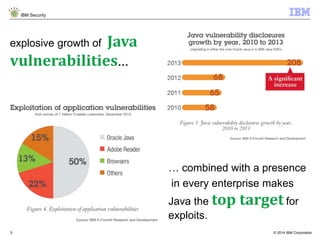
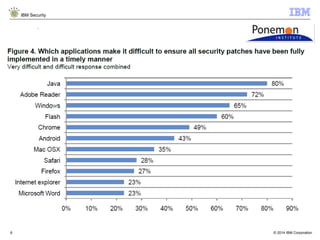
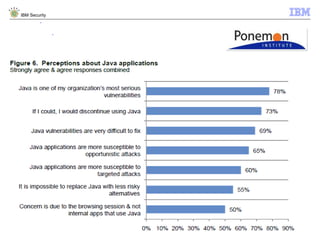
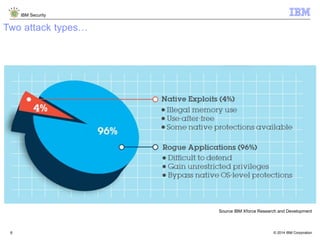
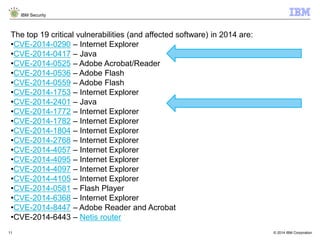
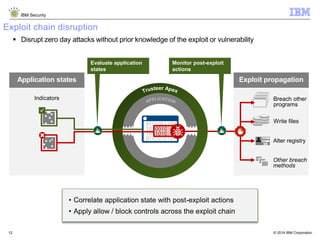
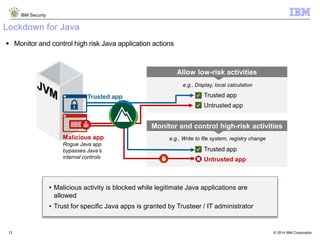
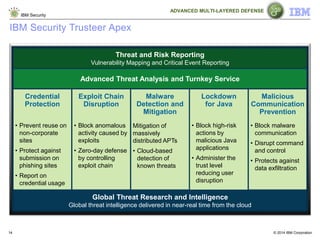
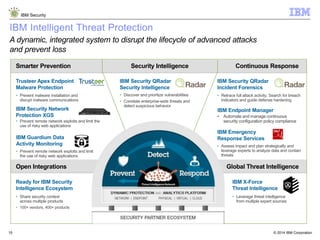
The document discusses how Java applications are frequently targeted by cybercriminals for malware attacks. It notes that Java's wide usage on desktops and mobile devices, combined with vulnerabilities, make it a top target for exploits. The document outlines how malware can be hidden in Java archives (JAR files) and details two common attack types using Java-based malware. It recommends defense solutions like IBM Security Trusteer Apex to monitor and control risky Java application actions and disrupt exploit chains.