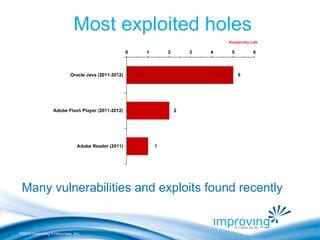
The document discusses Java's vulnerabilities and security mechanisms, emphasizing the need for regular updates and removal of outdated versions to ensure safety. It highlights the prevalence of Java 6 as the most vulnerable version, which is still widely used despite the availability of more secure alternatives like Java 7. Additionally, it outlines best practices for managing Java installations in order to mitigate security risks associated with exploits targeting older versions.



![©2010 Improving Enterprises, Inc.
Write once, run anywhere
Ubiquitous
Over 20 years old
Security model first implemented in 1.1.5 -
stack inspection with scopes [broken]
Exploits combine more than one
vulnerability](https://image.slidesharecdn.com/javasafety-130928202703-phpapp02/85/Running-Java-safely-5-320.jpg)




















