This document provides an introduction and overview of Secure Multi-Party Computation (SMPC). It begins with an introduction of the speaker and agenda. It then defines SMPC as a problem in distributed computing where parties wish to compute a function while preserving privacy and correctness, even if some parties are faulty. It presents the Millionaire's Problem protocol as an example. Real-world applications are discussed, along with adversary classifications and desirable SMPC properties. Key techniques like garbled circuits, oblivious transfer, and secret sharing are introduced. The document concludes by outlining future topics to be covered.






![Real World Problem….?
Online Dating
Electronic Voting
Privacy-preserving Statistics [ ex: satellite collision ]
Privacy-preserving Database Operations
Benchmarking
Privacy-preserving data mining
Secure e-auction](https://image.slidesharecdn.com/41drsqhqry43lpdm3ick-signature-fa17ef08645a3cce9ed98bc960f7e89b419197b8ab9318d2a54057ce7f634710-poli-160709185307/75/Introduction-to-smpc-7-2048.jpg)
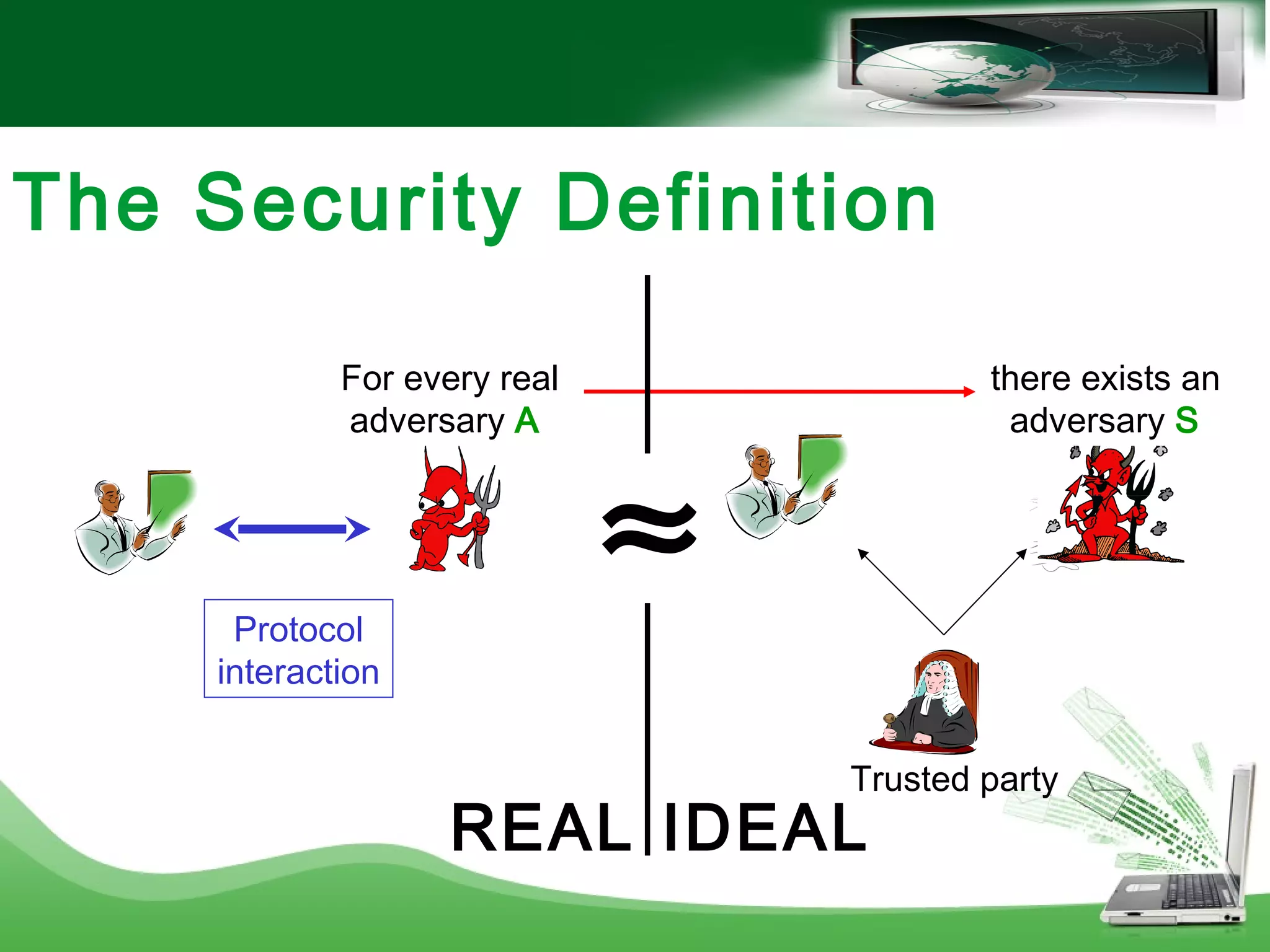
![Computational Setting
Any two-party function can be securely computed in the semi-
honest adversarial model [Yao]
Any multiparty function can be securely computed in the
malicious model, for any number of corrupted parties [GMW]](https://image.slidesharecdn.com/41drsqhqry43lpdm3ick-signature-fa17ef08645a3cce9ed98bc960f7e89b419197b8ab9318d2a54057ce7f634710-poli-160709185307/75/Introduction-to-smpc-10-2048.jpg)