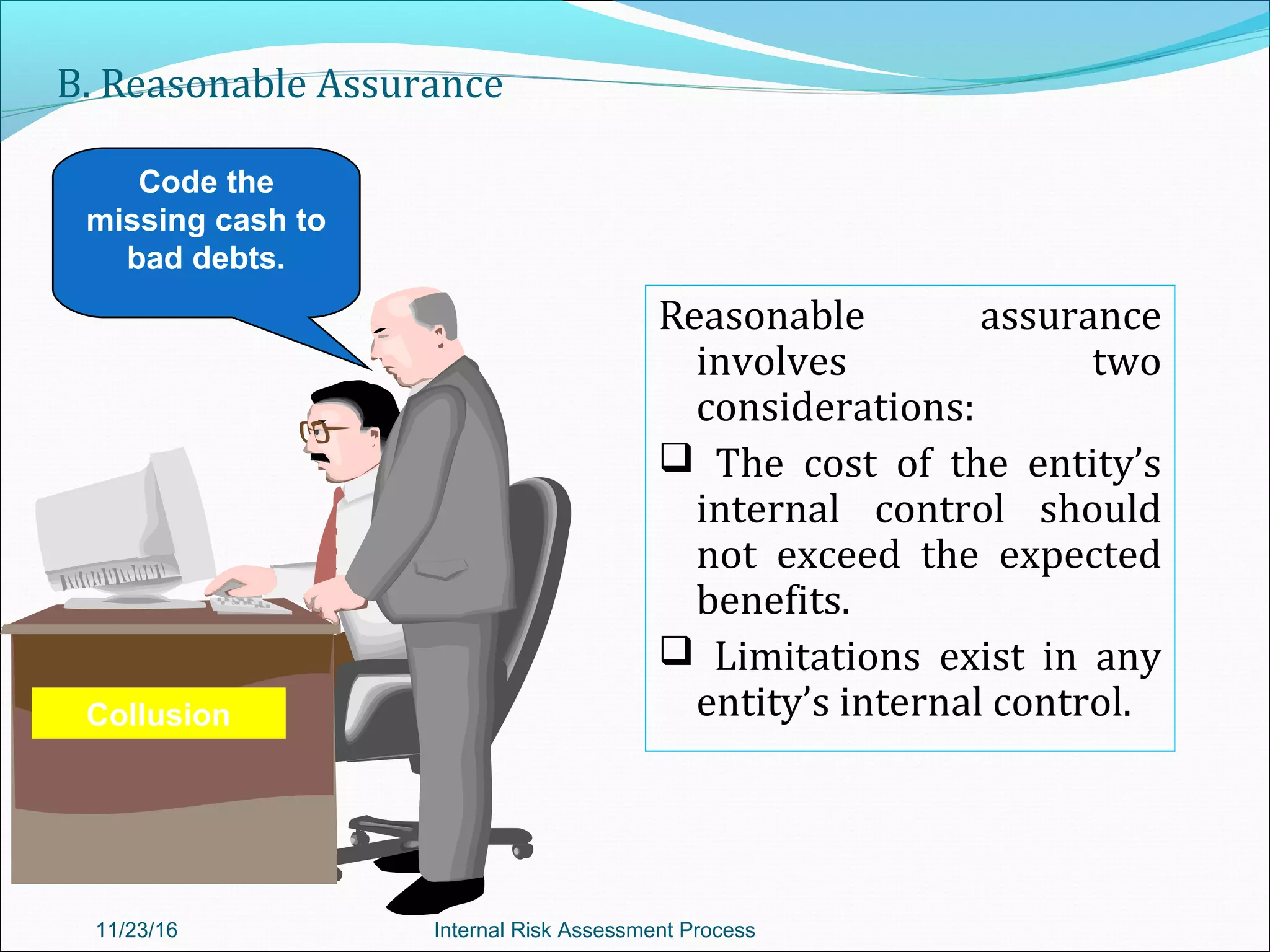
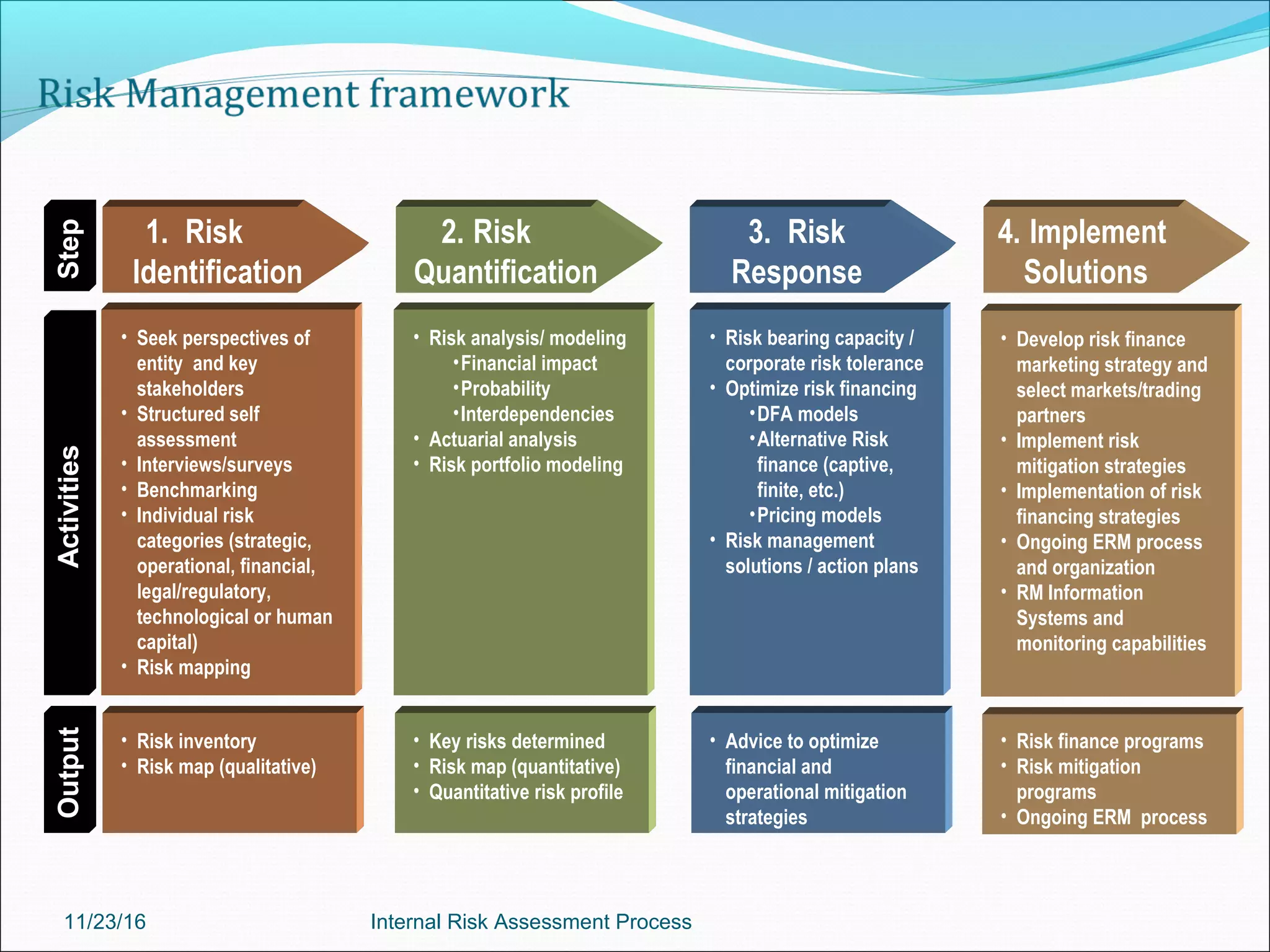
