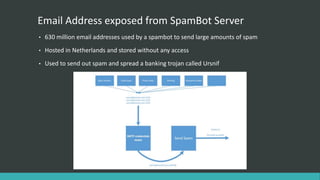
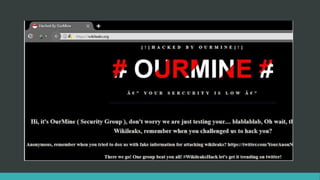
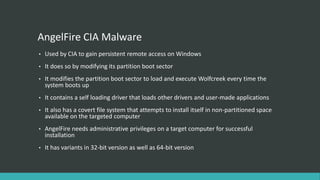
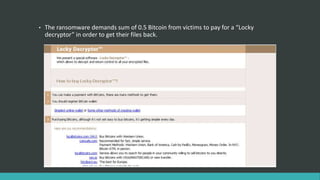
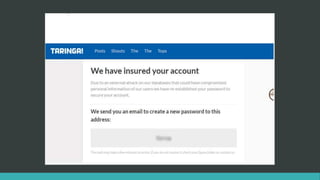
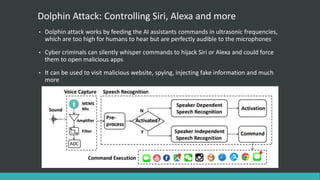
This document summarizes several recent security news stories. It reports on the discovery of the WireX Android botnet that has infected over 120,000 devices and is used to conduct DDoS attacks. It also mentions a data breach at Instagram that exposed users' contact info, the hacking of WikiLeaks' website by changing its DNS, the exposure of 630 million email addresses used by a spam bot, and the use of the CIA malware AngelFire to gain remote access on Windows devices. The document concludes by covering the Locky ransomware email scheme and a data breach at the social network Tiranga.