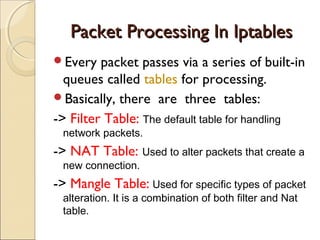
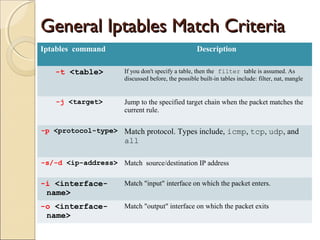
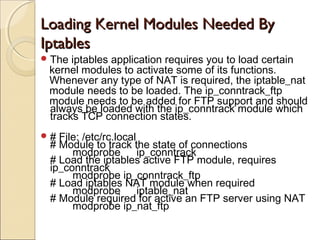
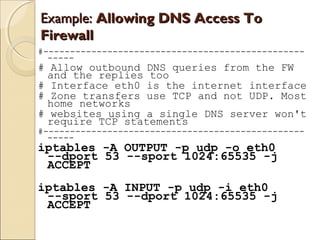
This document summarizes a seminar on firewalls and iptables. It defines a firewall as software or hardware that controls network traffic by applying rule sets to determine whether incoming or outgoing packets are allowed. It describes different types of firewalls including network layer/packet filters, application layer firewalls, proxies, and network address translation (NAT) firewalls. It also explains what iptables is, how packet processing works in iptables using tables like filter, NAT, and mangle, and provides examples of common iptables commands and how to configure rules to allow DNS access and internet access from the firewall.