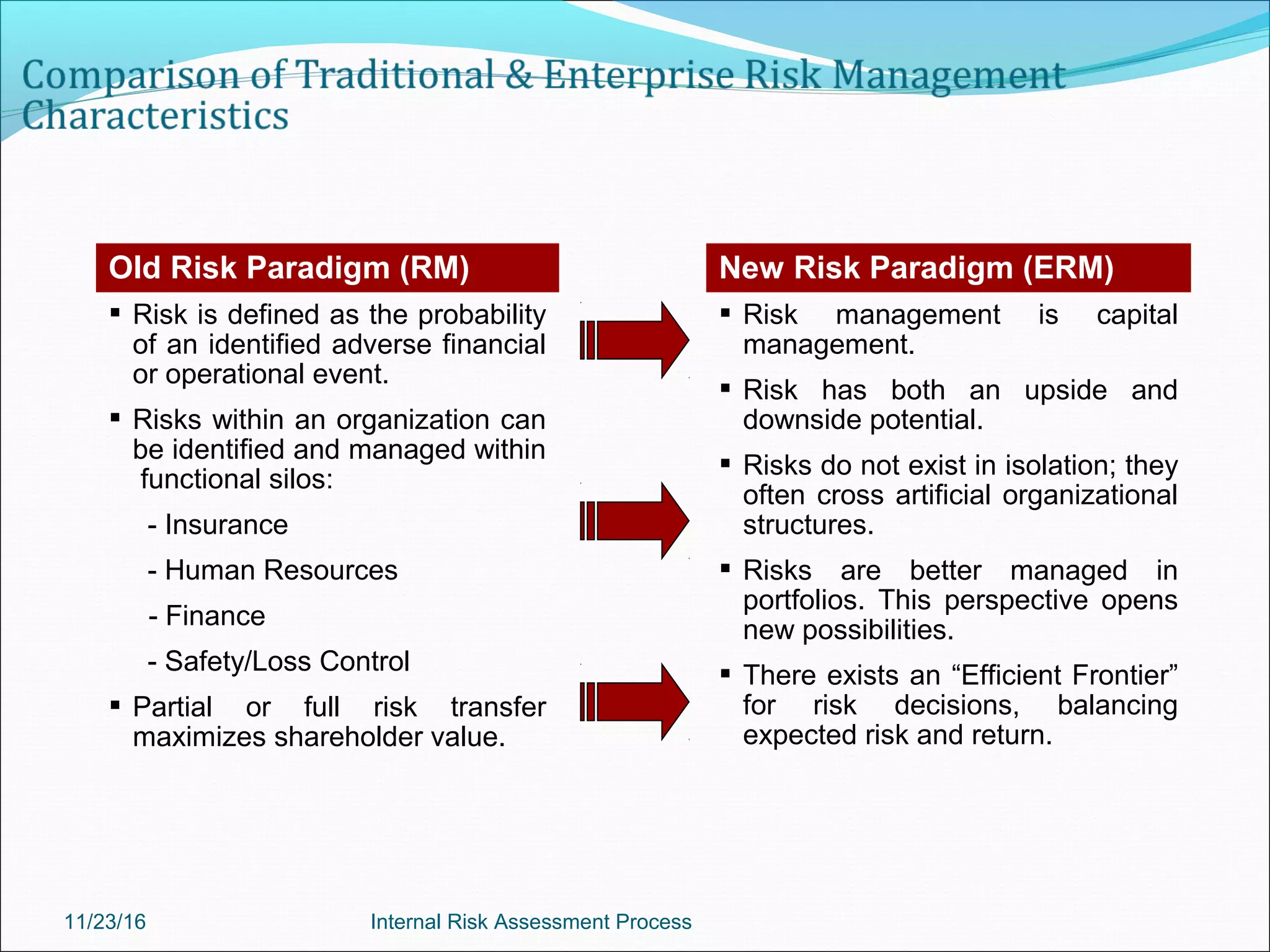
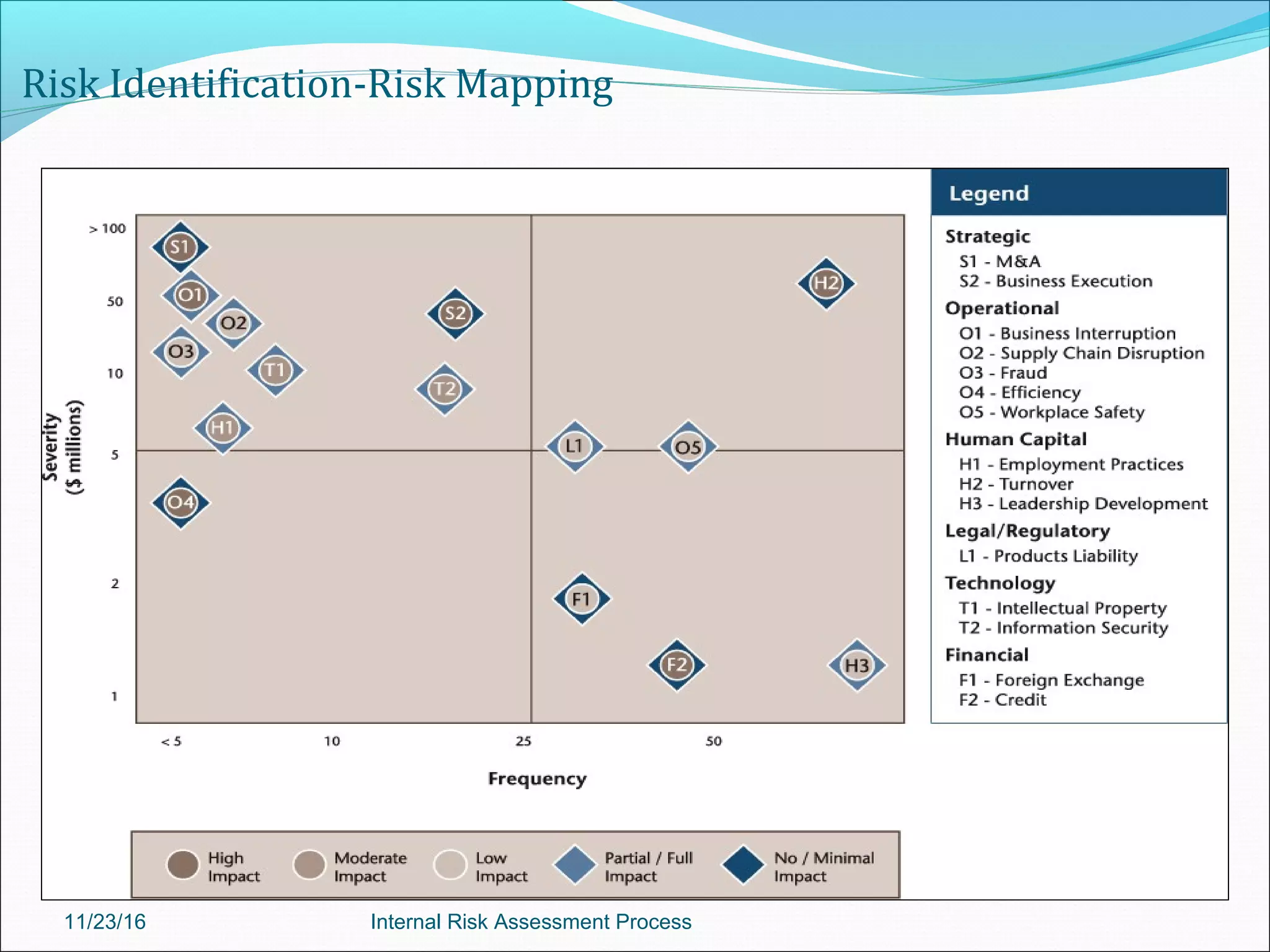
