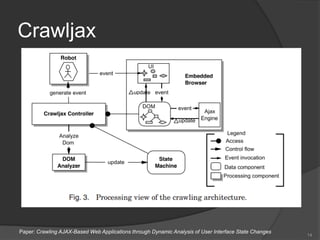
Roberto Suggi Liverani presents a talk on automating web application security testing, highlighting tools like Burp Suite, Selenium, and Crawljax for dynamic analysis of AJAX applications. He introduces Burp CSJ, an extension that integrates these tools for enhanced testing capabilities and discusses various automation techniques to improve vulnerability discovery. The session includes insights from his experiences, emphasizing the importance of thorough preparation and strategic testing to uncover critical security bugs.