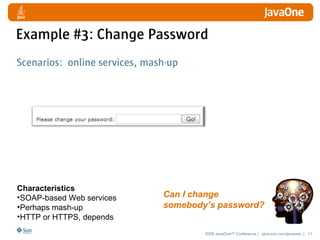
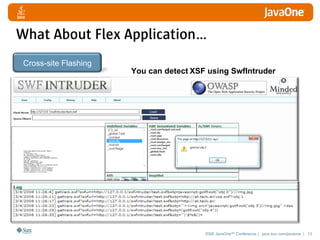
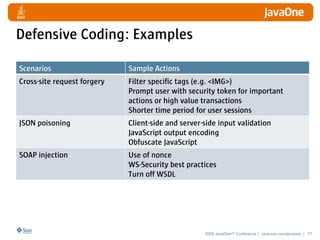
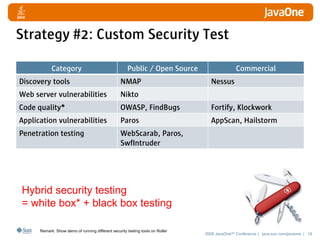
The document discusses detecting and defending against security vulnerabilities in Web 2.0 applications. It begins by outlining the top security issues in Web 1.0 vs Web 2.0 applications. Examples of vulnerabilities in Web 2.0 like cross-site scripting and JSON poisoning are provided. Strategies for detection include using security tools and custom security testing. Defense techniques include secure coding practices and security testing. The document emphasizes learning about security vulnerabilities and limitations of detection and defense.






![Example #2: What’s the Issue?
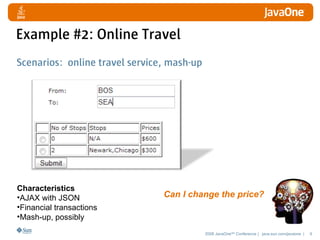
JSON Poisoning
What happens: Hackers intercepts the JSON, tampers it,
and posts it.
{ "From": "Boston", "To": "Seattle",
"flights": [ {"stops": "0", "transit"
: "N/A", "price": "$0"},
{"stops": "2", "transit" :
"Newark,Chicago", "price": "$900"} ] }
Result: hackers pay $0
2008 JavaOneSM Conference | java.sun.com/javaone | 10](https://image.slidesharecdn.com/2619984/85/TS-5358-10-320.jpg)