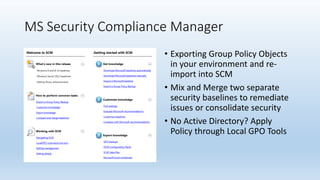
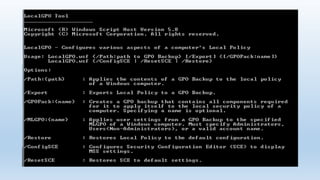
This document discusses strategies for hardening Windows operating systems and applications. It provides resources and guidelines for securing Microsoft OS's using tools like the Microsoft Security Compliance Manager and the Center for Internet Security benchmarks. Specific recommendations are given for mitigating risks from Java, Adobe Reader, local administrator passwords, and enabling full disk encryption with BitLocker. Troubleshooting tips are also included for addressing issues that may arise from an OS hardening project.