes are CAs at various levels and domains
• Each of these domains has many sub-domains, e.g, the education
domain has various university sub-domains.
• The root node is called the root CA which is a well-known principal in
the whole system.
• The root CA should certify its own public key.
• Two end-user principals can establish a secure communication channel
by finding upward in the DIT a CA who is the nearest common ancestor
node of them.](https://image.slidesharecdn.com/unit4partii-authenticationframeworkforpkc-230314094029-c969716e/75/Unit-4-Part-II-Authentication-Framework-for-PKC-pptx-10-2048.jpg)