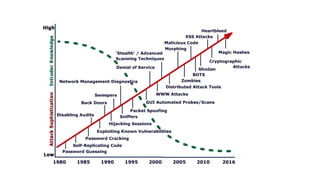
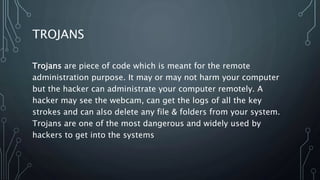
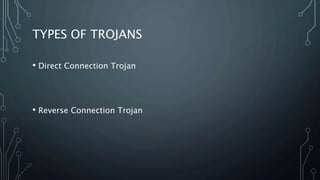
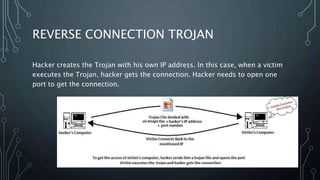
This document discusses cyber security fundamentals and social engineering. It covers the need for security due to increasing technology use and cyber criminals. It defines hacking and different types of hackers like white hat, black hat, and grey hat hackers. The document also discusses networking fundamentals like IP addresses, types of IP addresses, and Trojans. It defines viruses, worms, direct connection Trojans, and reverse connection Trojans. Finally, it introduces social engineering as the use of deception to manipulate individuals into revealing private information, and discusses techniques and the human element as the weakest link in security.