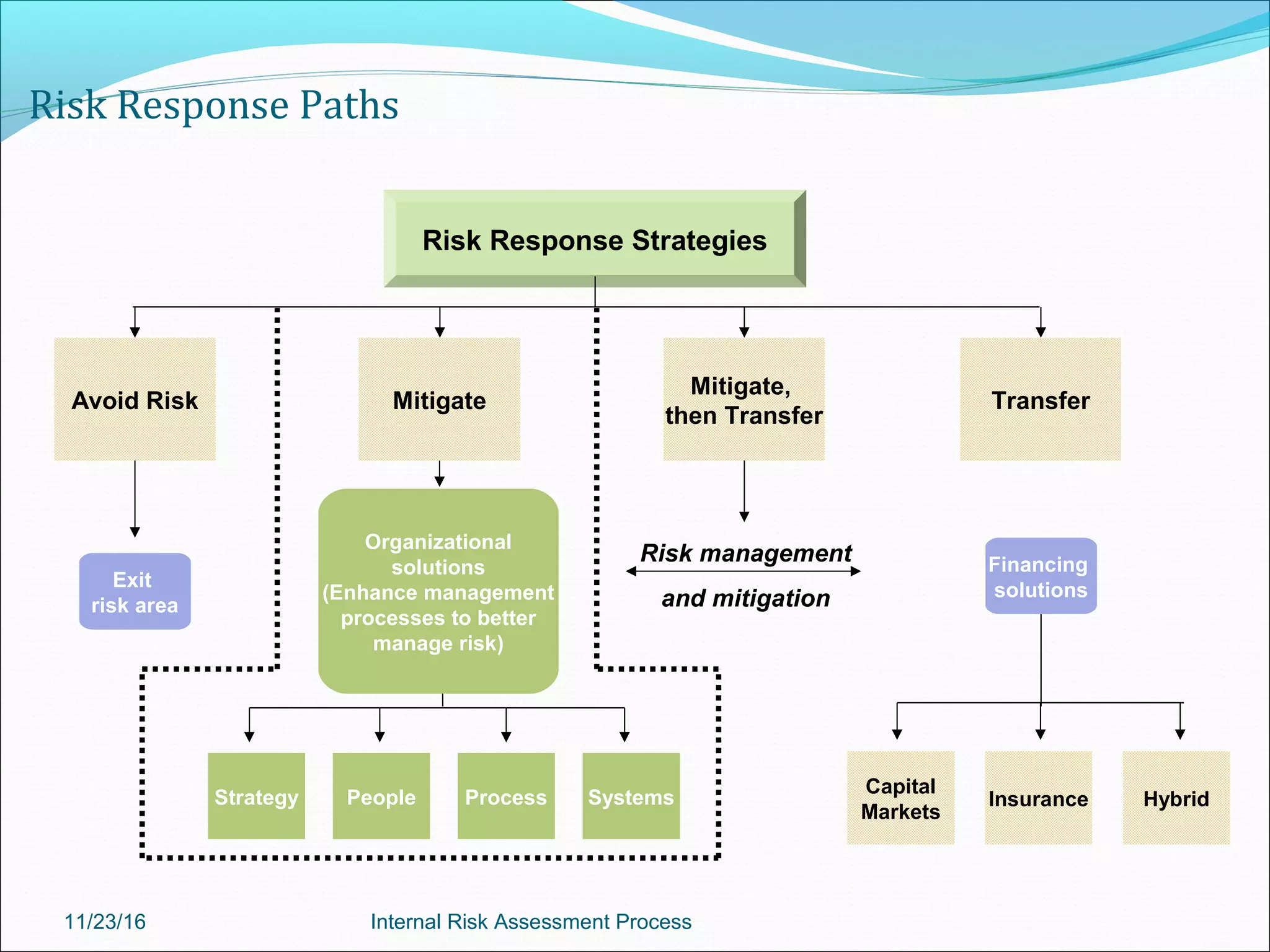
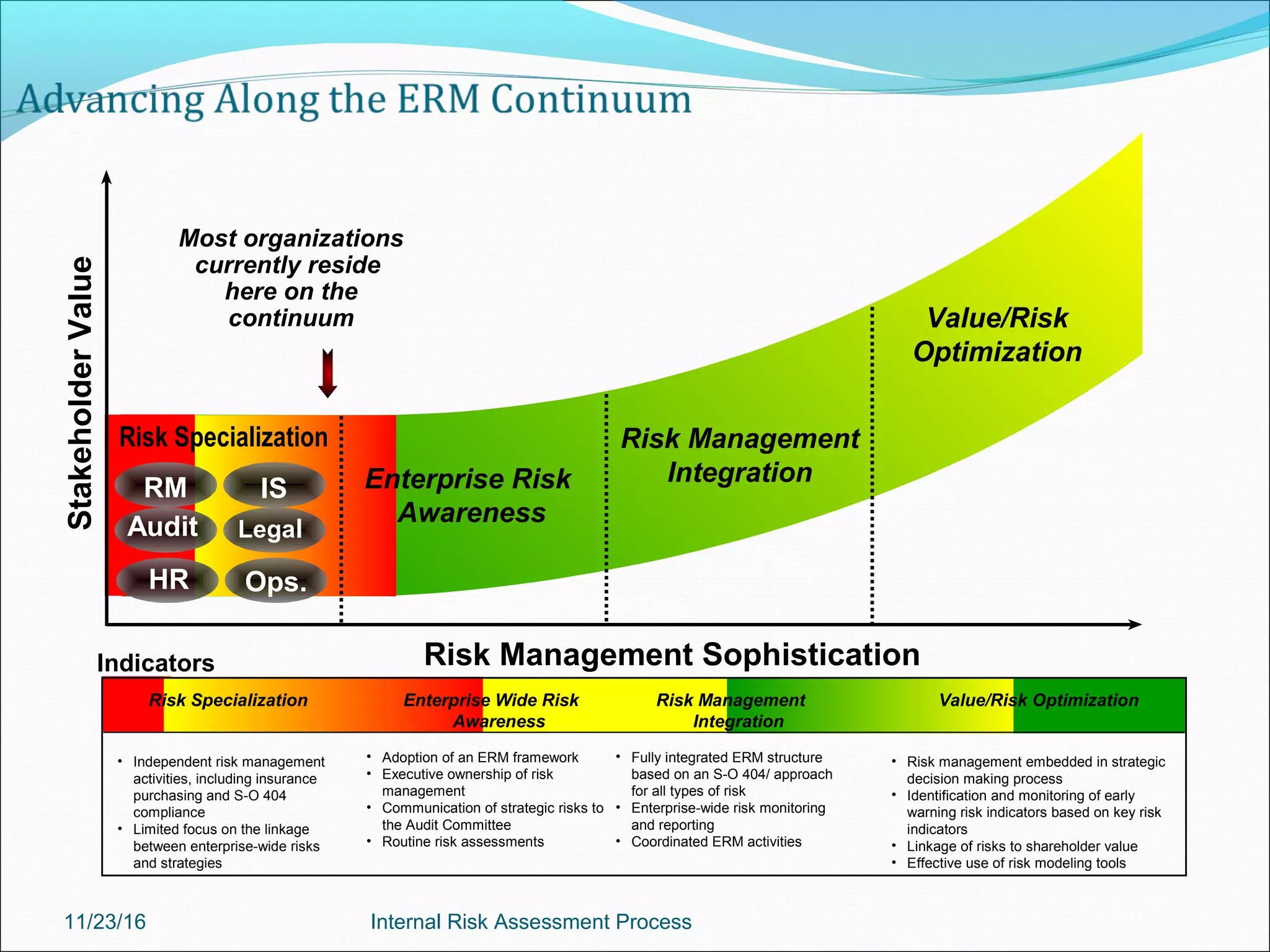
