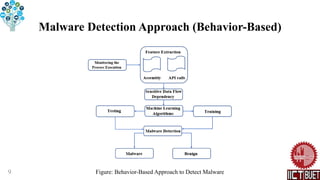
The document discusses malware detection approaches using data mining techniques. It describes signature-based and behavior-based approaches. Signature-based detection identifies malware by matching signatures in a predefined database, but struggles with polymorphic malware. Behavior-based detection analyzes malware behaviors through dynamic analysis, allowing detection of novel malware but having higher computational costs. Both approaches have advantages and limitations for malware detection.








![References
[1] Souri A, Hosseini R (2018) A state-of-the-art survey of malware detection
approaches using data mining techniques. Human-centric Computing and
Information Sciences 8:1-22.
[2] Fraley JB, Figueroa M(2016) Polymorphic malware detection using topological
feature extraction with data mining. SoutheastCon 2016, pp 1-7.
[3] Malhotra A, Bajaj K (2016) A hybrid pattern-based text mining approach for
malware detection using DBScan. Trans ICT 4:141–149.
[4] Boujnouni ME, Jedra M, Zahid N (2015) New malware detection framework
based on N-grams and support vector domain description. In: 2015 11th
international conference on information assurance and security (IAS), pp 123–128.
14](https://image.slidesharecdn.com/malwaredetectionapproachesusingdataminingtechniques-220423131155/85/Malware-Detection-Approaches-using-Data-Mining-Techniques-pptx-14-320.jpg)
![References
[5] Wang P, Wang Y-S (2015) Malware behavioral detection and vaccine
development by using a support vector model classifier. Journal of Computer and
System Sciences 81:1012–1026.
[6] Sun H, Wang X, Buyya R, Su J (2017) CloudEyes: cloud-based malware
detection with reversible sketch for resourceconstrained internet of things (IoT)
devices. Software—Practice & Experience 47:421–441.
[7] Tang Y, Xiao B, Lu X (2011) Signature tree generation for polymorphic worms.
IEEE Transactions on Computers 60:565–579.
[8] Palumbo P, Sayfullina L, Komashinskiy D, Eirola E, Karhunen J (2017) A
pragmatic android malware detection procedure. Computers and Security 70:689–
701.
15](https://image.slidesharecdn.com/malwaredetectionapproachesusingdataminingtechniques-220423131155/85/Malware-Detection-Approaches-using-Data-Mining-Techniques-pptx-15-320.jpg)
