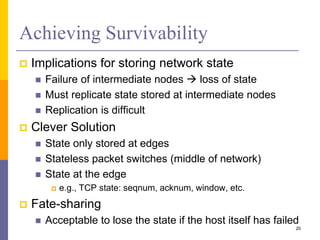
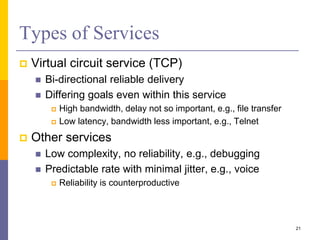
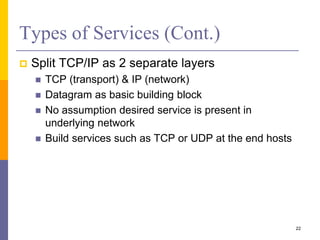
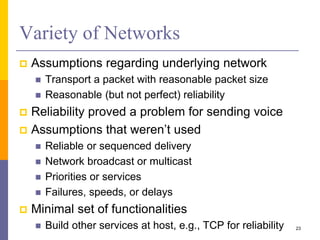
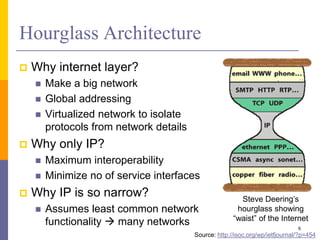
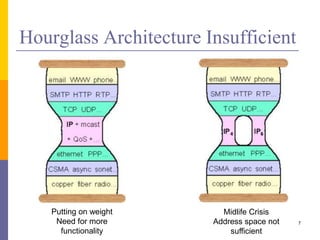
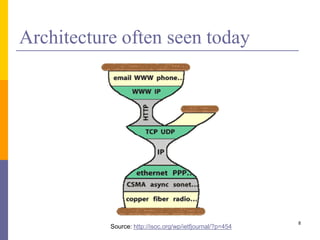
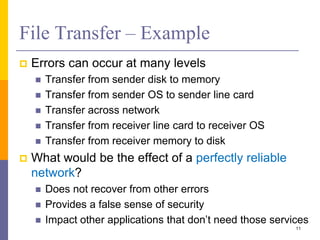
The document discusses the architecture and design philosophy of the internet, highlighting key principles such as the end-to-end argument and the hourglass model. It outlines the fundamental goals and trade-offs in the design of TCP/IP protocols, emphasizing the need for survivability, service variety, and distributed management. The summary also indicates that while some goals have been successfully achieved, others have posed challenges, particularly regarding the efficiency of implementations.


![End-to-End Argument [1]
Examines which layer should implement a service
Argue many services should be implemented at
higher layers
e.g., on end hosts
Contributions
Fits with the model of minimal network (IP) layer
Provides guidance on what (not) to add to data link
layers
End-to-end principle is fundamental to Internet success
9](https://image.slidesharecdn.com/01-internetarchitecturedesignphilosophy-180818031552/85/Internet-Architecture-and-Design-Philosophy-9-320.jpg)


![Why TCP/IP? [2]
Objective
Why TCP/IP was designed this way?
DARAP Internet Architecture
1 fundamental goal
Several 2nd level goals
Ordering of 2nd level goals
15](https://image.slidesharecdn.com/01-internetarchitecturedesignphilosophy-180818031552/85/Internet-Architecture-and-Design-Philosophy-15-320.jpg)