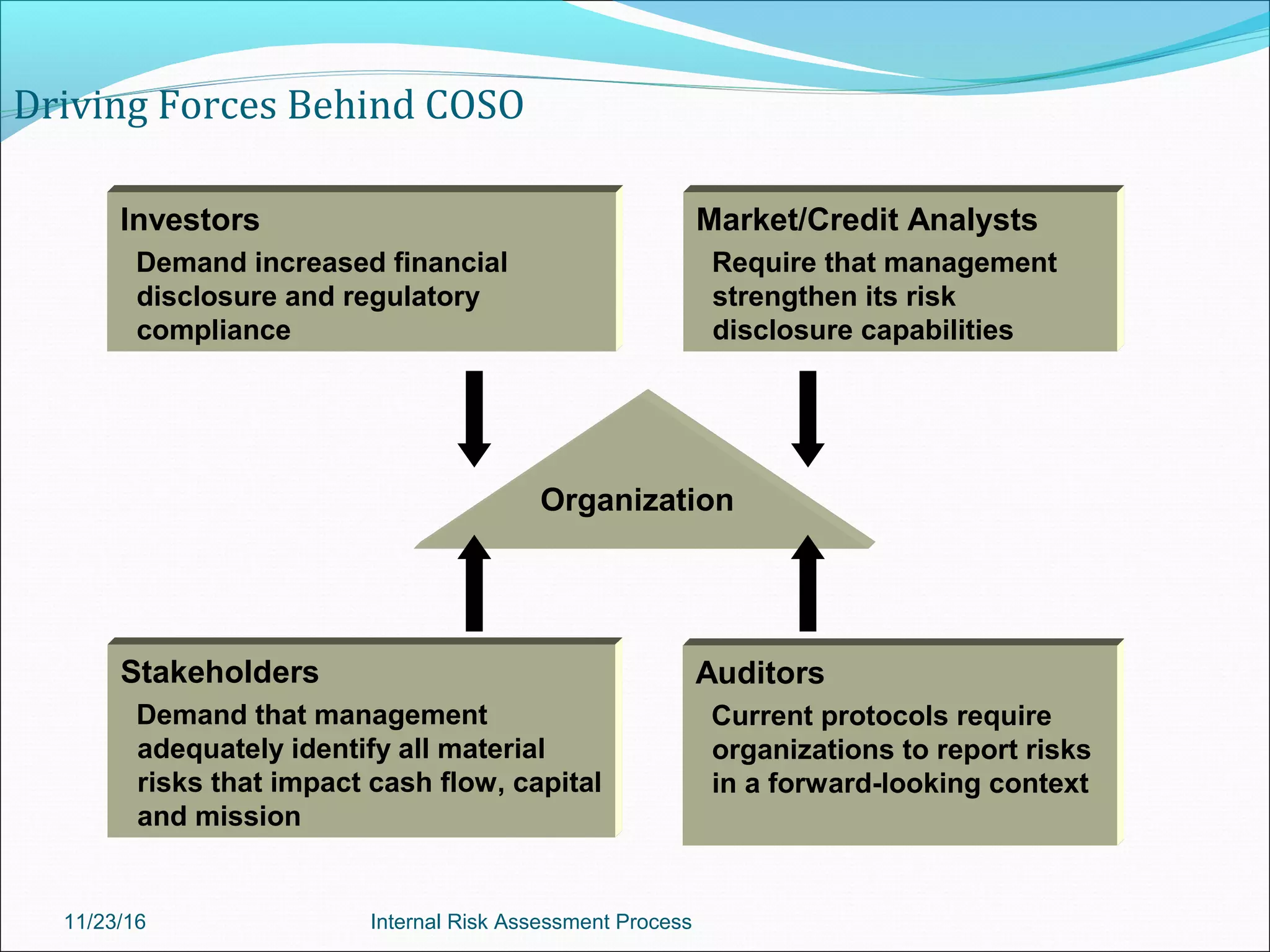
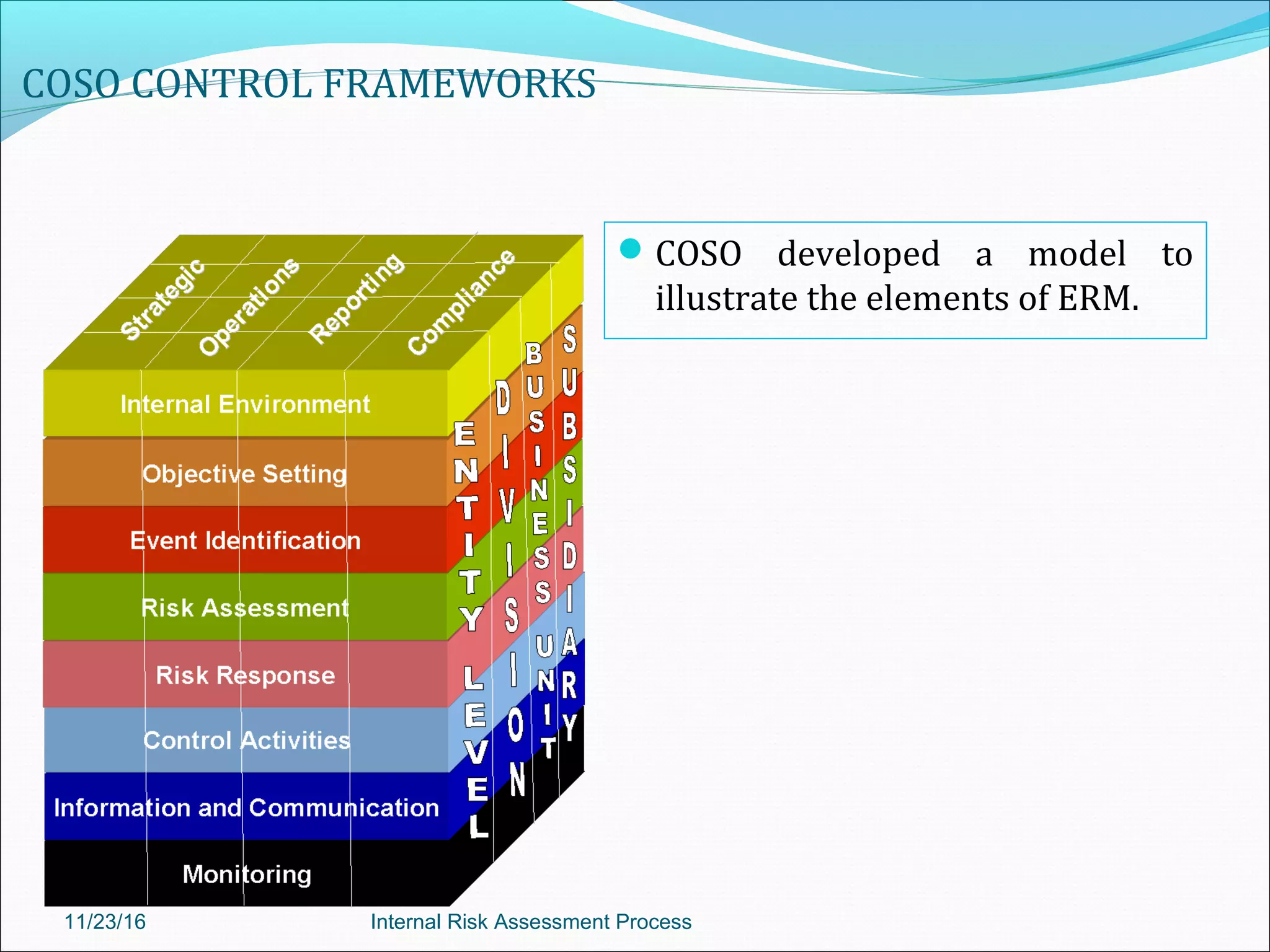
