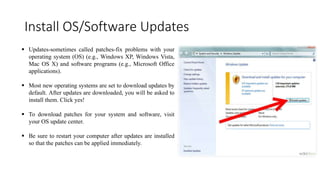
This tutorial outlines essential practices for protecting personal information and computers from cyber threats such as viruses, hackers, and identity theft. It emphasizes seven key actions for cyber safety including updating software, using antivirus tools, preventing identity theft, and securing passwords. The guide also discusses the roles of cybercriminals and provides recommendations for maintaining cyber safety at home and in the workplace.