The document is a seminar report on computer viruses submitted for a B.Tech degree, highlighting the definition, types, and impacts of computer viruses. It discusses various virus categories, including worms, trojans, adware, rootkits, and ransomware, explaining their behaviors, spread mechanisms, and potential harm. Additionally, it includes acknowledgments, an abstract, and references, alongside figures and tables related to the topic.






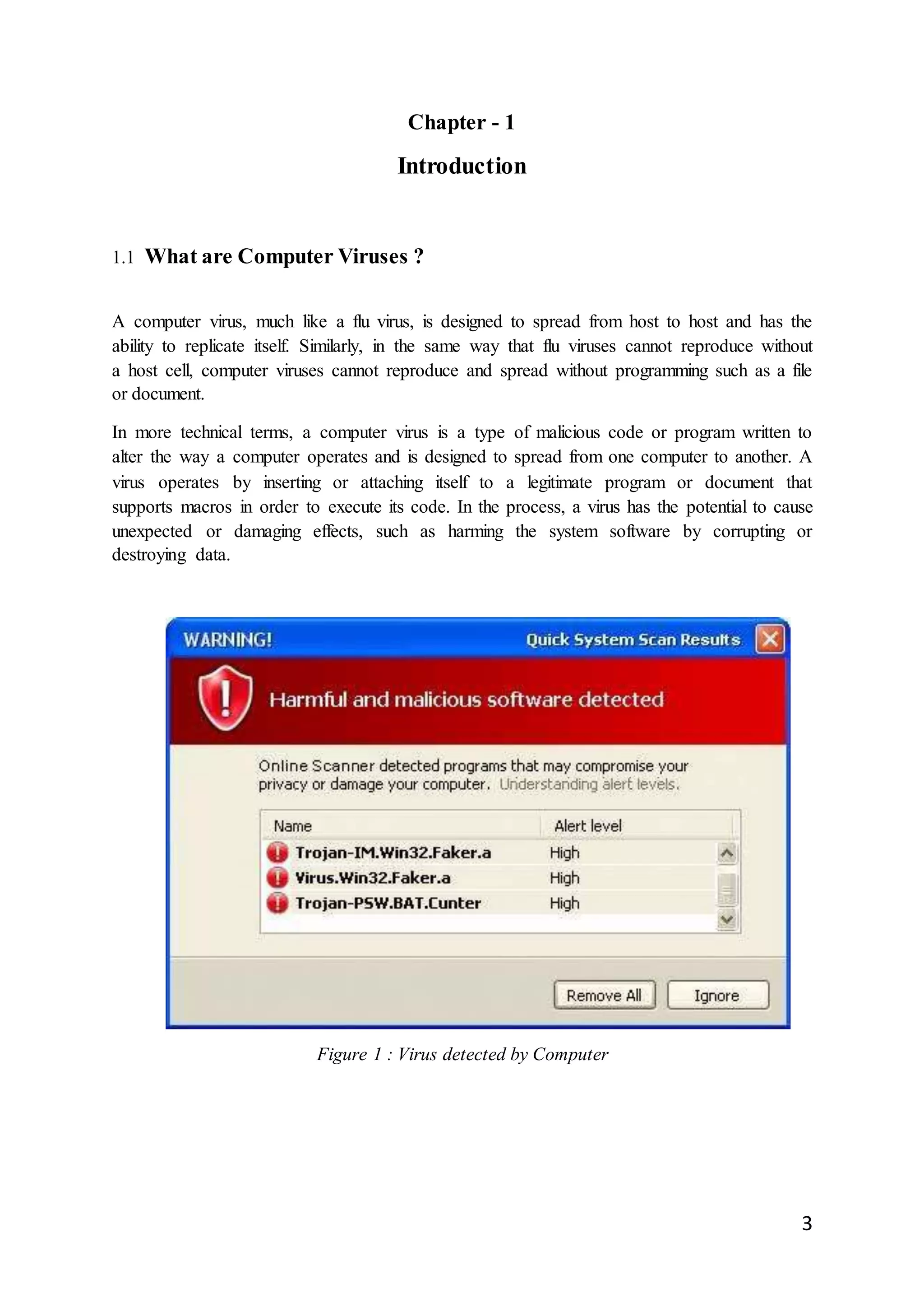



![7
Chapter -2
Categories of Virus
2.1 Worms
Worm is a self-replicating program, similar to a computer virus. A virus attaches itself to,
and becomes part of, another executable program; however, a worm is self-contained and
does not need to be part of another program to propagate. Worm is a small piece of
software that uses computer networks and security holes to replicate itself. A copy of the
worm scans the network for another machine that has a specific security hole. It copies
itself to the new machine using the security hole, and then starts replicating from there, as
well.
Figure 3 – Hex dump of the worm, showing a message left for Microsoft CEO Bill Gates by
the worm programmer Blaster [2]
Worms spread by exploiting vulnerabilities in operating systems. Vendors with security
problems supply regular security updates (see "Patch Tuesday"), and if these are installed
to a machine then the majority of worms are unable to spread to it. If a vulnerability is
disclosed before the security patch released by the vendor, a zero-day attack is possible.
Like the ILOVEYOU virus, which destroyed the files of more than 50 million internet
users worldwide, rendered PCs unbootable, copied people’s passwords and sent them to
its creators, and caused up to US$9 billion in damages in the year 2000.](https://image.slidesharecdn.com/computervirus-190517130134/75/Computer-virus-11-2048.jpg)



![15
Department of Justice also publicly issued an indictment against the Russian hacker Evgeniy
Bogachev for his alleged involvement in the botnet. It was estimated that at least US$3
million was extorted with the malware before the shutdown.
Reveton
In 2012, a major ransomware Trojan known as Reveton began to spread. Based on the
Citadel Trojan (which itself, is based on the ZeusTrojan), its payload displays a warning
purportedly from a law enforcement agency claiming that the computer has been used for
illegal activities, such as downloading unlicensed software or child pornography. Due to this
behaviour, it is commonly referred to as the "Police Trojan". The warning informs the user
that to unlock their system, they would have to pay a fine using a voucher from an
anonymous prepaid cash service such as Ukash or paysafecard. To increase the illusion that
the computer is being tracked by law enforcement, the screen also displays the computer's IP
address, while some versions display footage from a victim's webcam to give the illusion that
the user is being recorded.
Figure 6 – Reveton
Reveton initially began spreading in various European countries in early 2012.[5] Variants
were localized with templates branded with the logos of different law enforcement
organizations based on the user's country; for example, variants used in the United Kingdom
contained the branding of organizations such as the Metropolitan Police Service and
the Police National E-Crime Unit. Another version contained the logo of the royalty
collection society PRS for Music, which specifically accused the user of illegally
downloading music. In a statement warning the public about the malware, the Metropolitan
Police clarified that they would never lock a computer in such a way as part of an
investigation.](https://image.slidesharecdn.com/computervirus-190517130134/75/Computer-virus-19-2048.jpg)