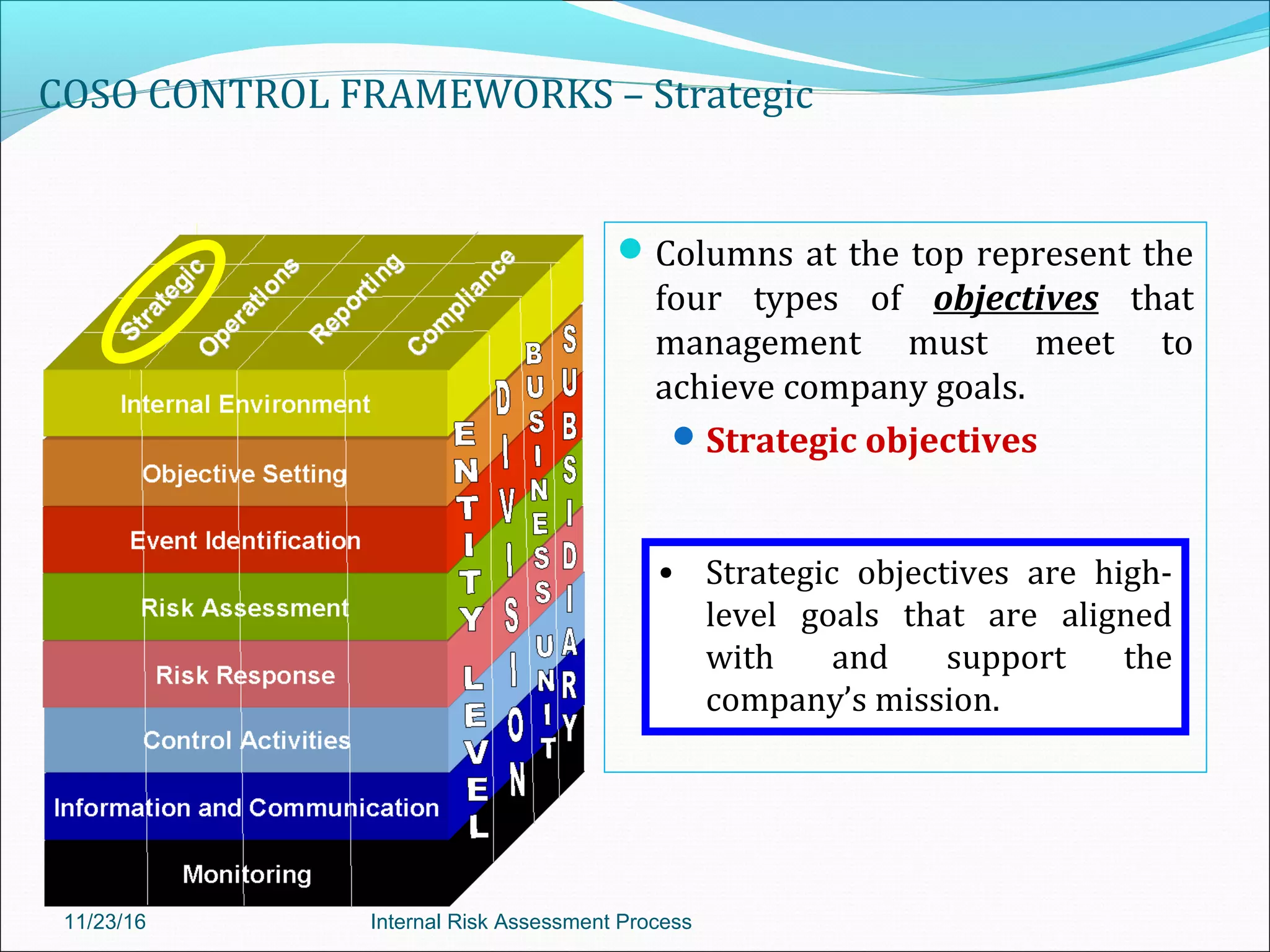
