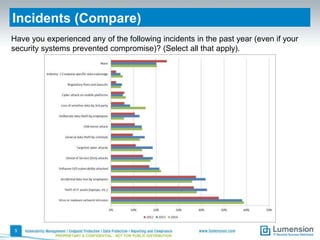
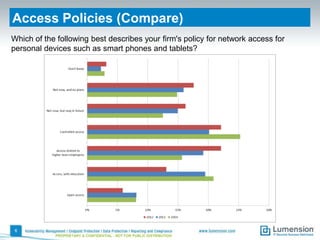
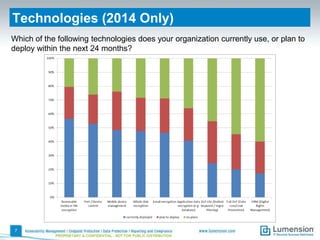
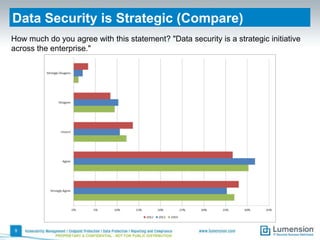
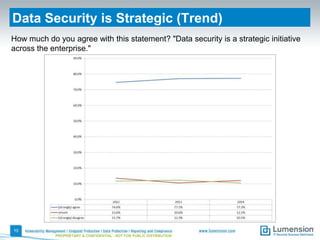
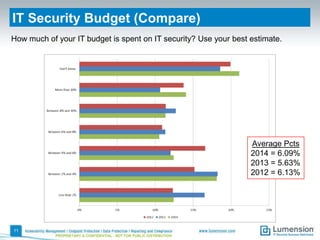
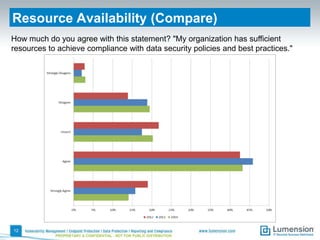
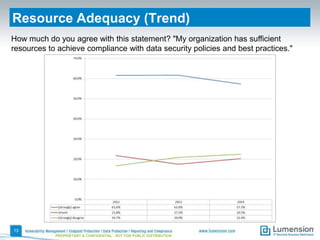
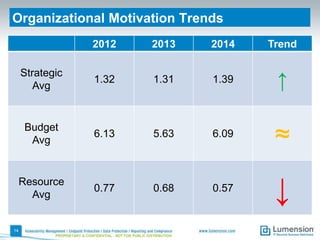
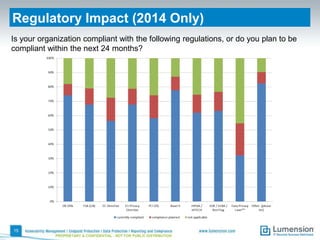
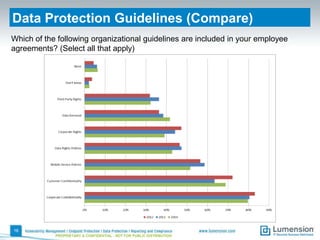
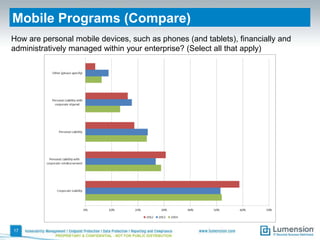
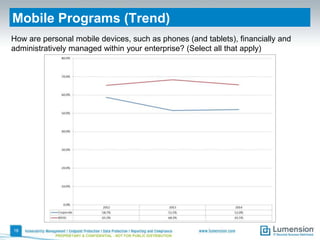
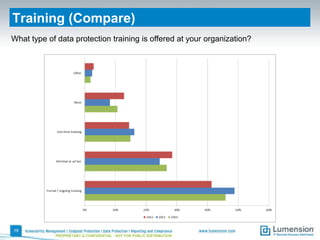
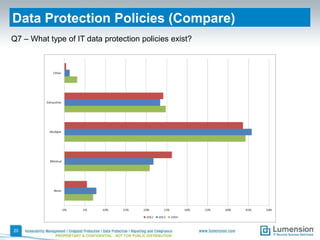
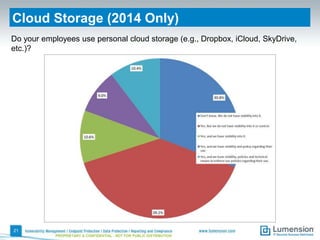
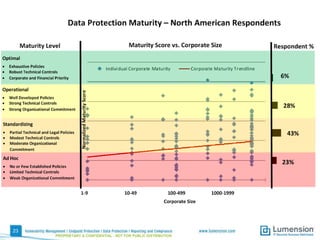
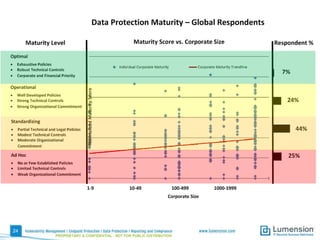
This document summarizes the results of a 2014 data protection maturity survey. It finds that while data security is increasingly seen as a strategic initiative, organizations still struggle with sufficient resources. On average, 6% of IT budgets are spent on security. The survey assessed technical, administrative, and motivational controls to determine an organization's maturity level. Most organizations fall in the standardizing or operational categories, showing some security practices but still needing improvement. The survey aims to help organizations understand their maturity and improve data protection.