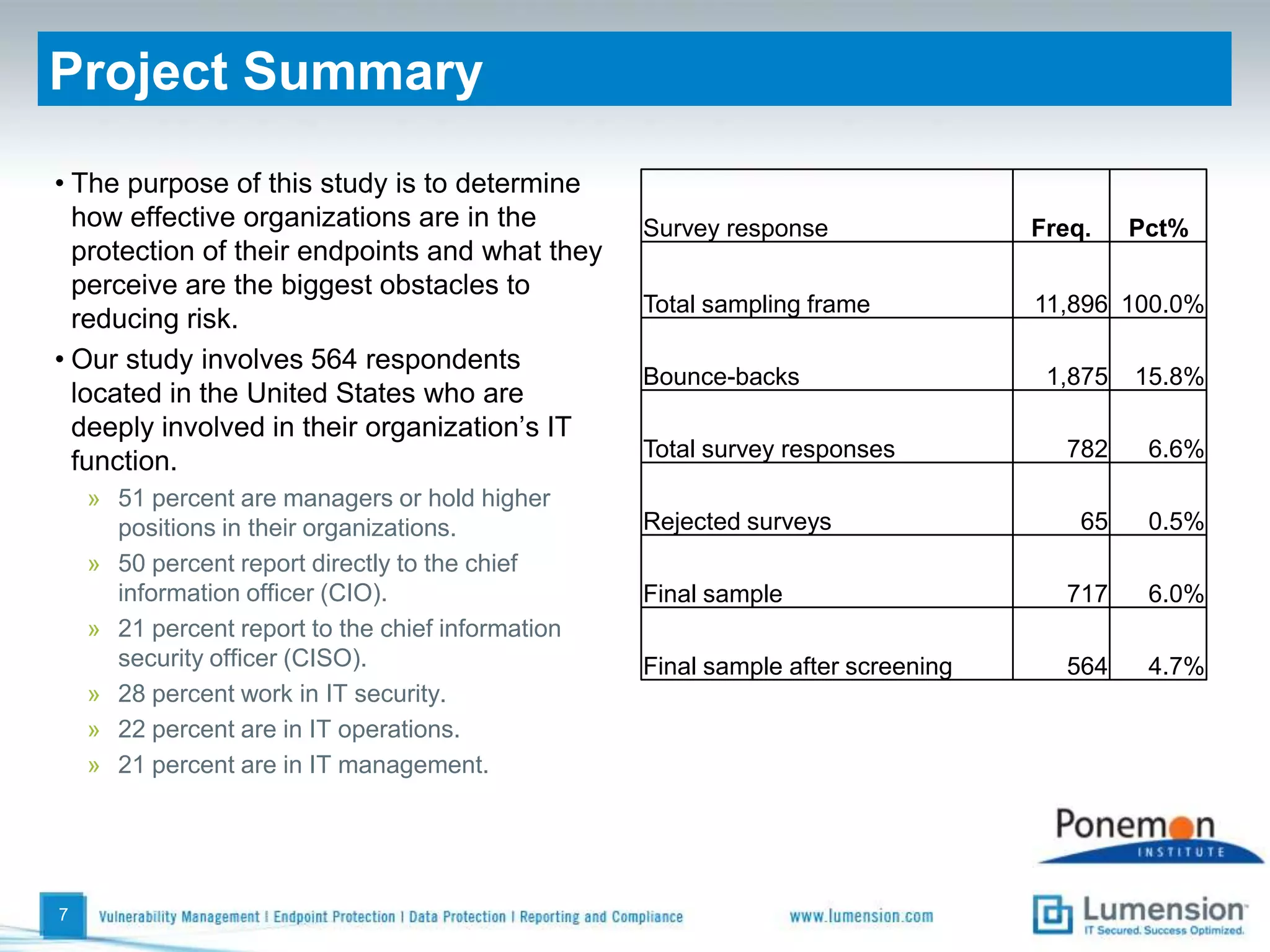
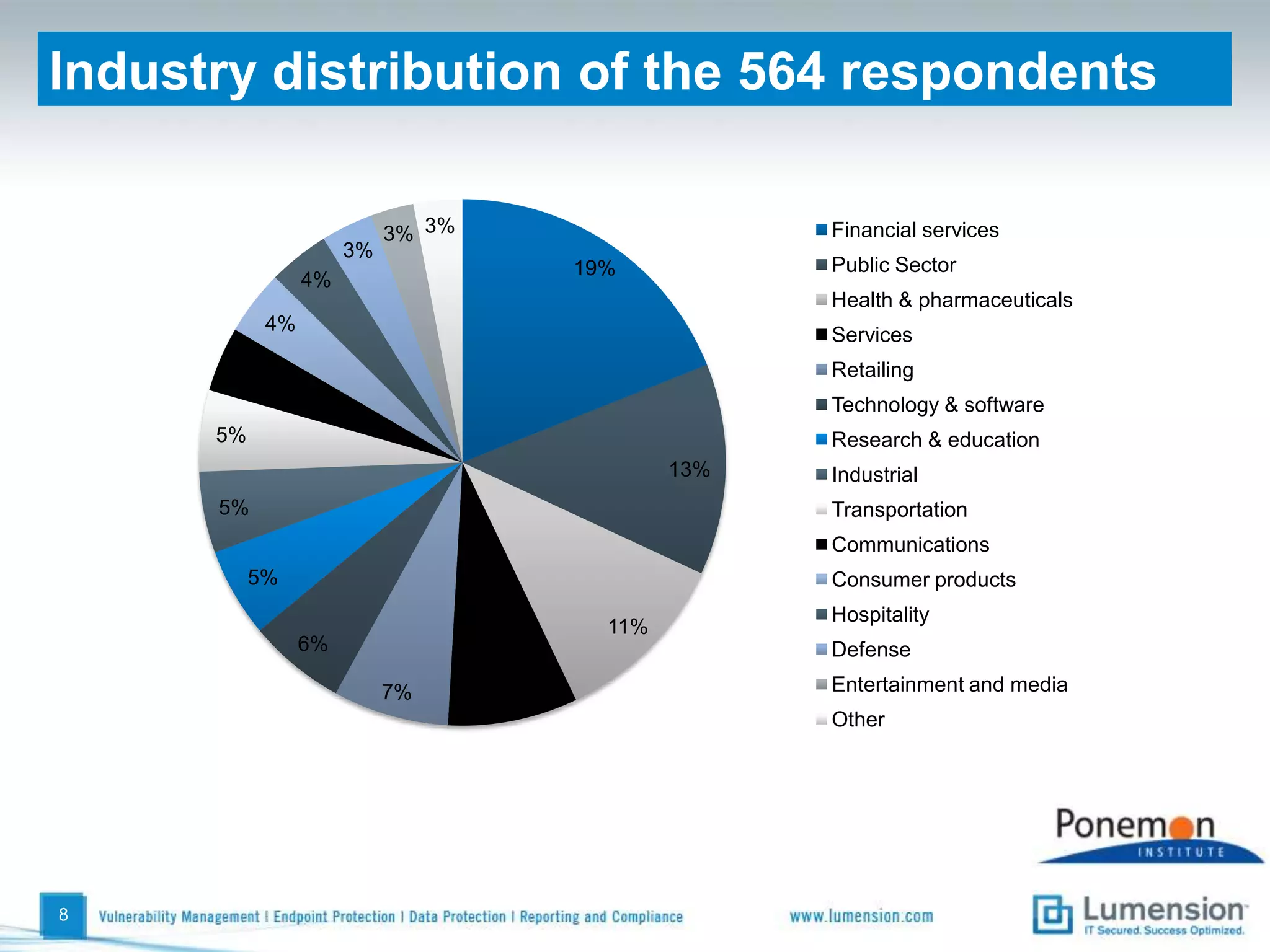
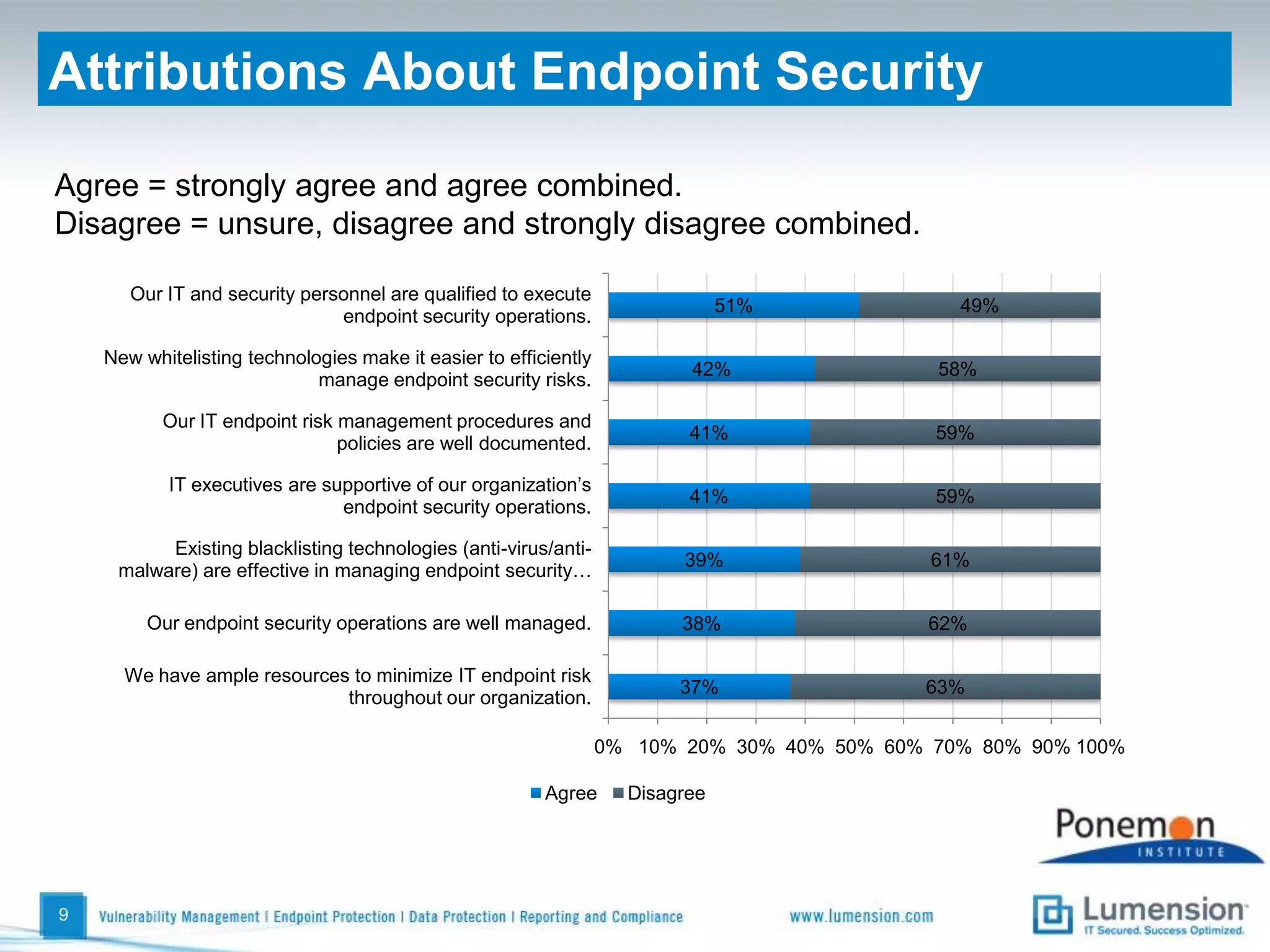
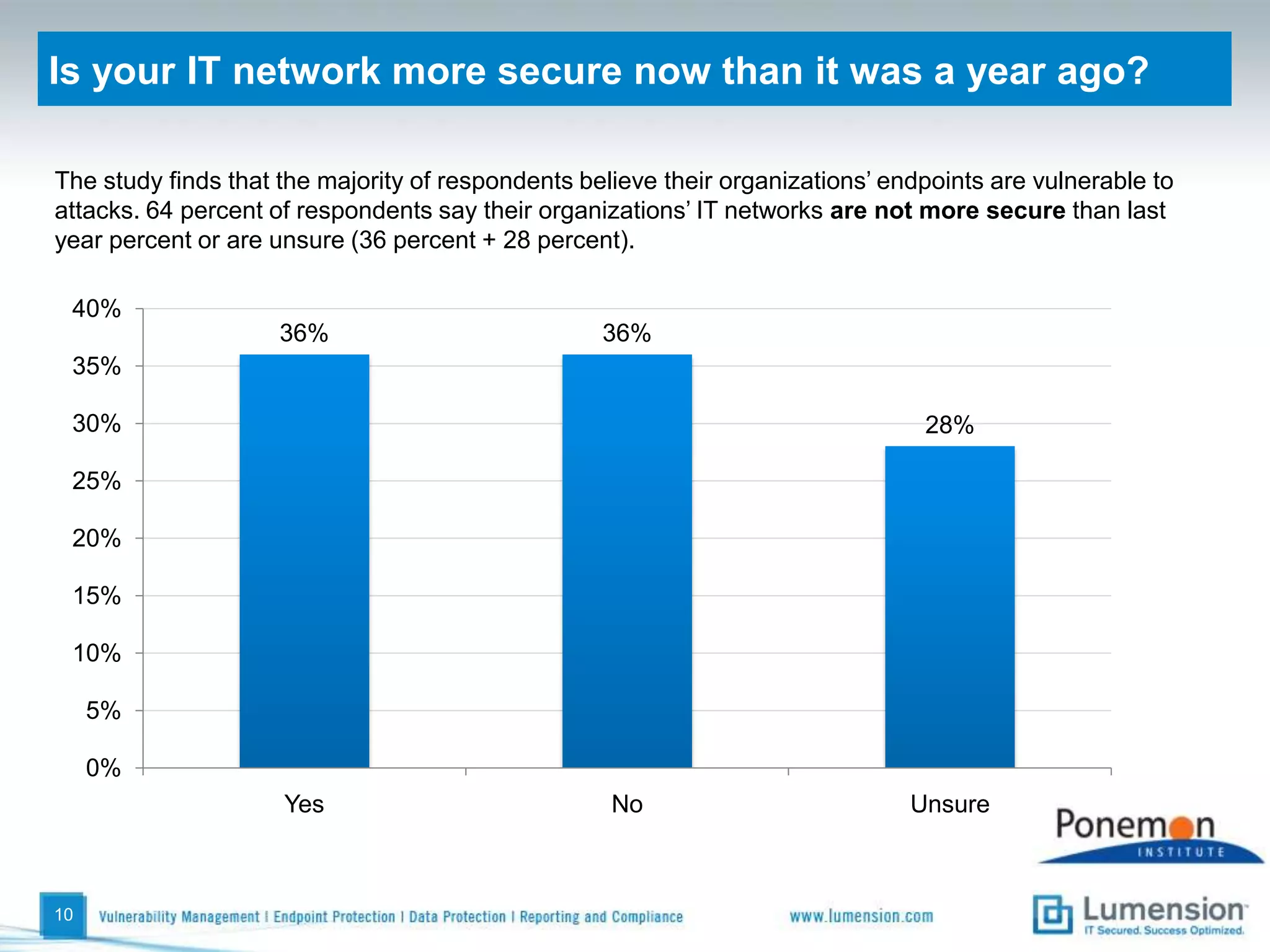
