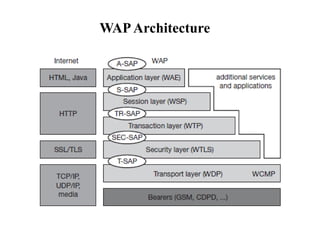
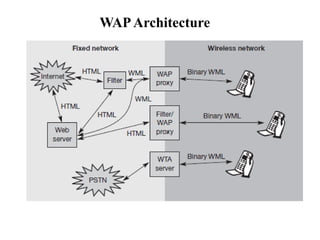
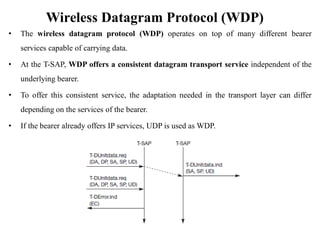
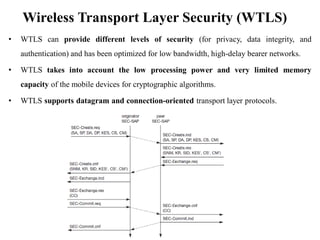
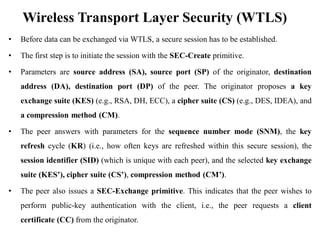
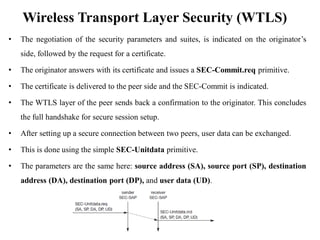
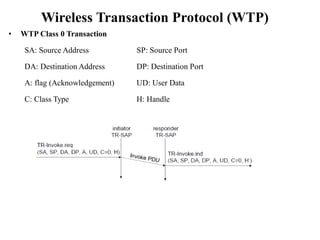
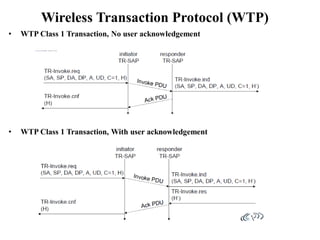
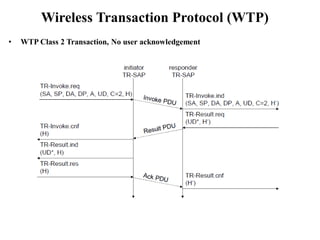
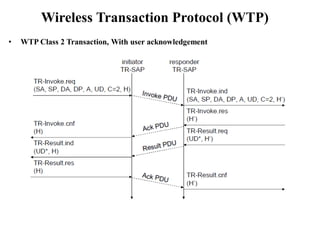
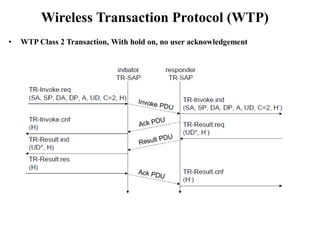
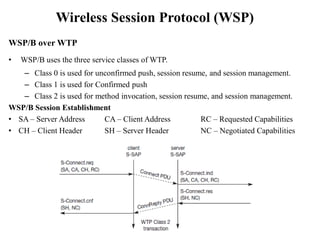
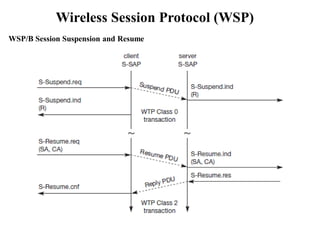
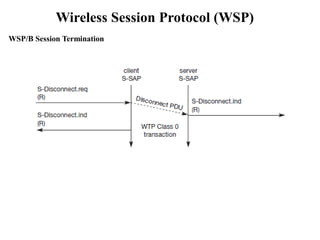
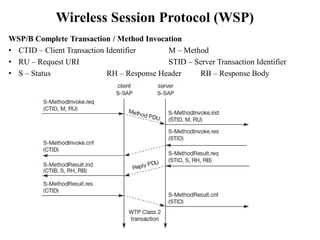
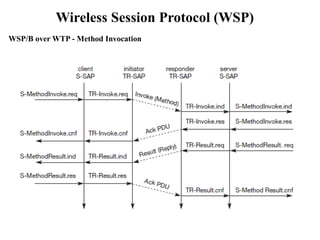
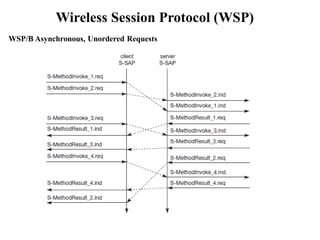
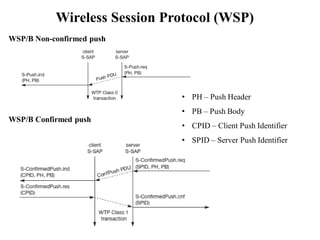
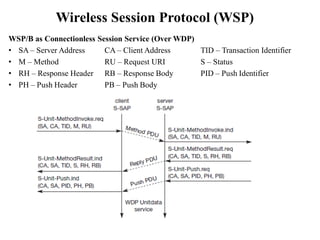
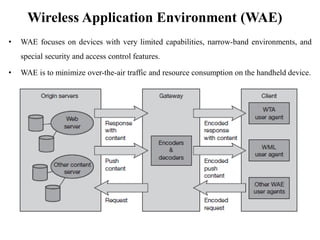
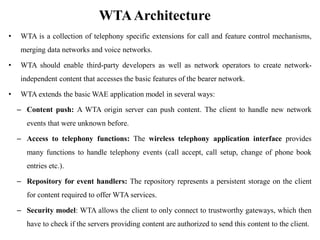
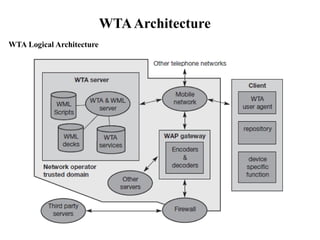
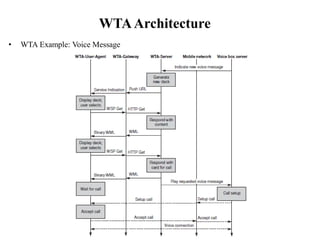
The document discusses various aspects of mobile transport and application layers including Mobile TCP, WAP architecture, Wireless Datagram Protocol (WDP), Wireless Transport Layer Security (WTLS), Wireless Transaction Protocol (WTP), Wireless Session Protocol (WSP), Wireless Application Environment (WAE), and WTA architecture. Mobile TCP aims to avoid packet loss over wireless links. The WAP architecture defines layers for transport, security, transactions, and applications to enable wireless internet access. Protocols like WDP, WTLS, WTP and WSP operate at different layers to provide services like transport, security, transactions and sessions. WAE and WTA provide frameworks for mobile applications and access to telephony functions.