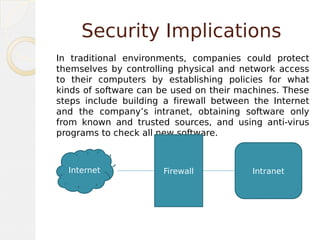
This document discusses security features in Java. It covers applets, security implications of applets running locally, the sandbox model, bytecode verification, class loading, the security manager, language features that enhance security, and signed JAR files. The key points are that applets are restricted to prevent harm, the bytecode is verified before execution, and digital signatures allow verification of untrusted code sources.