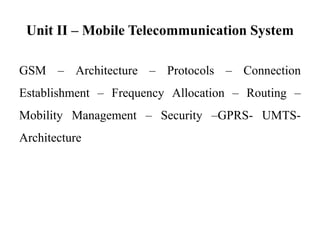
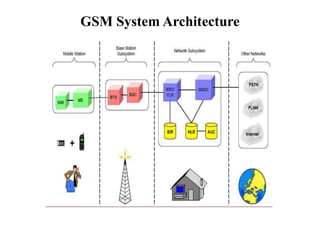
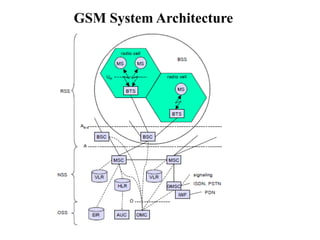
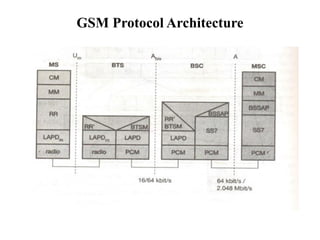
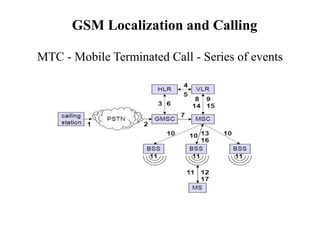
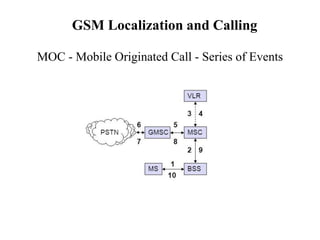
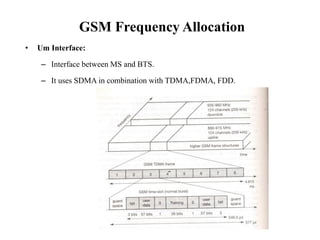
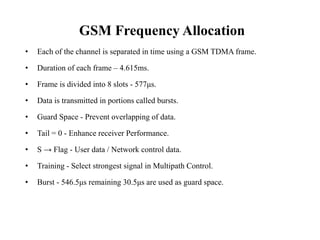
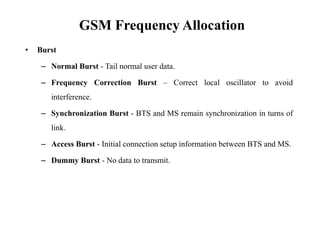
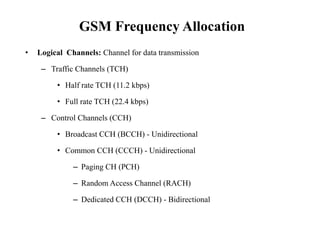
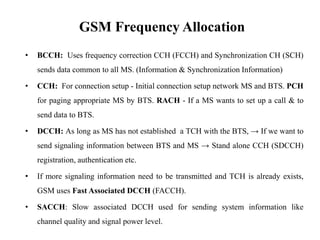
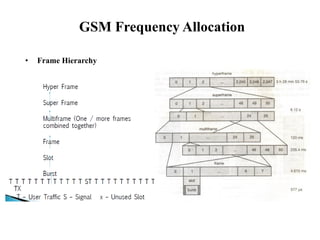
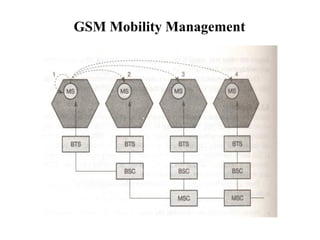
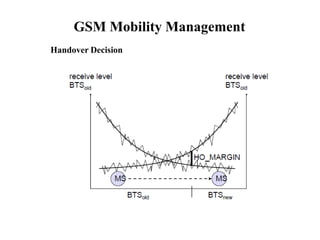
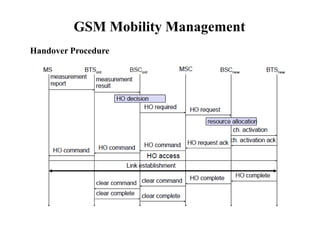
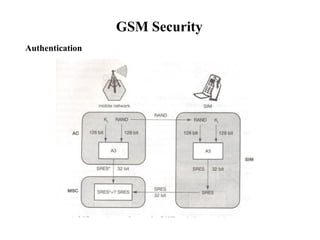
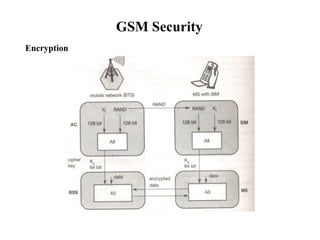
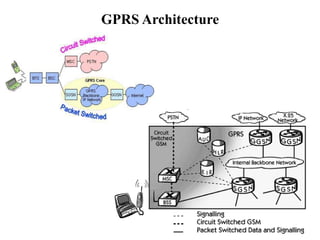
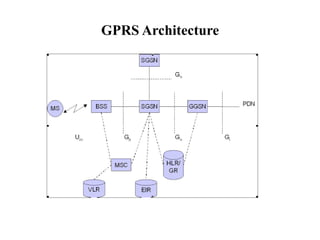
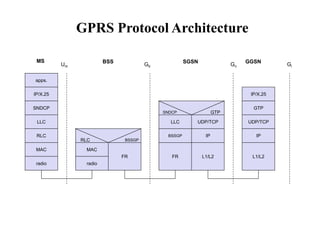
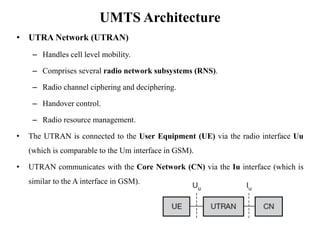
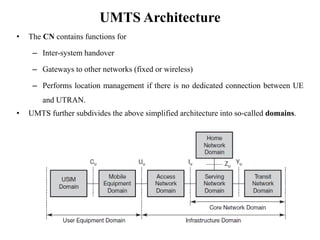
GSM is a 2G mobile communication system that provides voice and data services using radio frequency bands between 800-2000MHz. It has a three-part architecture including the radio subsystem with mobile stations, base stations and controllers; the network and switching subsystem with mobile switching centers and registers; and the operation subsystem for network management. Key protocols used in GSM include LAPDm for signaling, mobility management for registration and location updating, and call management for call establishment and control. GSM provides location tracking as users roam between different visitor location registers.