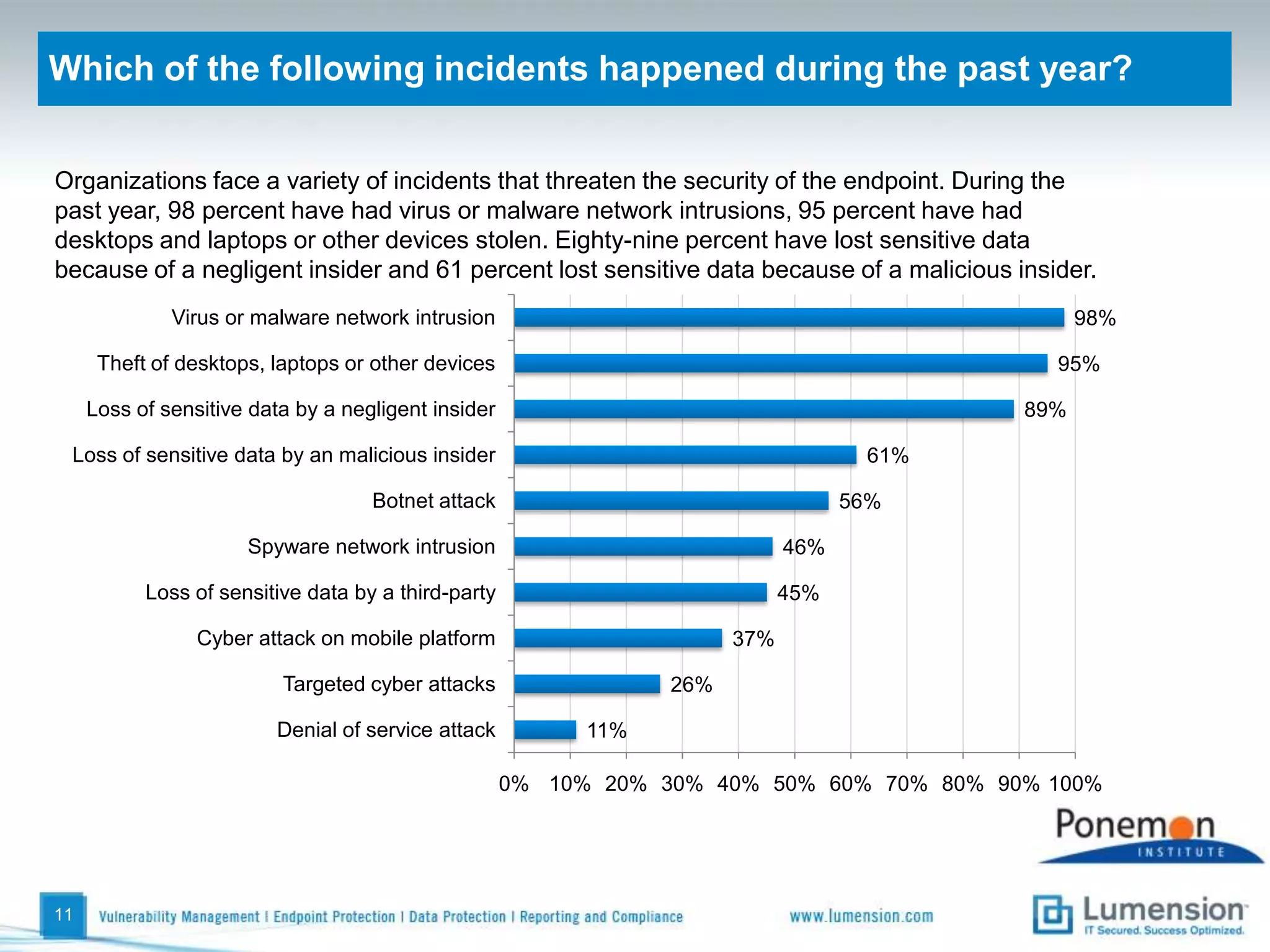
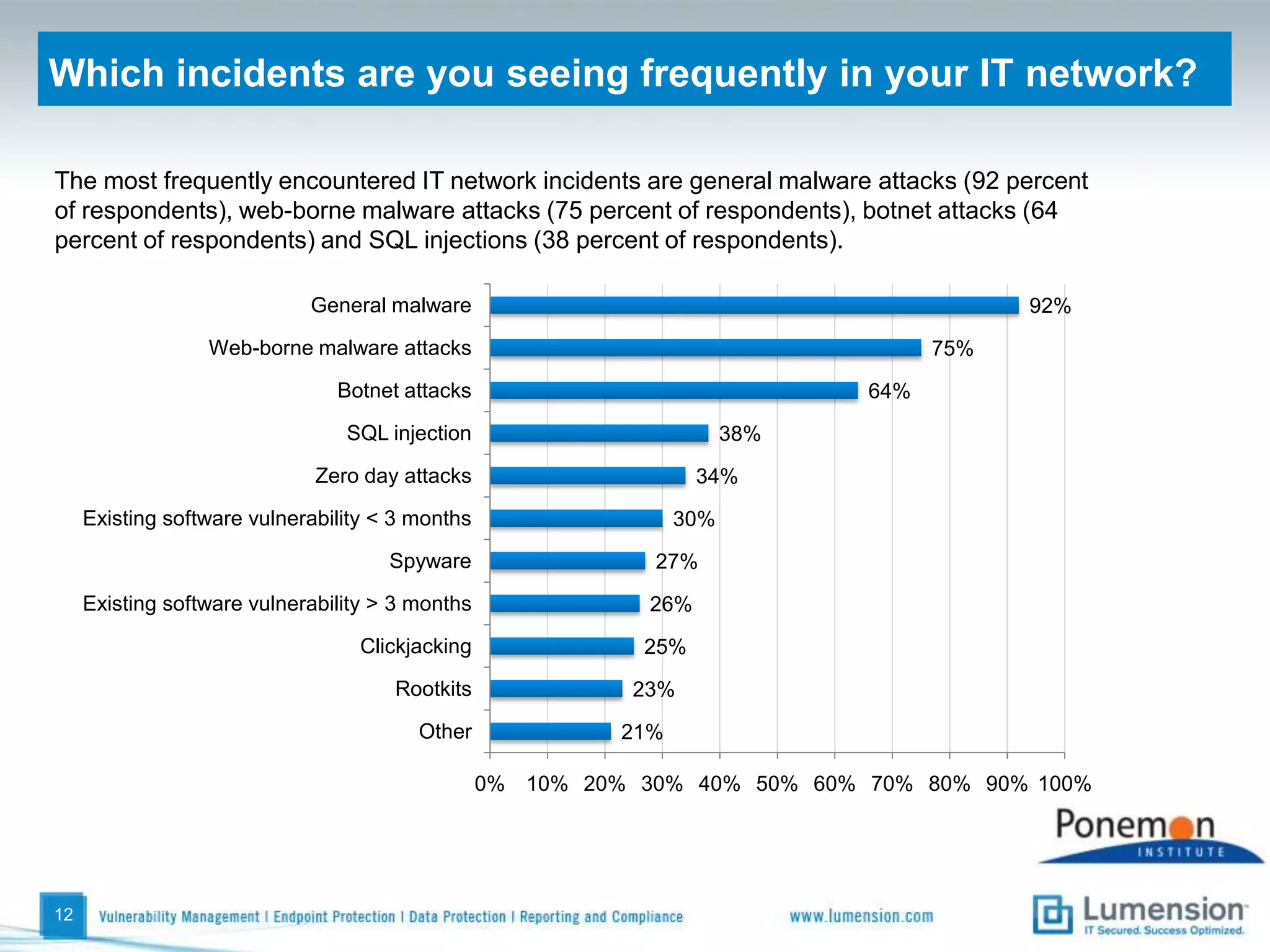
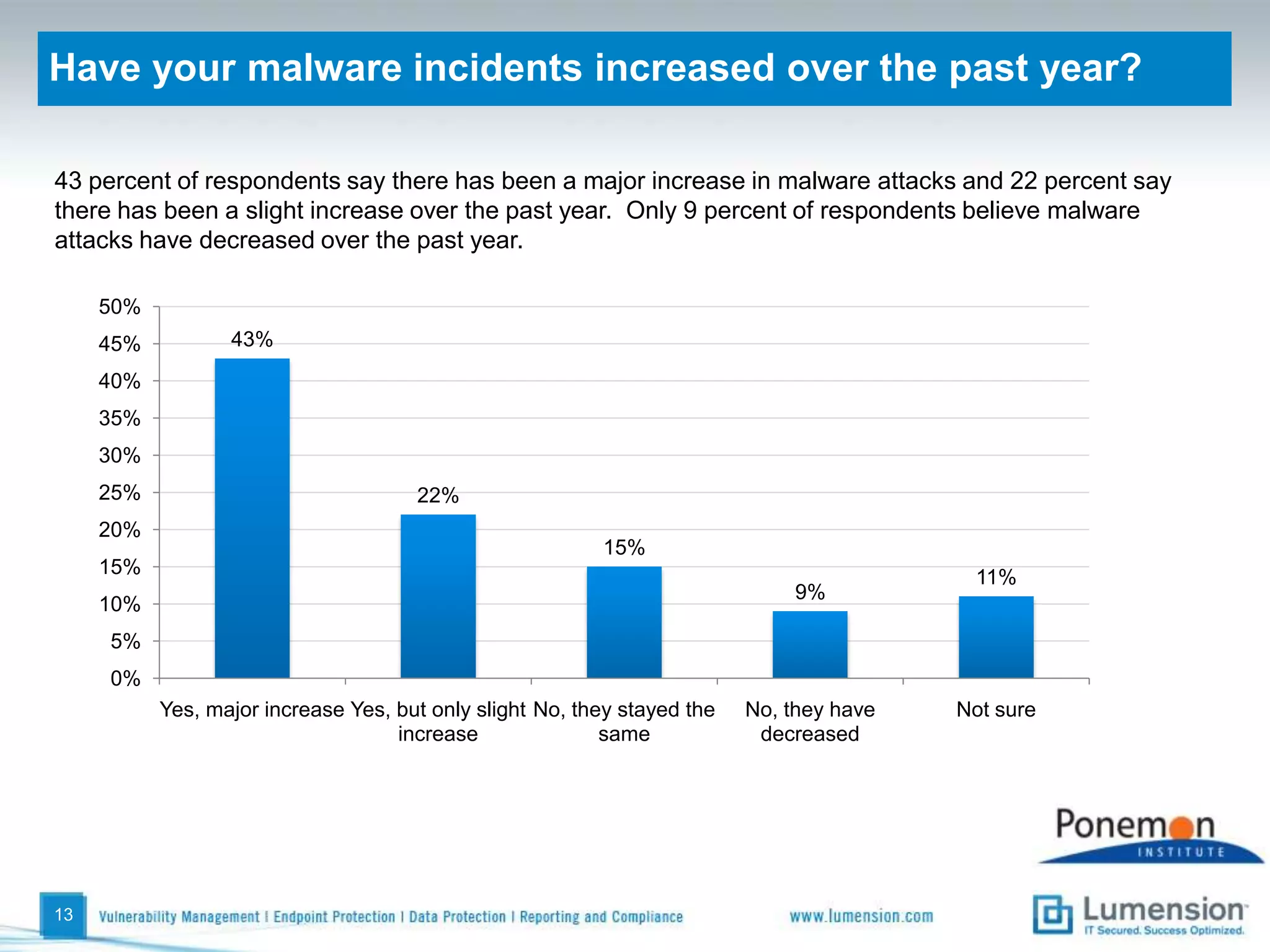
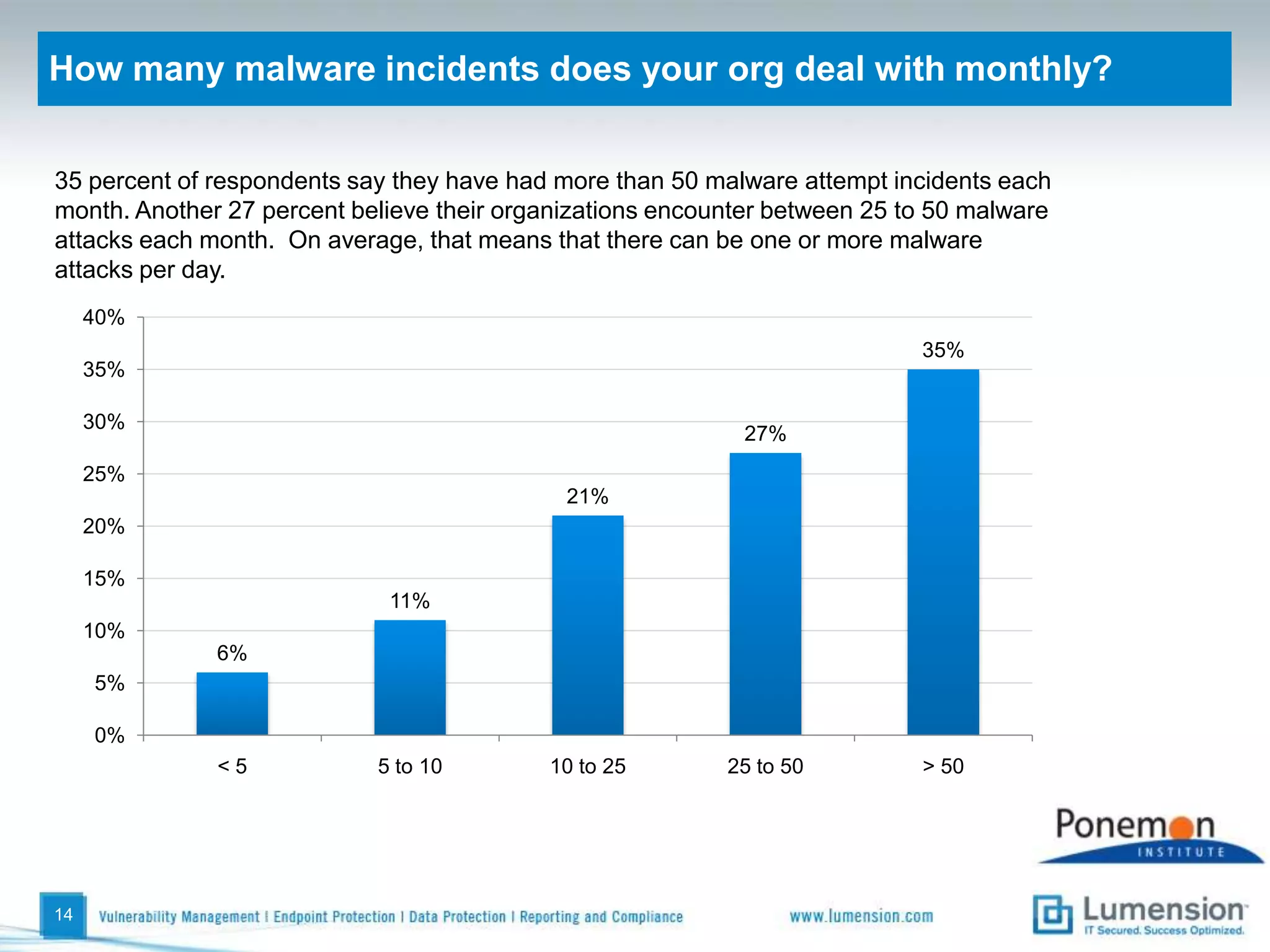
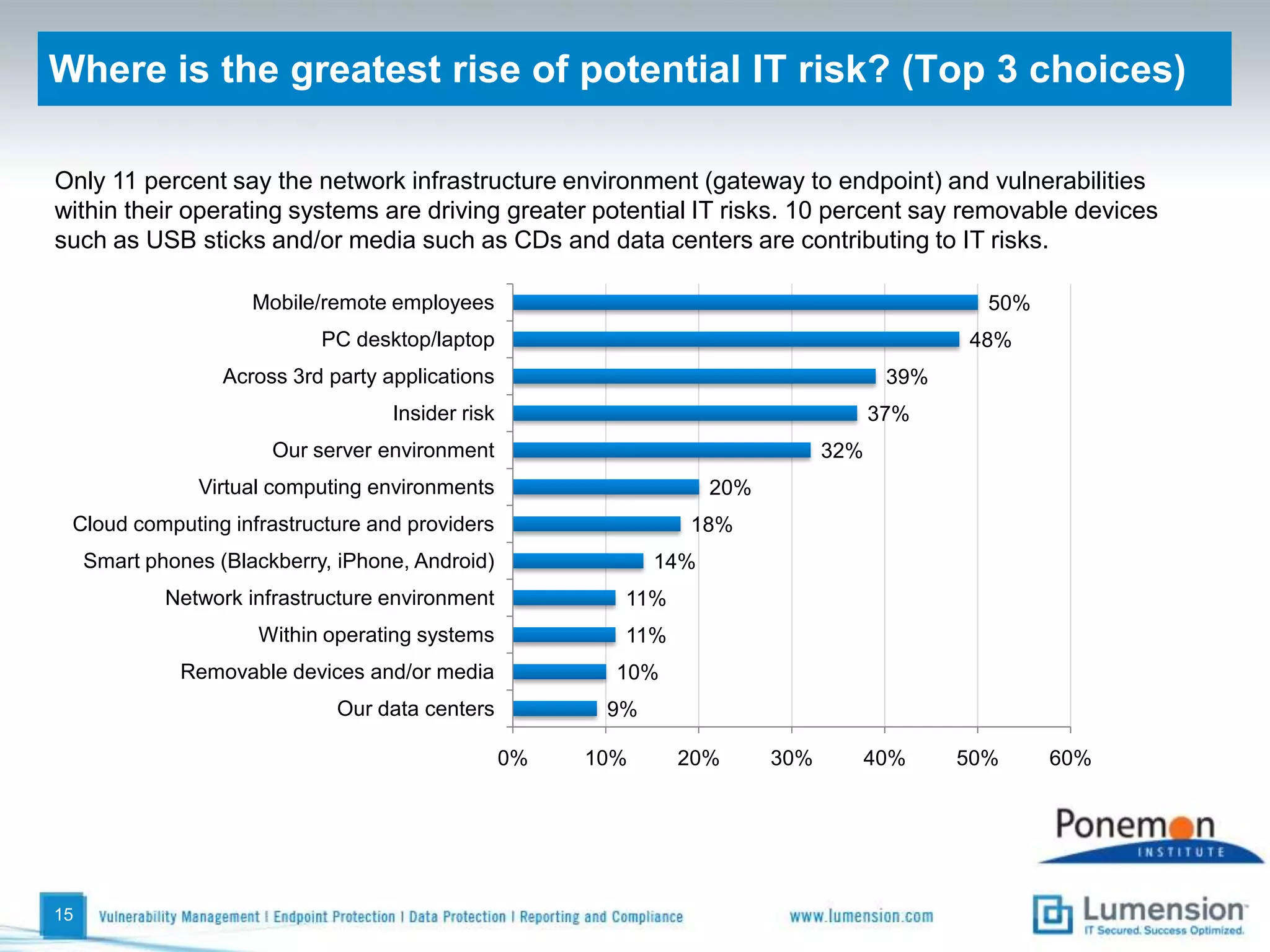