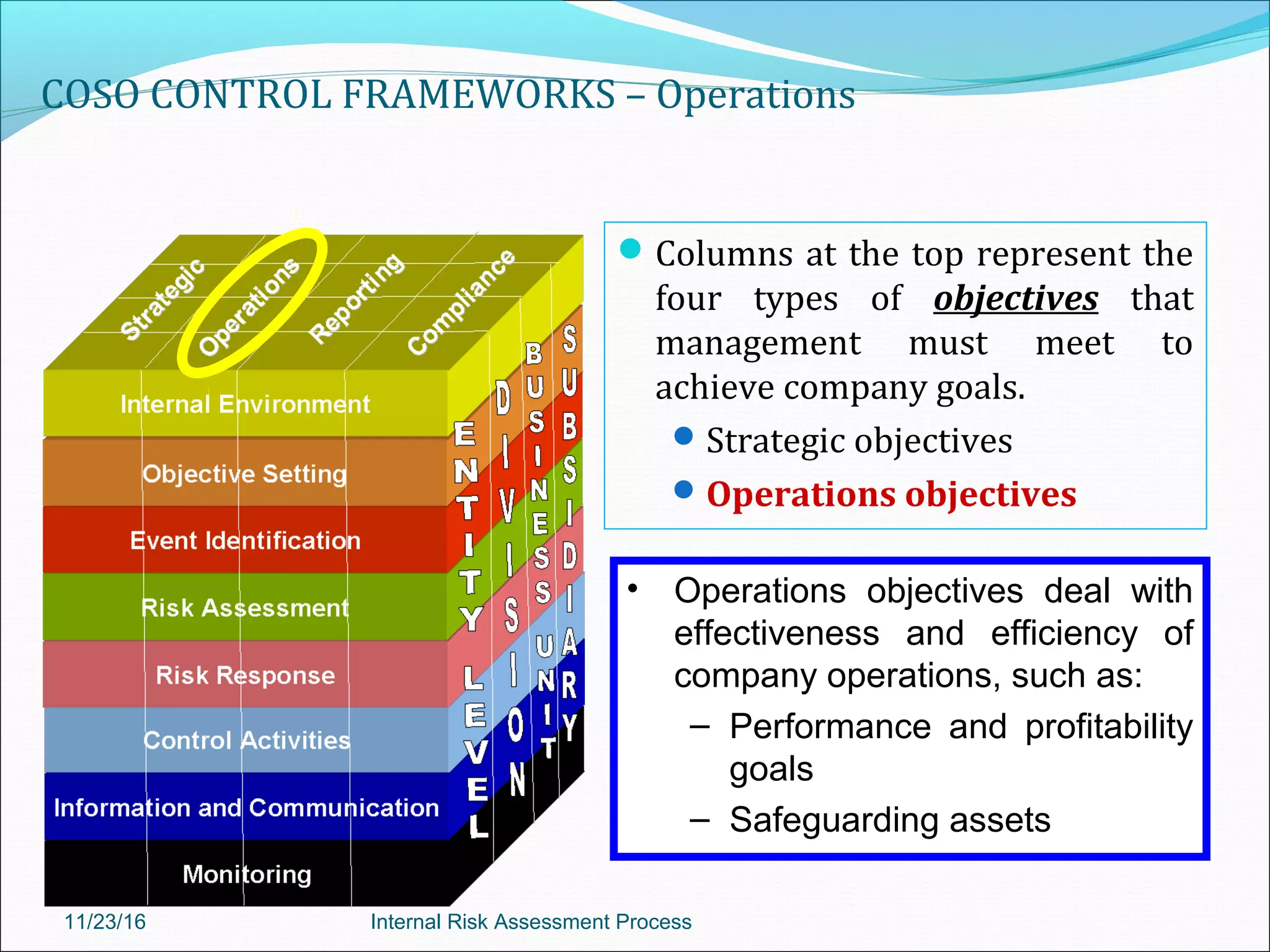
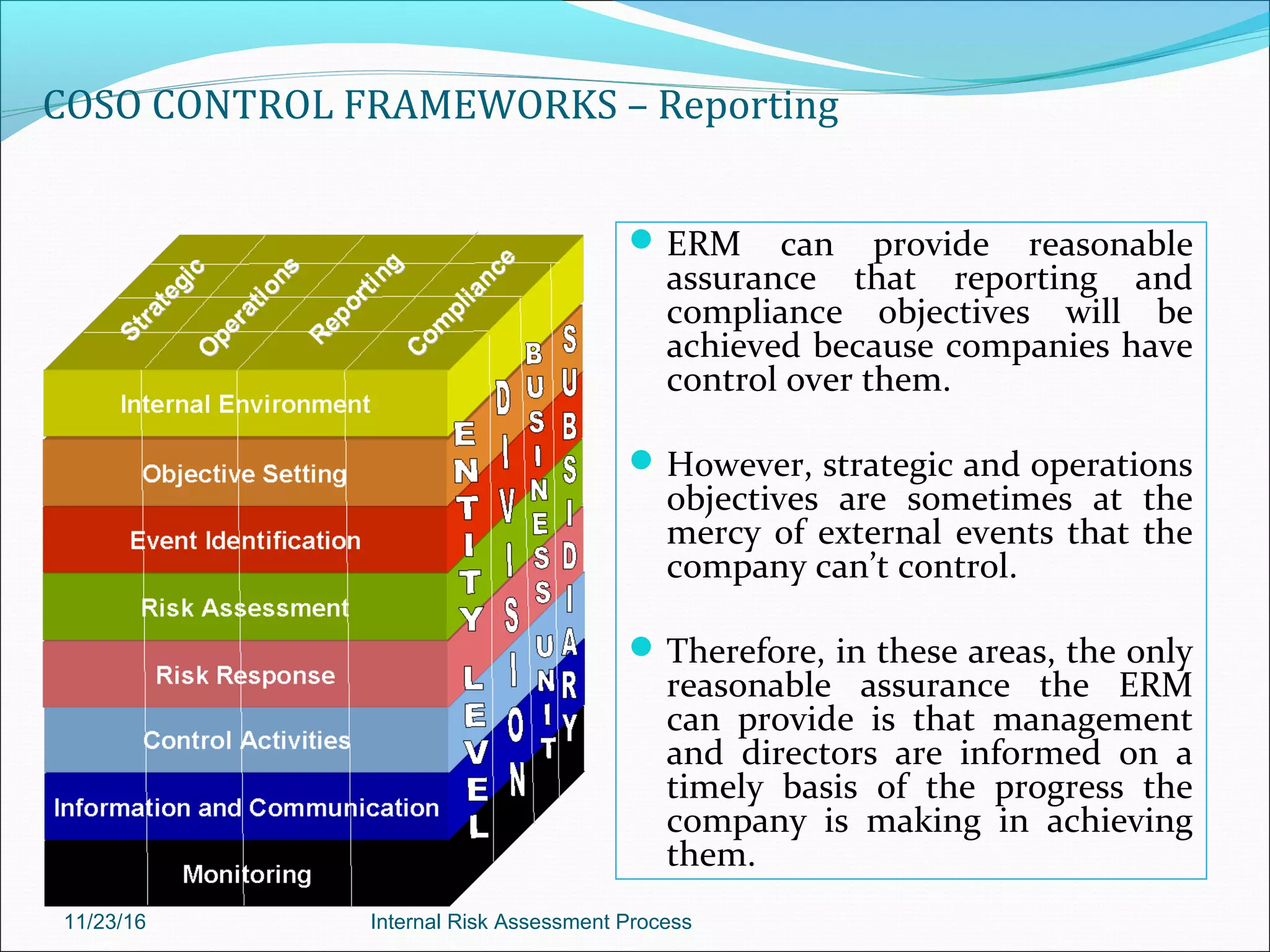
