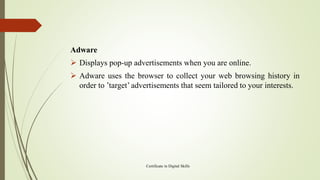
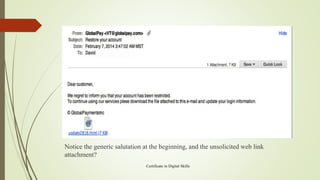
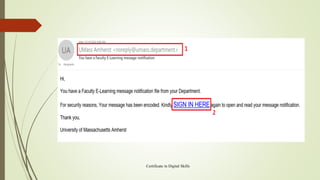
The document provides an overview of IT security topics including malware, phishing, protecting data on devices, and safely searching online. It defines types of malware like viruses, spyware, and adware that can harm devices. Phishing is described as attempting to steal personal information through deceptive messages. The document outlines signs of malware infection and advises using antivirus software, firewalls, and encryption to secure devices and data. It also provides tips for safely searching online like using privacy tools and evaluating website content and credibility.