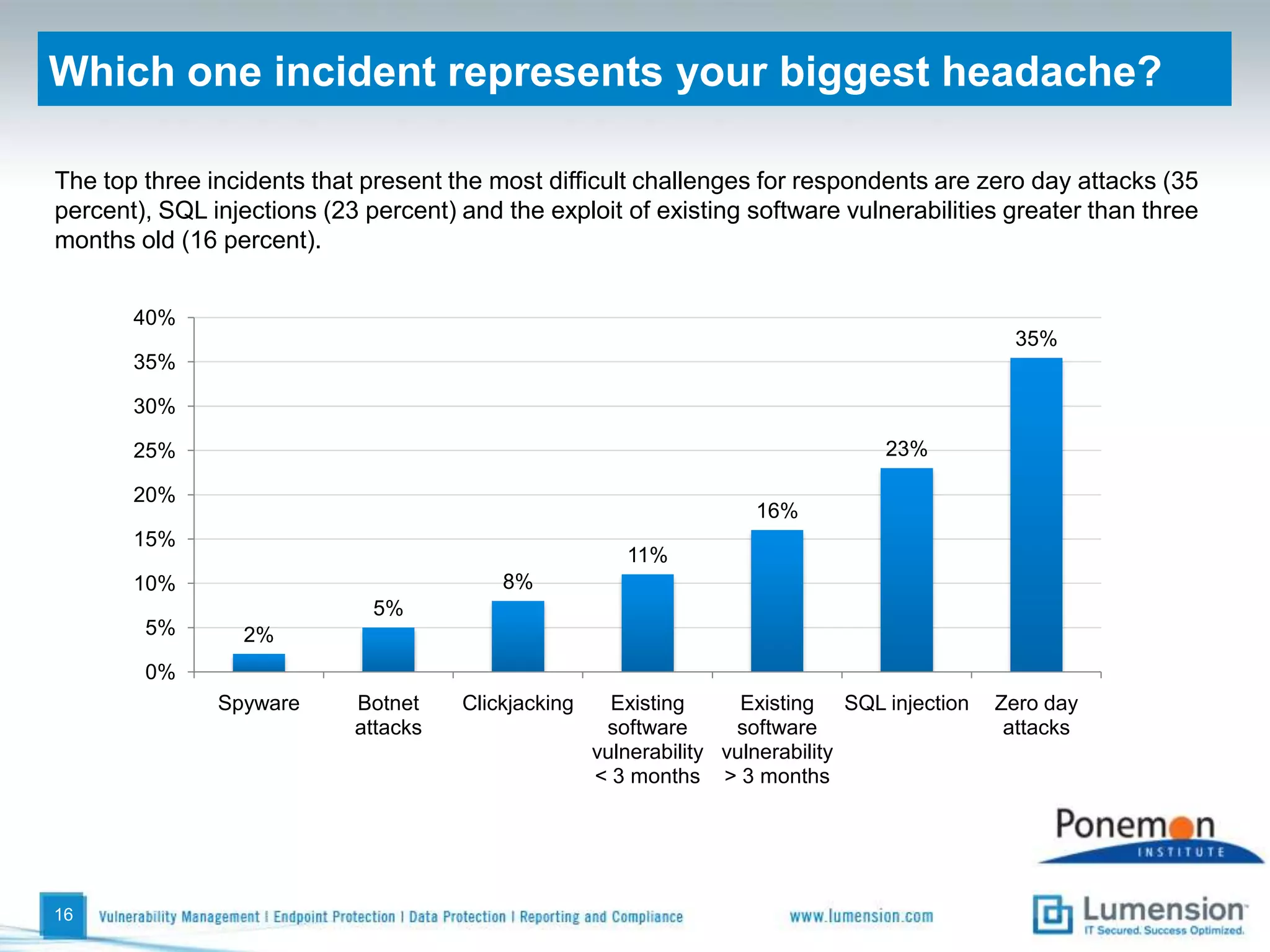
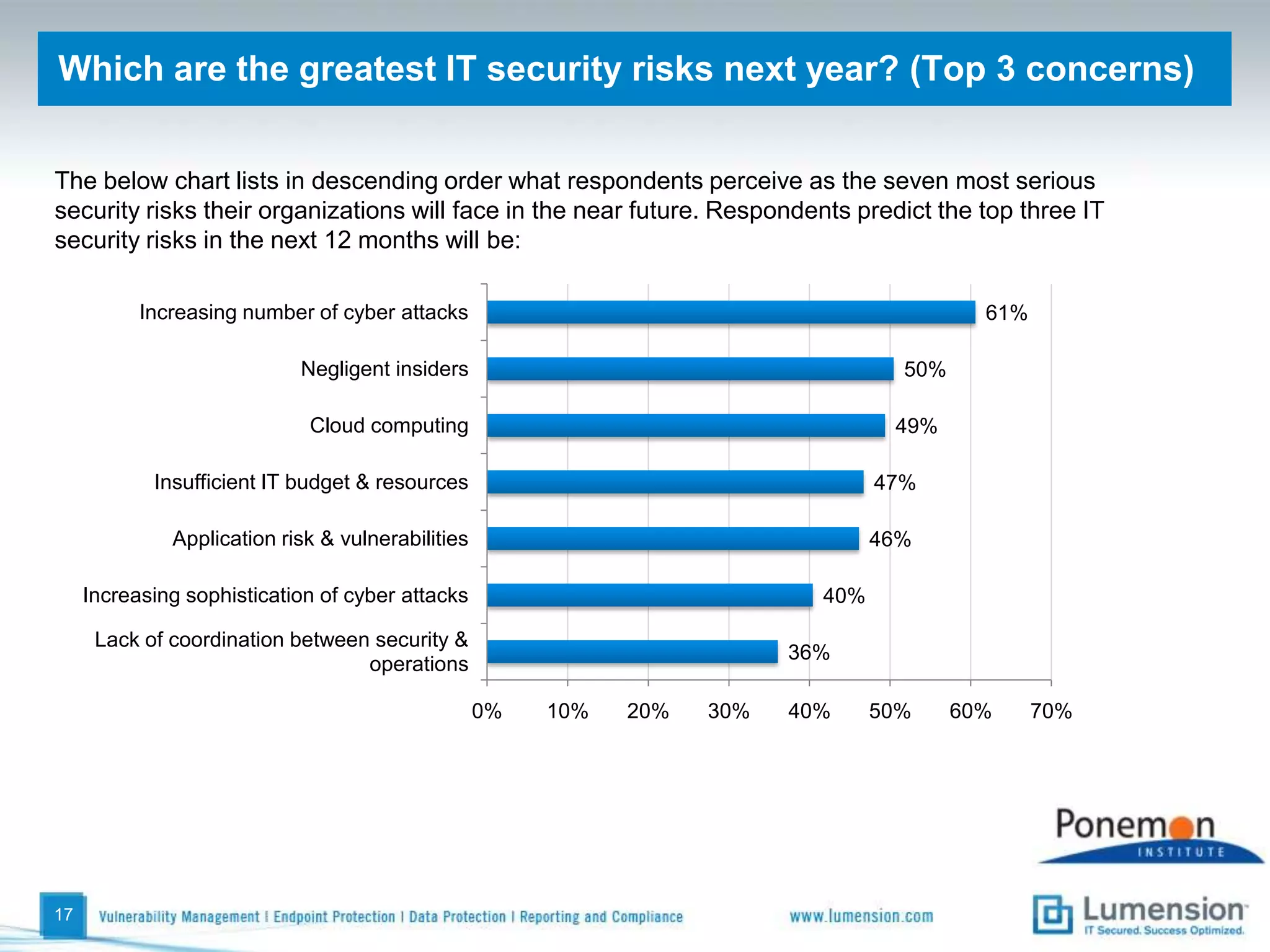
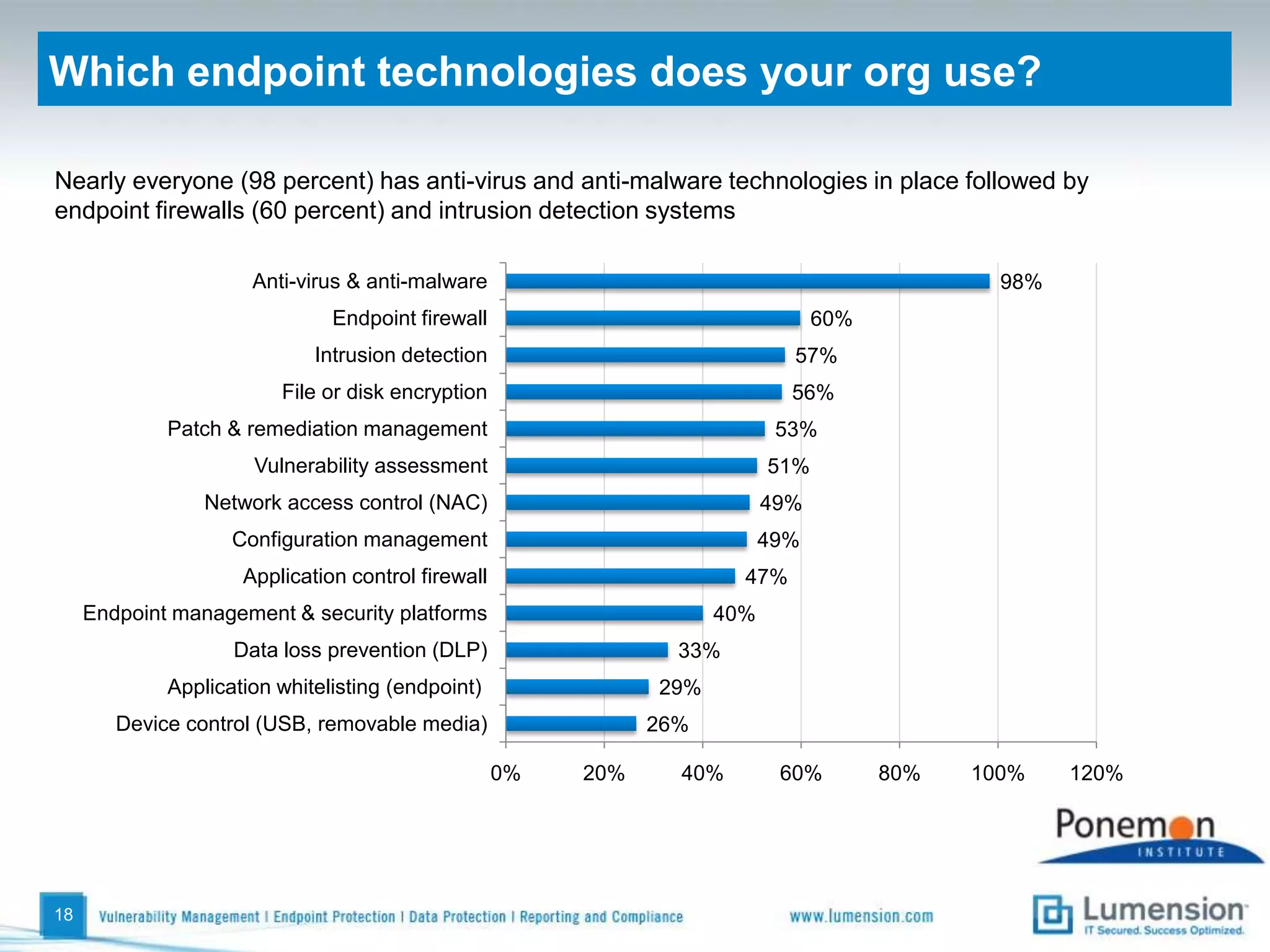
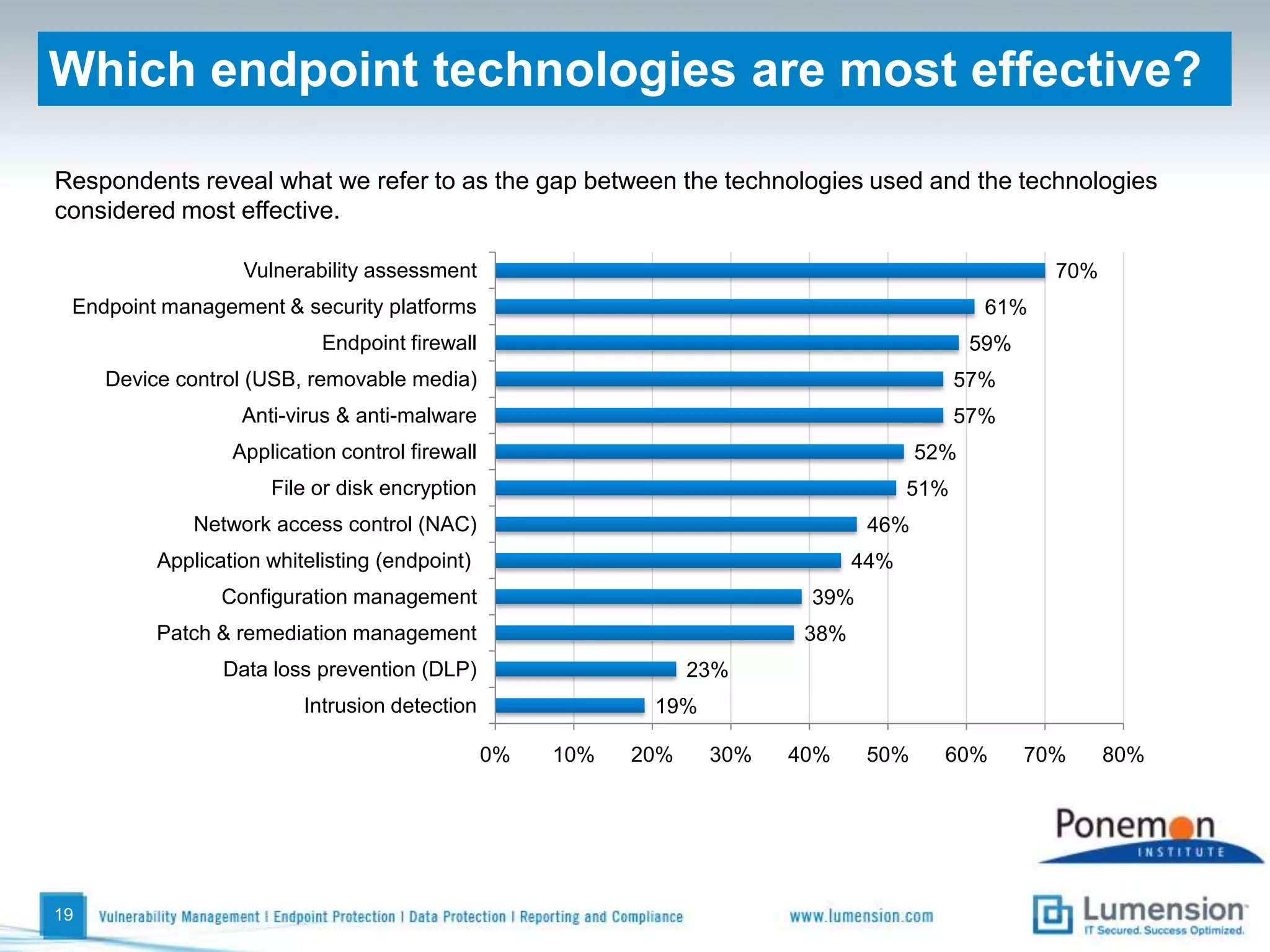