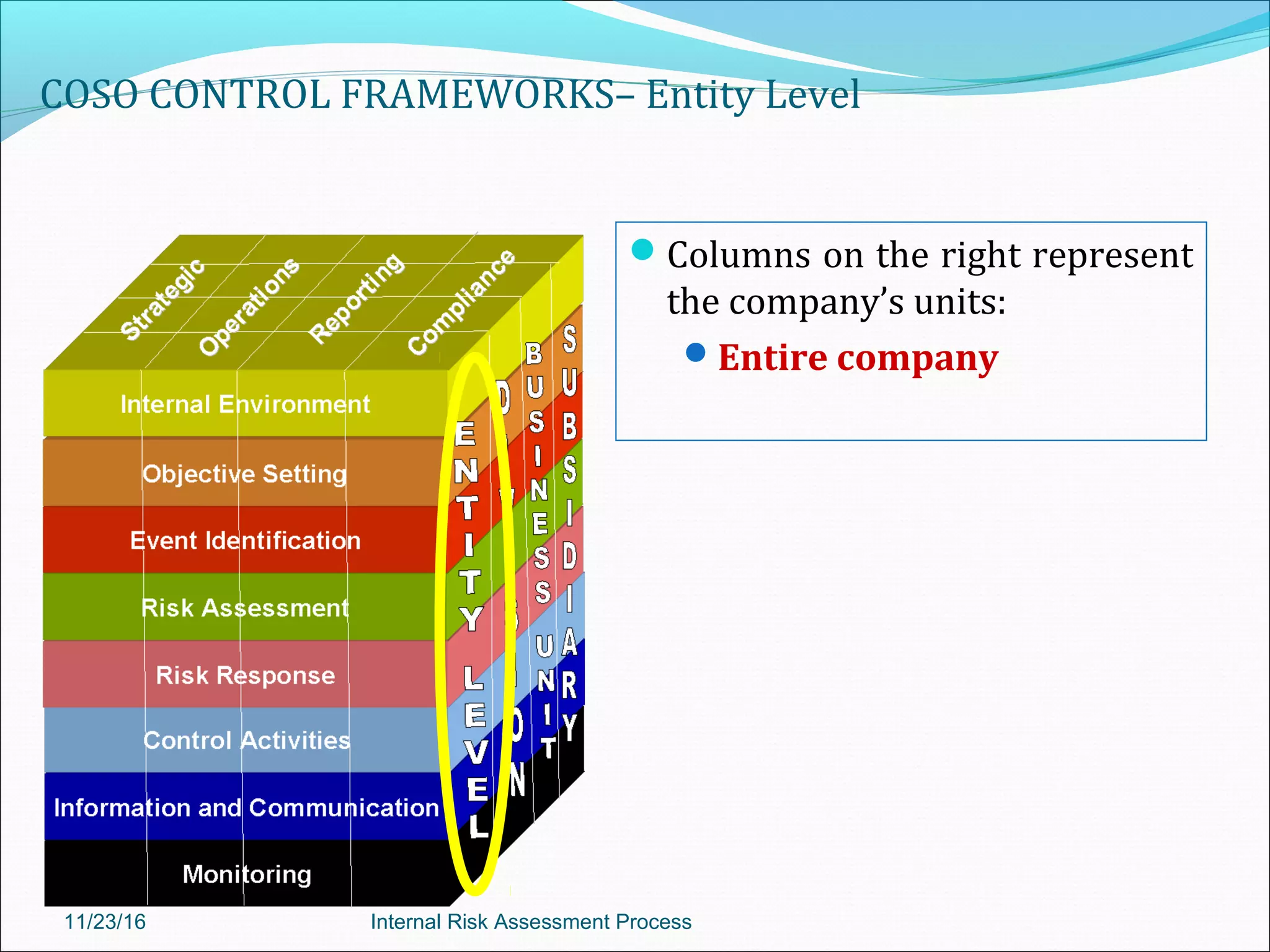
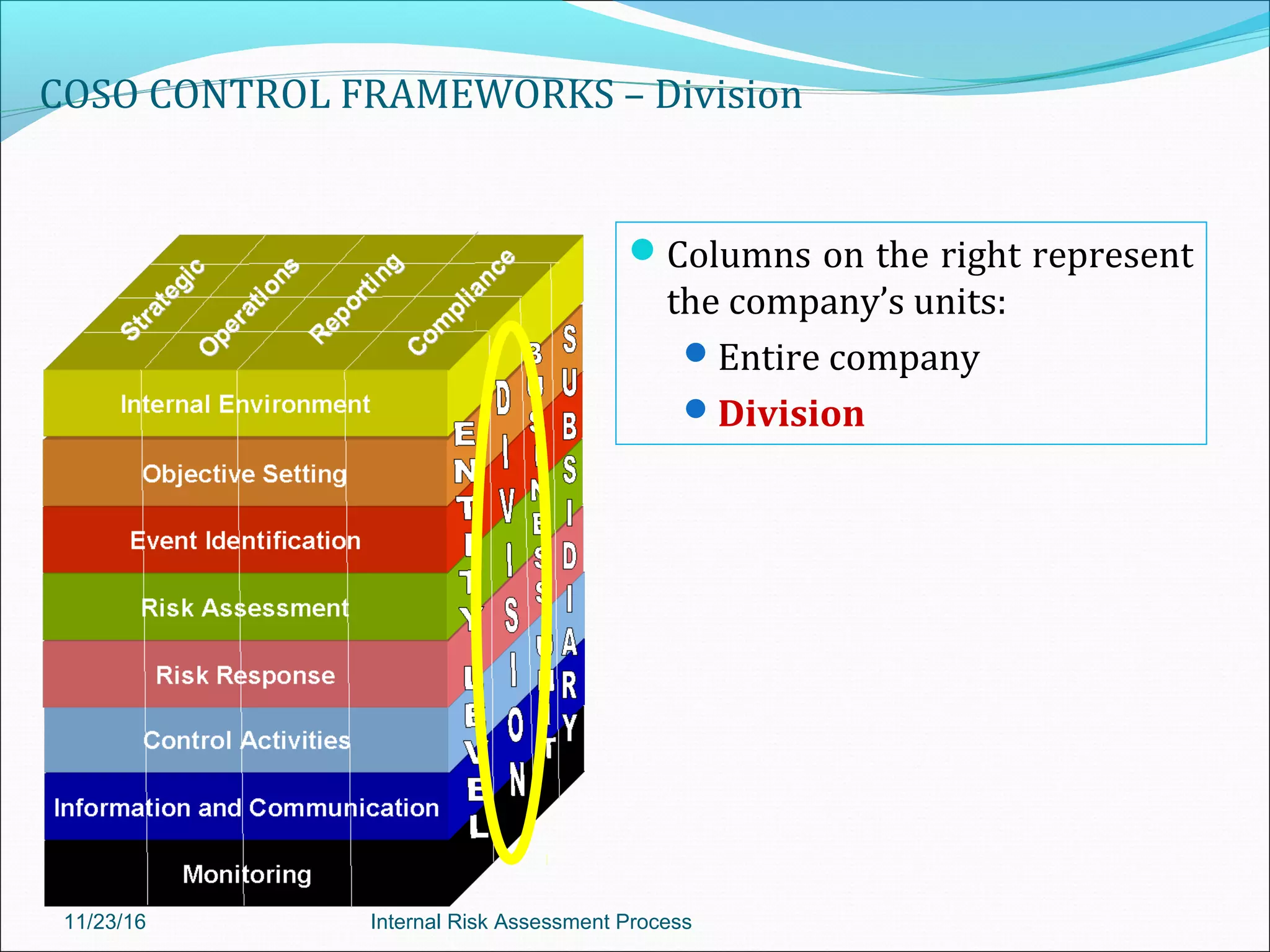
