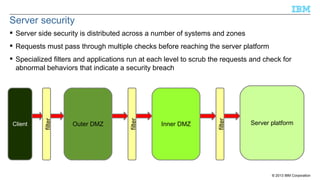
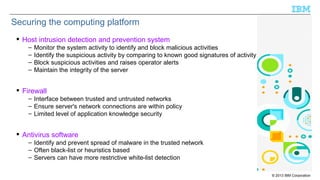
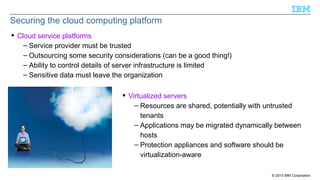
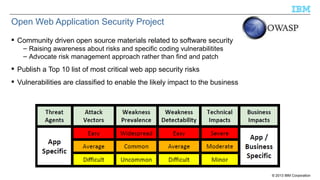
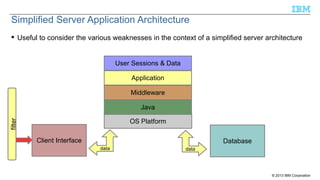
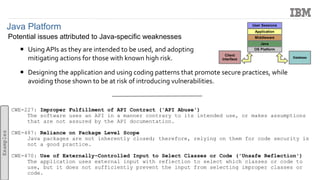
The document discusses the importance of securing Java applications on server platforms, addressing client-side versus server-side computing, and detailing various security measures such as firewalls, intrusion detection systems, and secure coding practices. It emphasizes a lifecycle approach to application security, including risk assessment, secure engineering practices, and ongoing monitoring for vulnerabilities. Additionally, it outlines common vulnerabilities and resources for improving server-side Java security, such as the Common Vulnerabilities and Exposures (CVE) and the Open Web Application Security Project (OWASP).