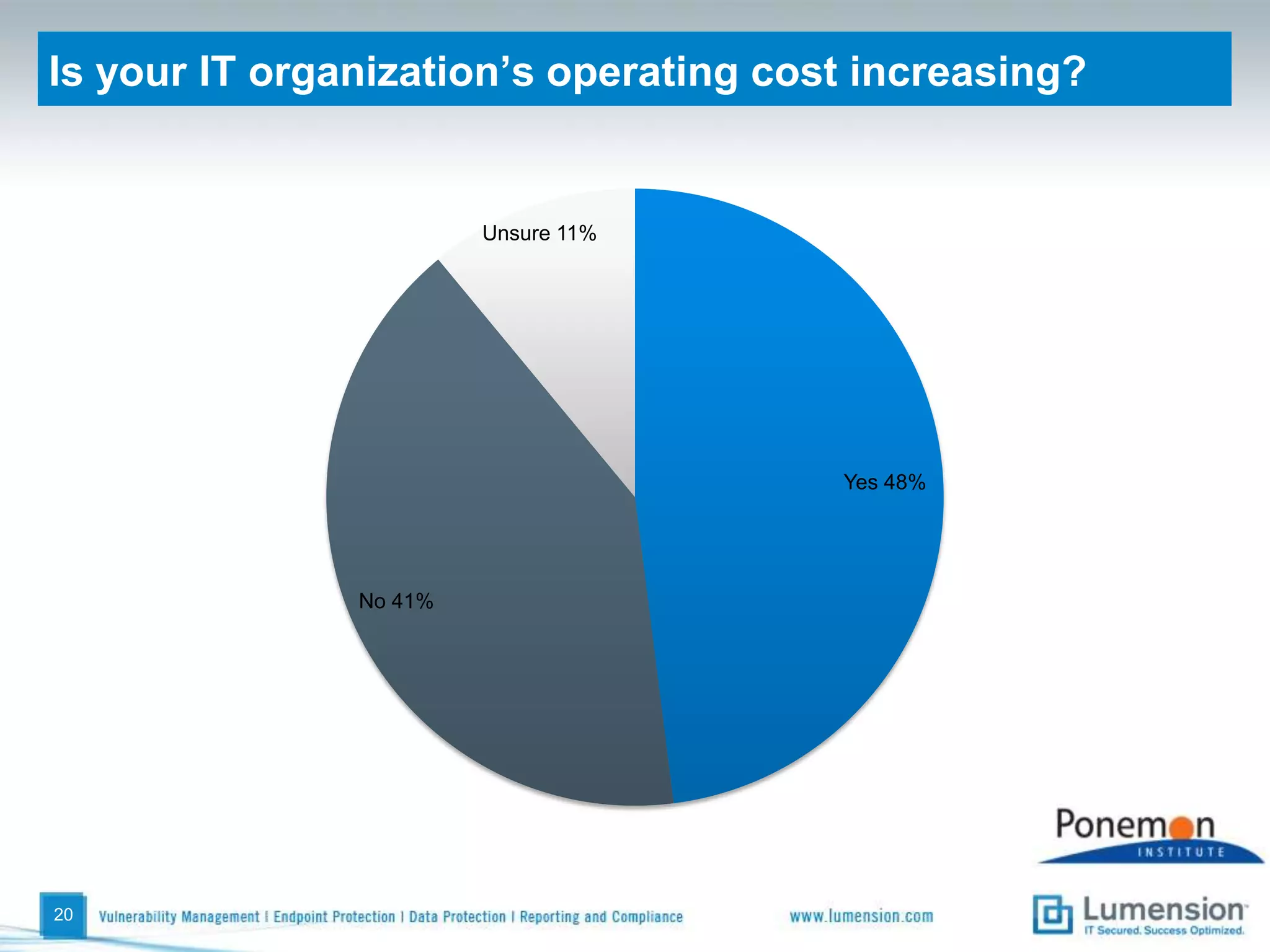
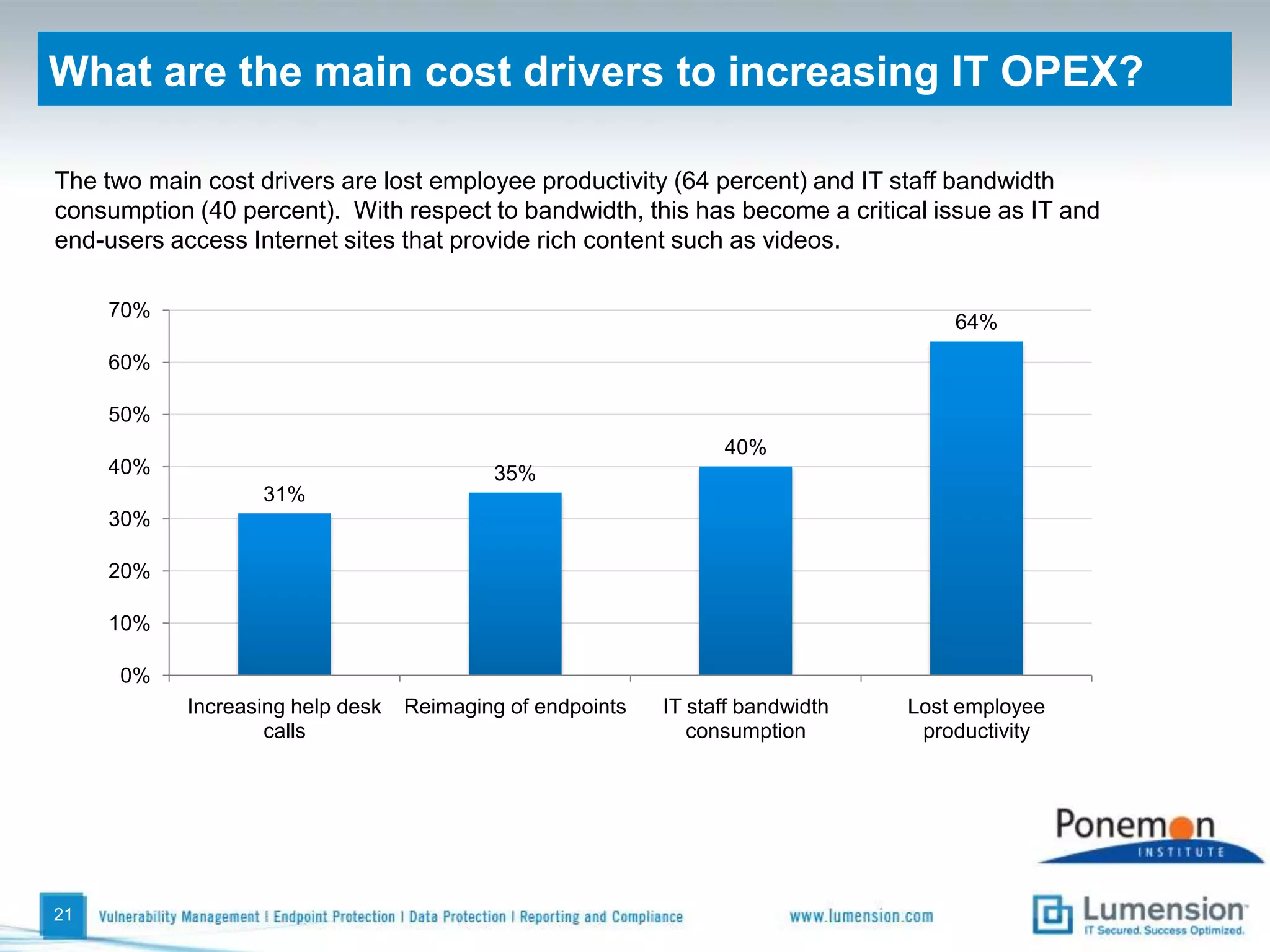
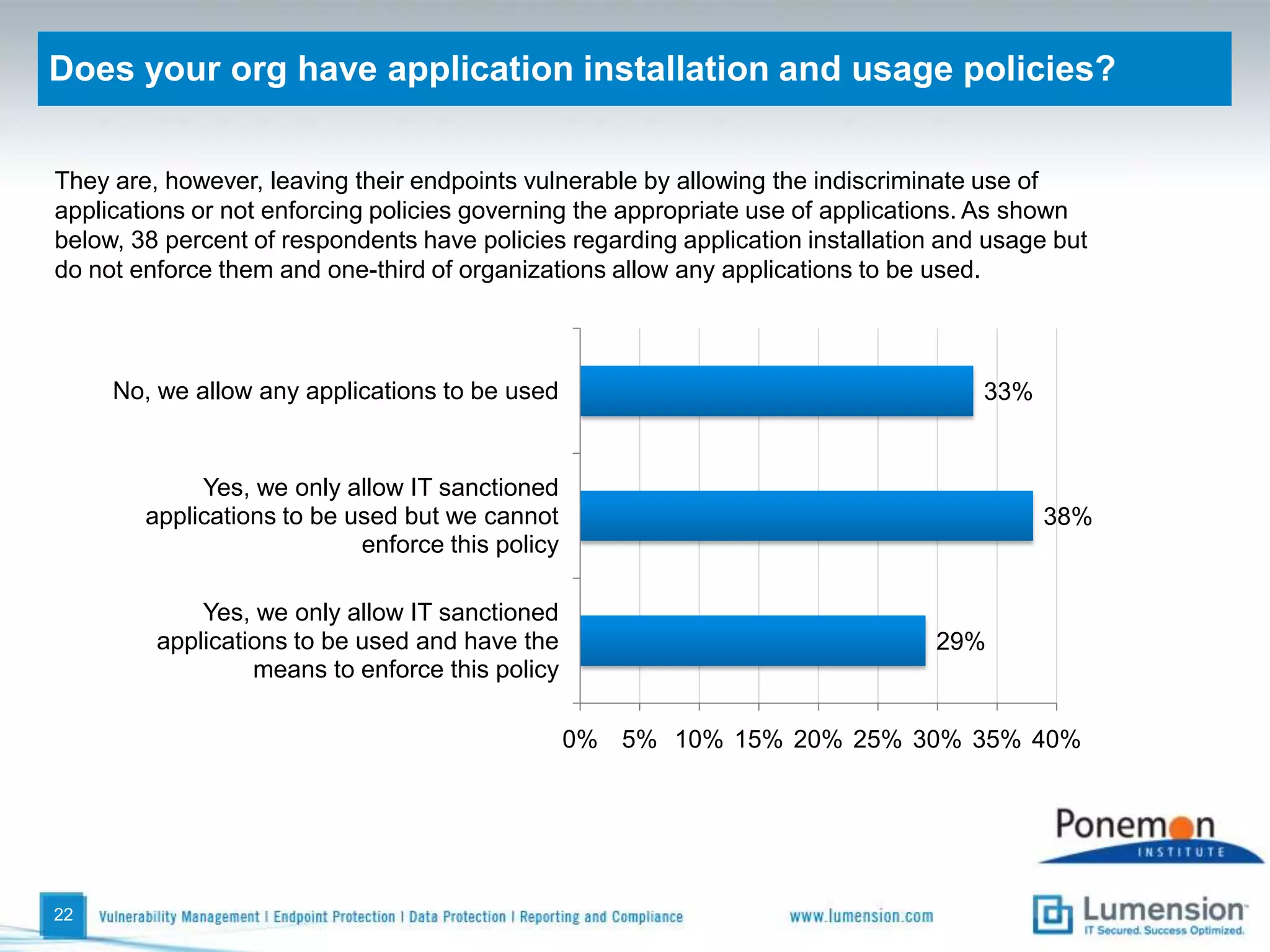
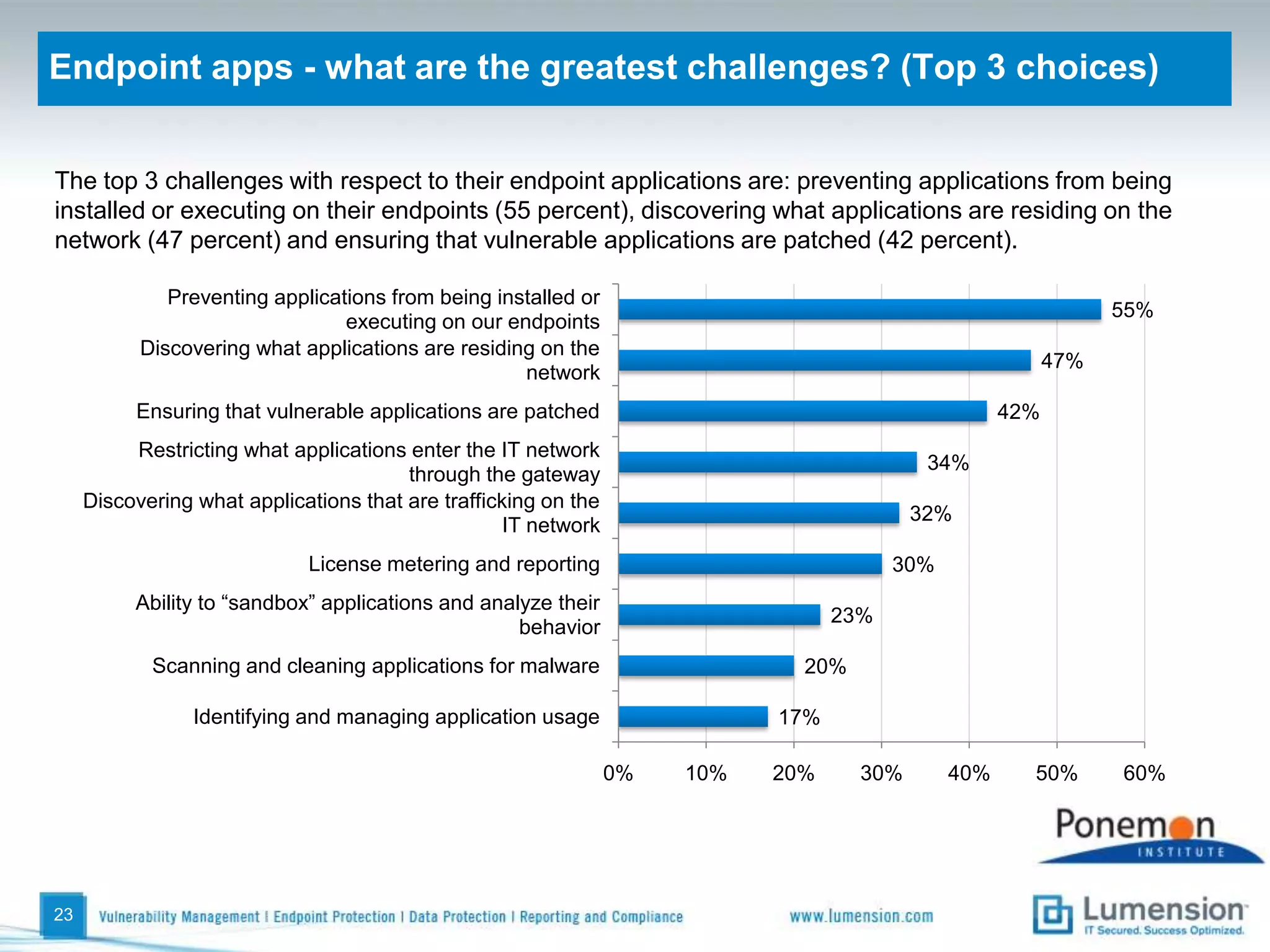
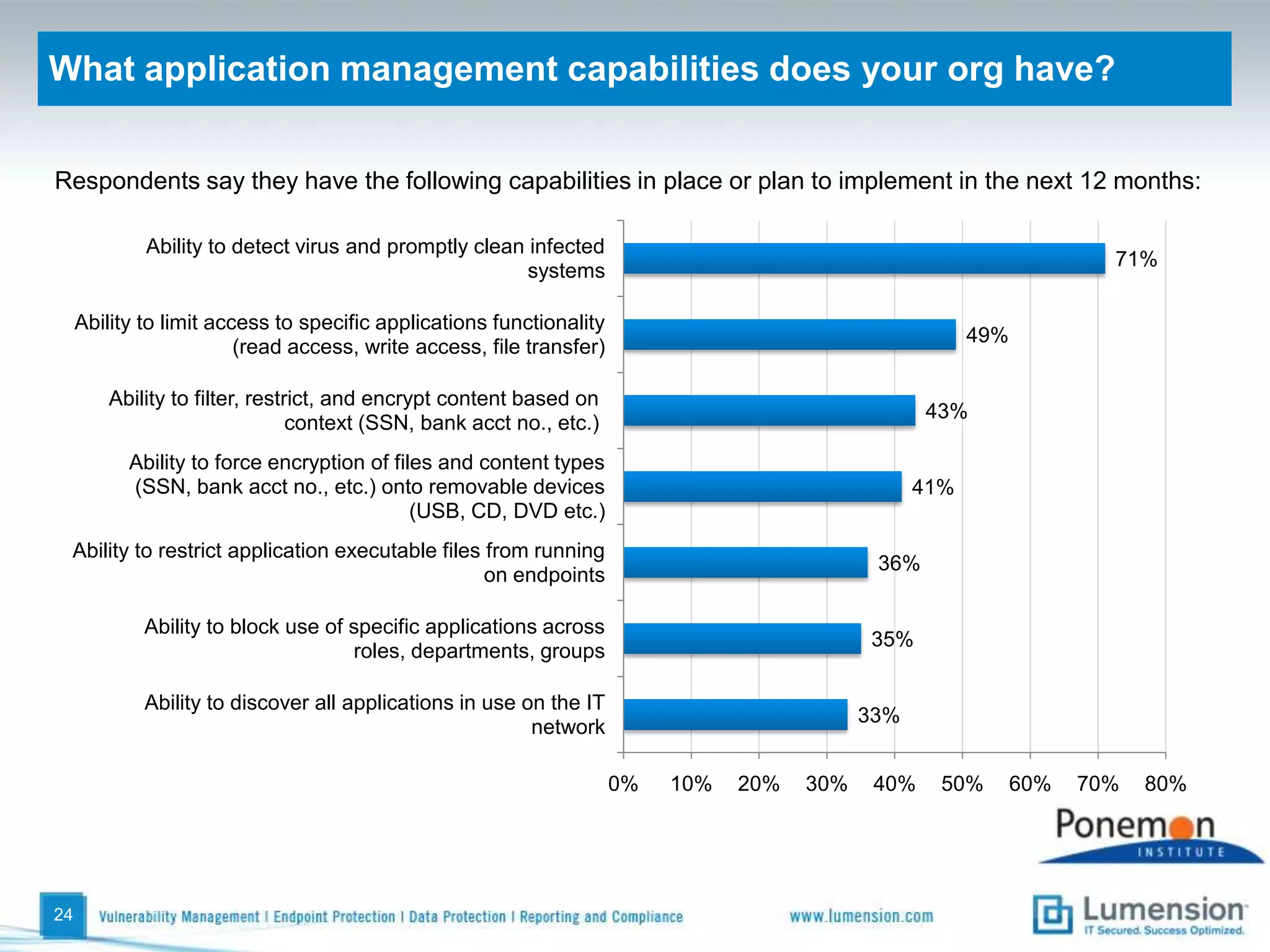
