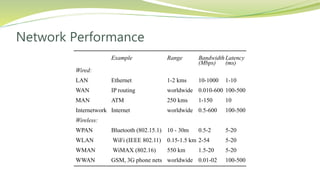
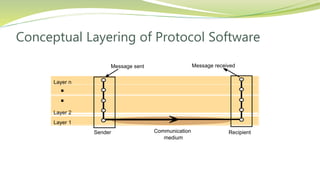
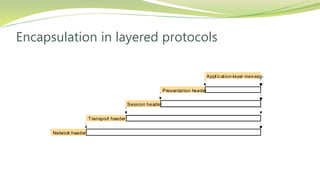
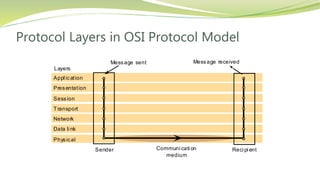
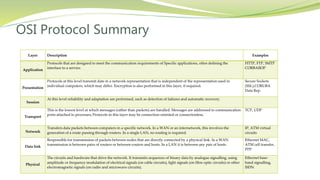
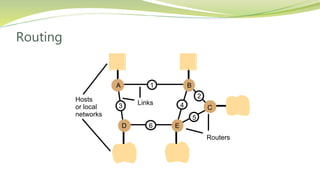
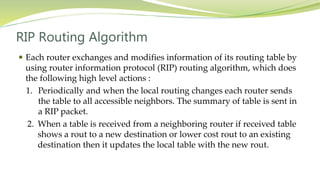
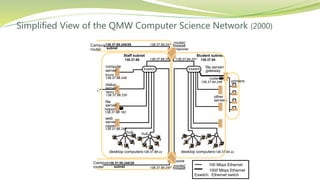
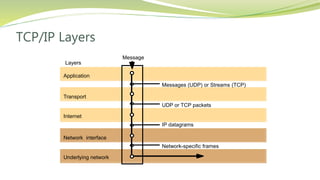
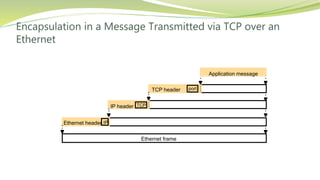
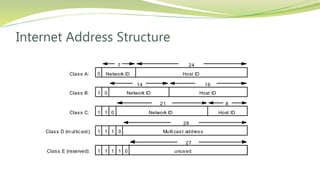
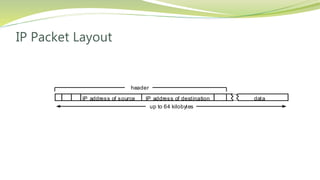
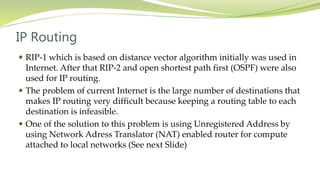
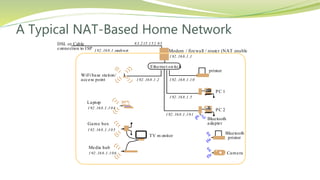
The document provides an overview of networking issues for distributed systems, basic networking concepts, and Internet protocols. It discusses performance parameters like latency and data transfer rate that affect message transfer speed. It also describes various wired and wireless network types and their typical bandwidth and latency ranges. The document introduces the OSI 7-layer model and summarizes each layer's functions. It explains concepts like routing, routing algorithms, encapsulation, and the TCP/IP protocol stack. The document provides examples of routing tables, packet encapsulation, and how NAT enables private addressing on local networks.