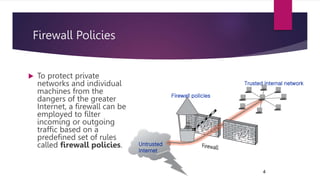
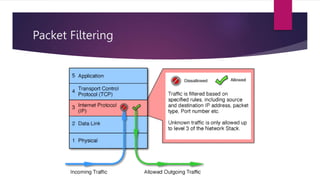
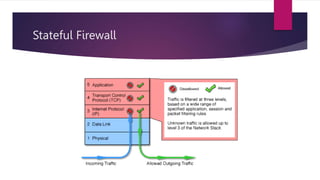
A firewall is a collection of security measures that prevents unauthorized access between networked systems. It monitors traffic and implements security policies at a single point. Firewalls can filter incoming or outgoing traffic based on predefined rules. Packets can be accepted, dropped, or rejected by firewall policies that examine properties like protocols, ports, and packet payloads.