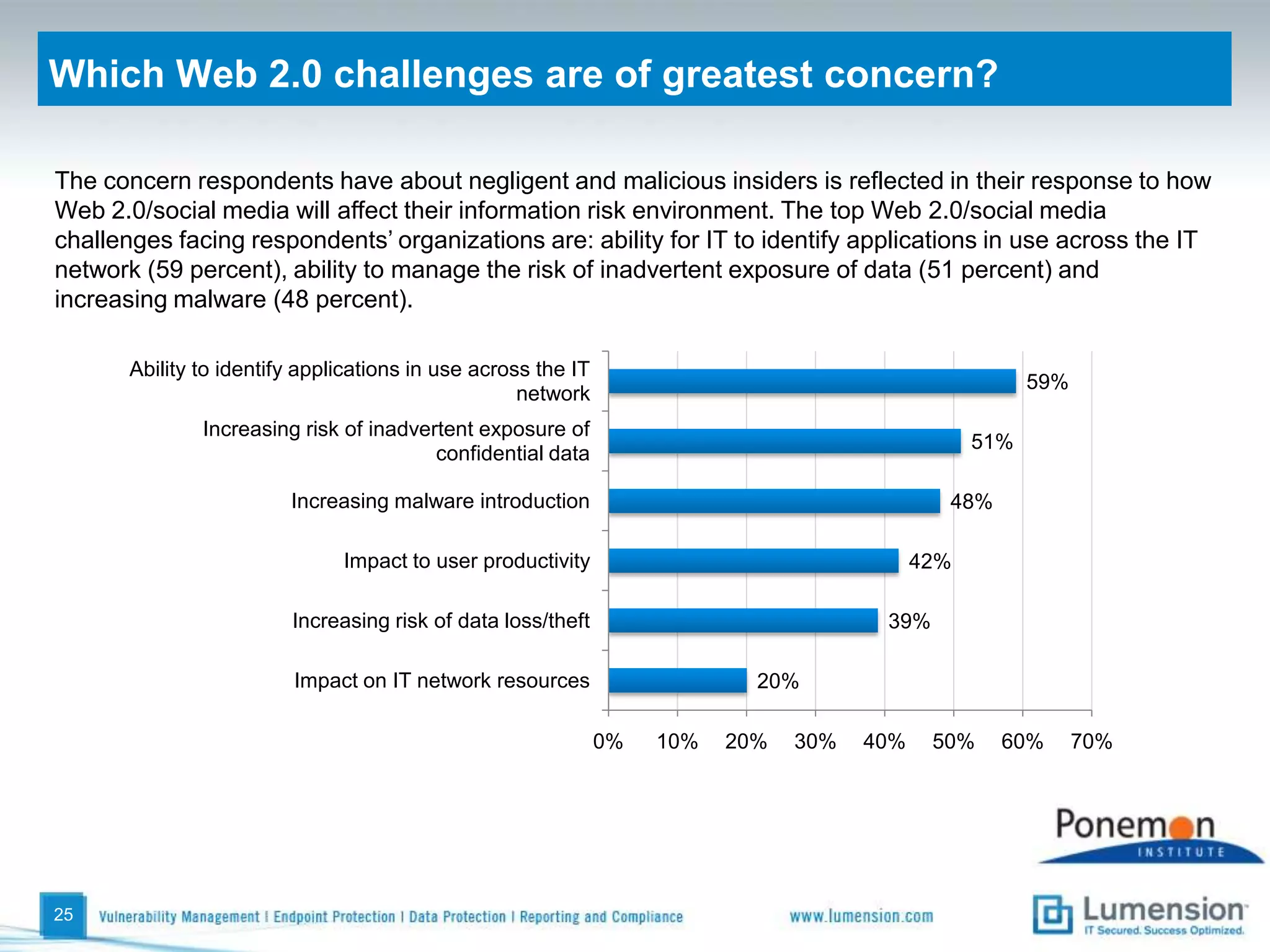
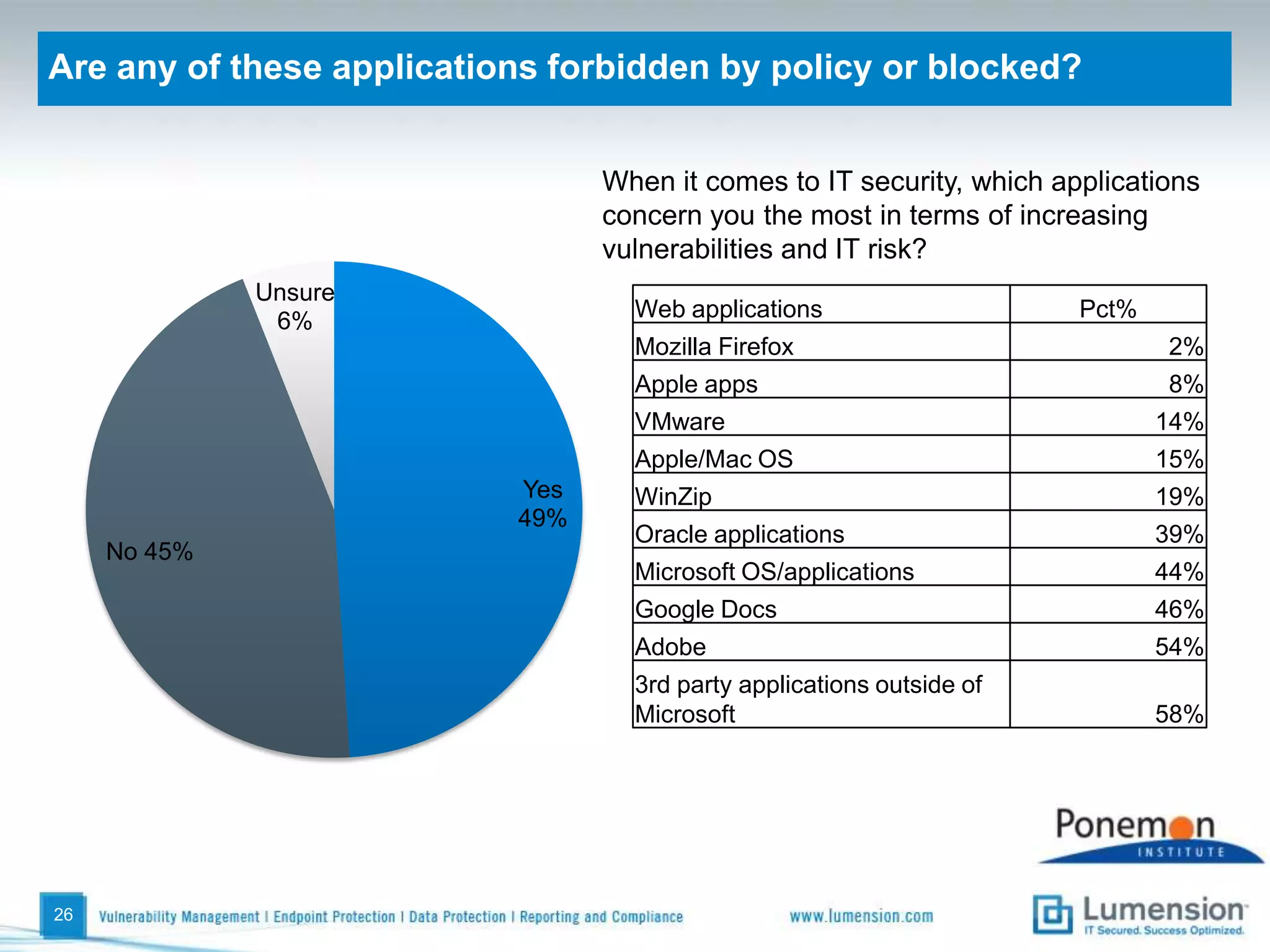
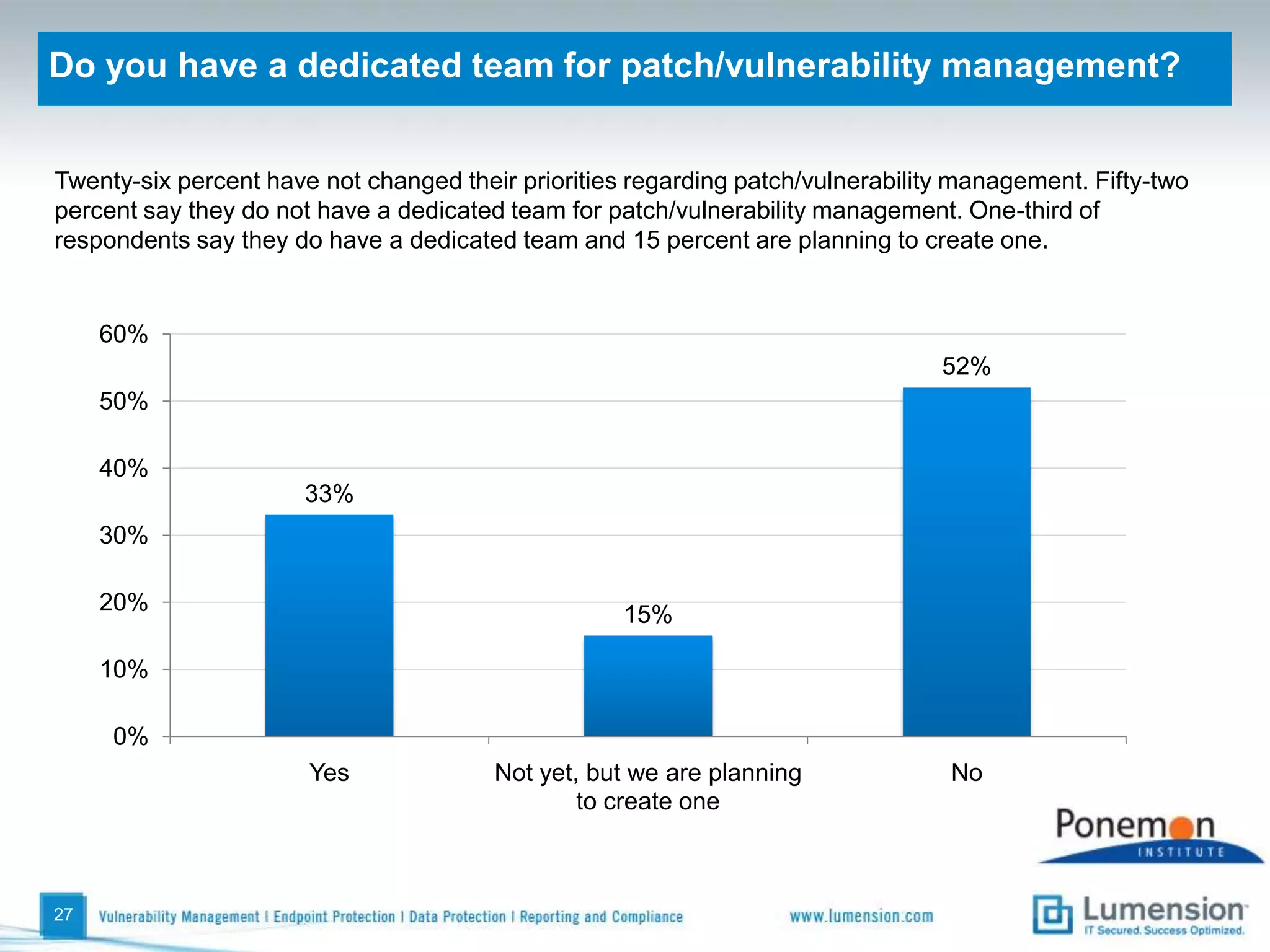
The survey found that organizations do not feel more secure than the previous year due to ineffective endpoint security technologies. Malware incidents are increasing and driving up IT costs. Zero-day attacks, SQL injections, and exploiting old software vulnerabilities are the biggest challenges. Respondents expect the top IT security risks in the next year will be negligent or malicious insiders, mobile device threats, and advanced persistent threats. Current approaches to endpoint security are costly and ineffective at preventing the rise of malware attacks through third-party and web-based applications.