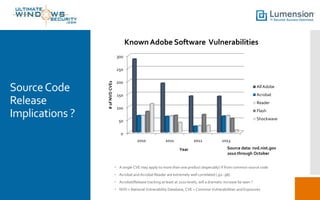
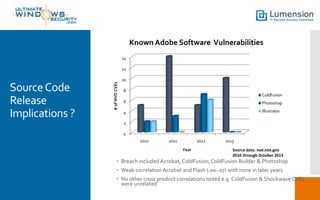
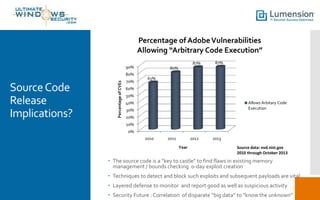
Adobe experienced a significant security breach affecting 38 million users, compromising sensitive information, including source code for products like Acrobat, Reader, and Photoshop. The breach raises concerns about identity theft, source code integrity, and potential for new exploits. Recommendations for mitigating risks include replacing vulnerable tools, using sandboxes for applications, and enhancing memory protection technologies.