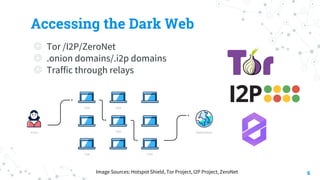
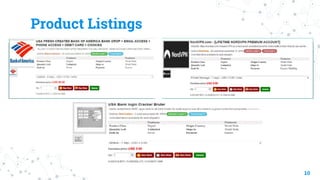
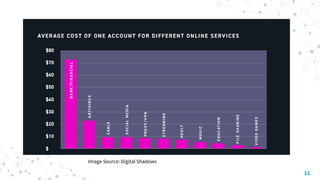
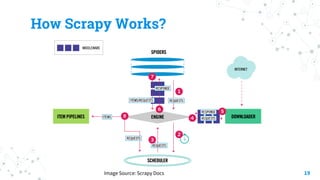
The document discusses threat hunting on the dark web, covering its definition, importance, and methods used for effective hunting. It emphasizes the need for operational security (opsec) to prevent information leaks while navigating dark web forums and marketplaces. The document also outlines various tools and techniques utilized in threat hunting, and stresses the complexity and resource demands of the process.