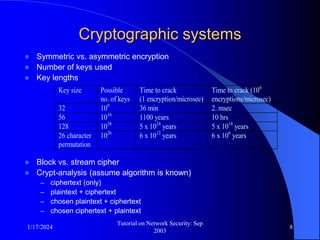
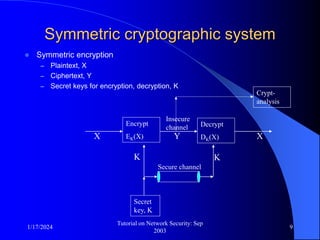
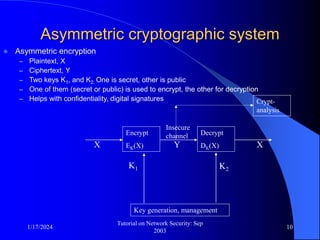
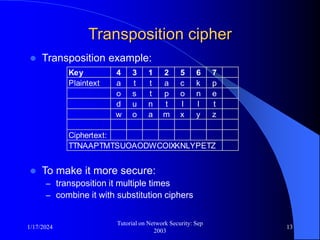
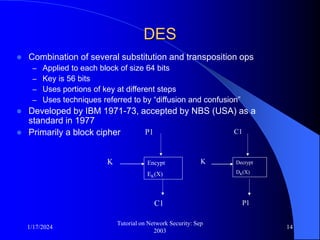
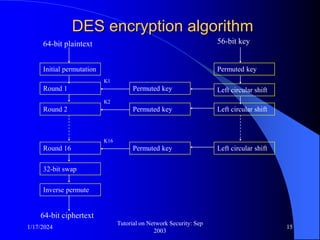
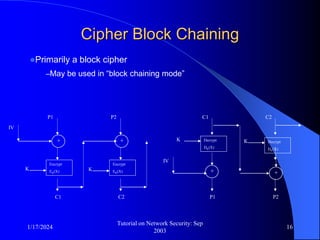
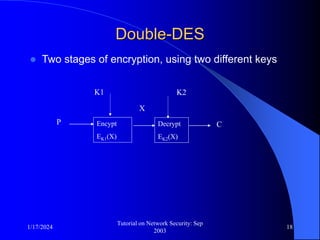
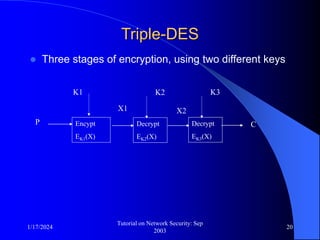
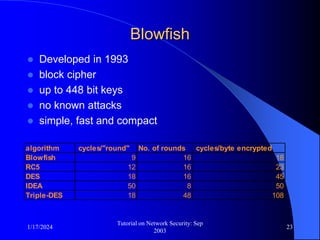
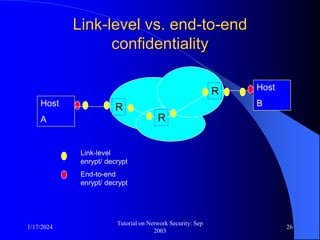
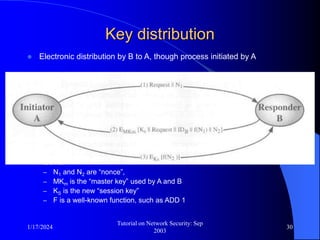
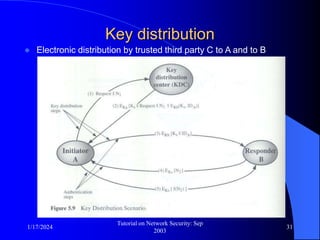
This document provides an overview of a tutorial on network security given in September 2003. It discusses top-level issues in network security including threats, security services, and mechanisms. It also summarizes symmetric key encryption techniques like DES, AES, and their operating principles. Key distribution is highlighted as a challenge for symmetric key encryption systems.