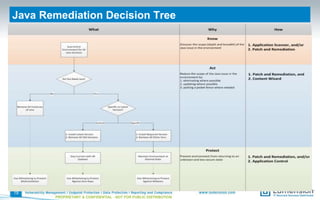
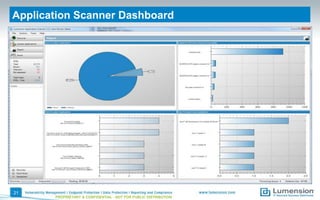
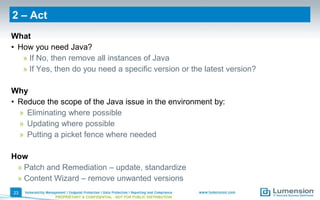
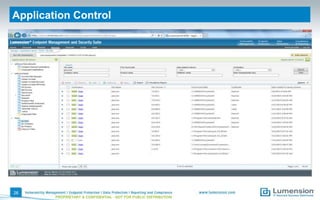
The document outlines vulnerabilities associated with Java software and provides strategies for assessment, disabling, hardening, filtering, and patching Java installations. Key points include the importance of identifying installed Java versions, managing security configurations, and utilizing tools for effective patch and remediation. It emphasizes the need for organizations to proactively manage Java risks to maintain security across their environments.















![Patching
Oracle still relies on independent auto-updaters on each endpoint
Install by MSI
Download and run the offline installer, but do not complete it. Look in
%userprofile%appdatalocallowsunjava.
Open the folder jre<update number> and copy the msi and cab files there
to your server share where you deploy your msis. Deploy with group
policy as per normal.
Silent install from script
<jre>.exe [/s] [INSTALLDIR=<drive>:<JRE_install_path>] [STATIC=1]
[WEB_JAVA=0/1] [WEB_JAVA_SECURITY_LEVEL=VH/H/M/L]
http://java.com/en/download/help/silent_install.xml](https://image.slidesharecdn.com/lumension-javafinal-130718163613-phpapp01/85/Java-Insecurity-How-to-Deal-with-the-Constant-Vulnerabilities-16-320.jpg)