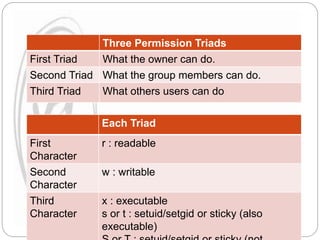
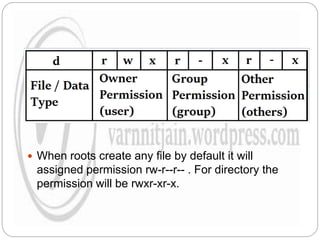
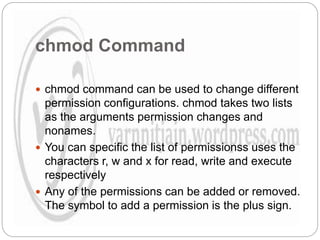
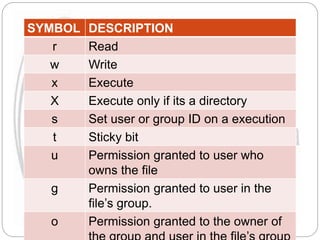
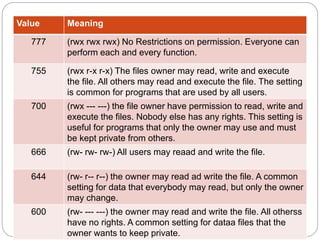
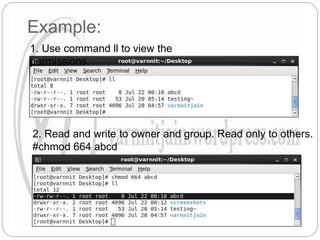
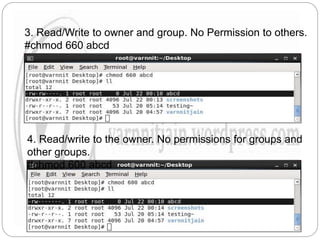
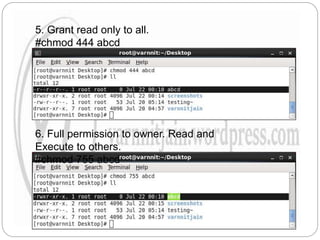
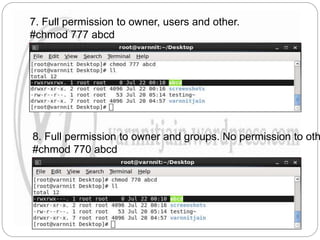
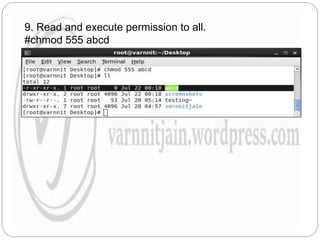
The document explains file permissions in Linux systems, highlighting the management of access rights for users, groups, and others. It details symbolic and numeric notation for permissions, including the significance of the chmod command for changing these configurations. Additionally, it provides examples of various permission settings and their implications for file accessibility.