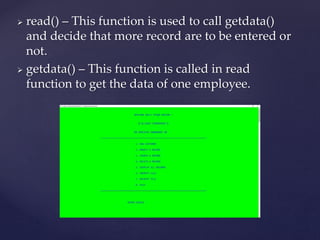
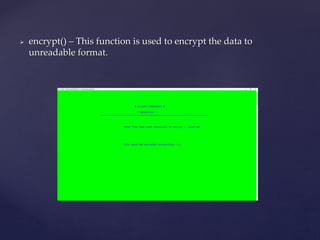
This document describes an encrypted database management system that allows administrators to securely store and access employee data from anywhere using their smartphone. It discusses how encryption protects data even if stolen, as attackers cannot access it without the encryption key. The system allows administrators to add, read, write, modify, search, delete, encrypt, and decrypt employee records including name, age, ID number, mobile number, salary, sector, year of joining, gender, and designation. It provides functions for logging in, displaying interfaces, performing database operations, and concluding that C++ is well-suited for building such secure systems.