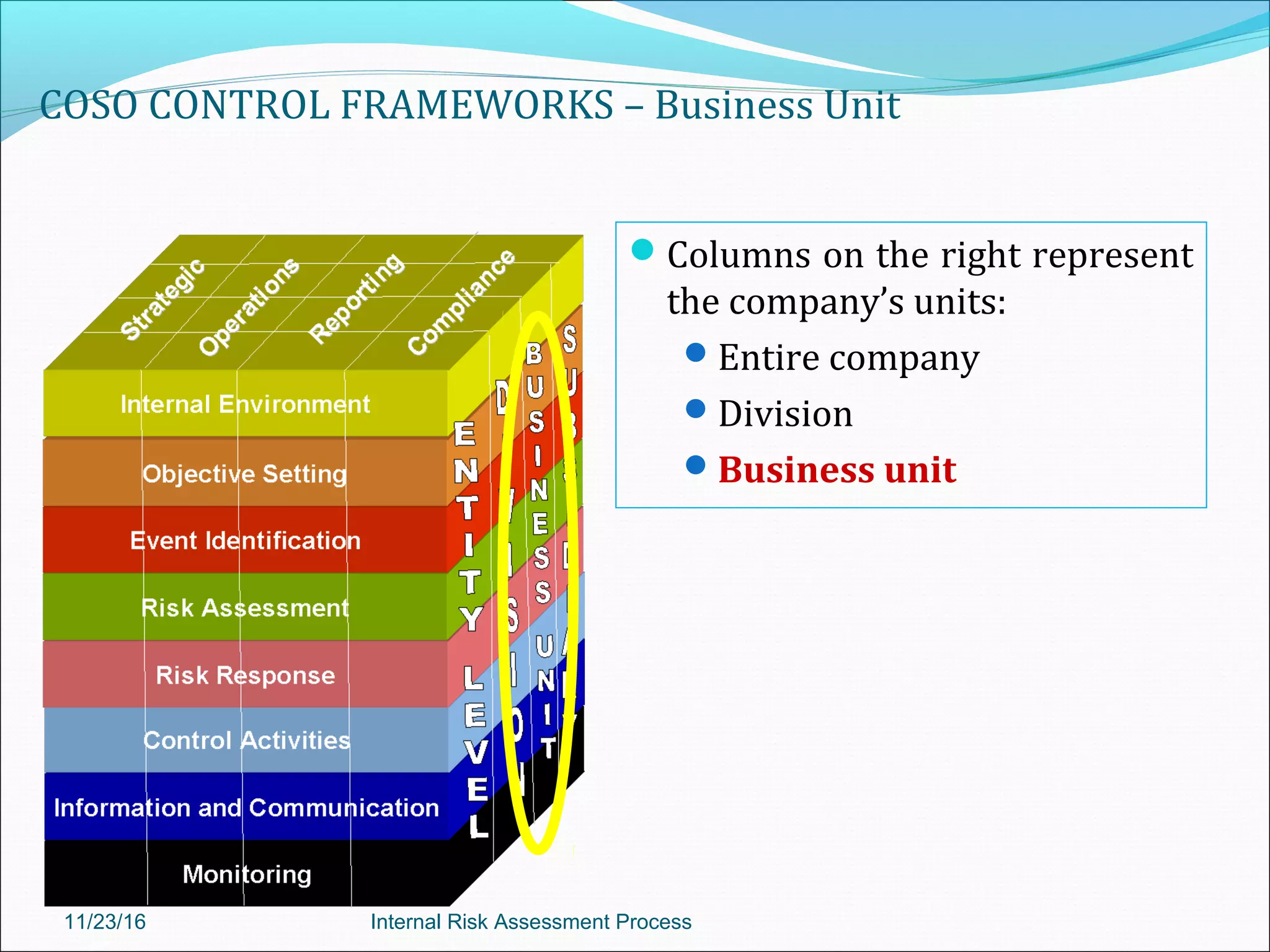
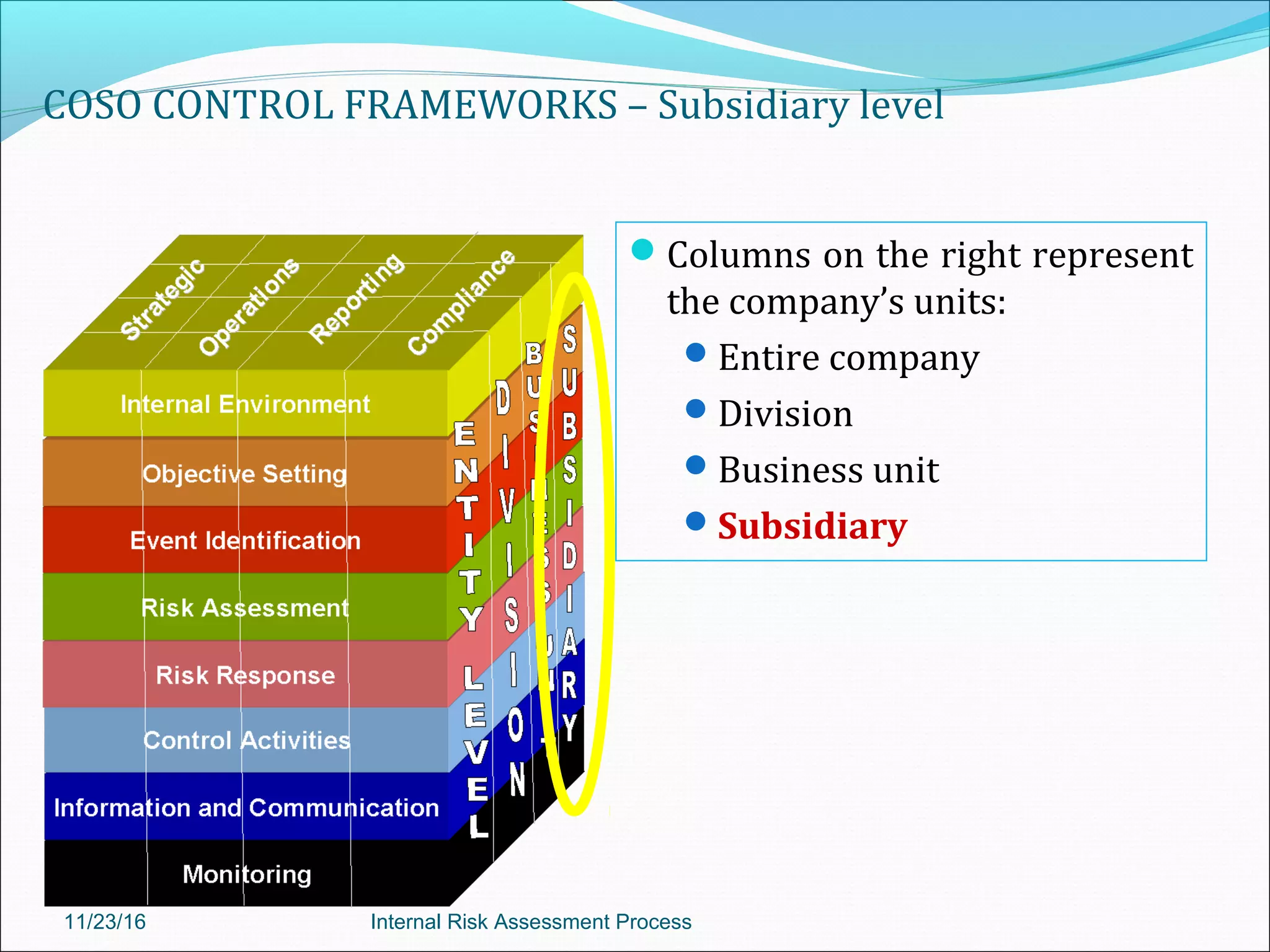
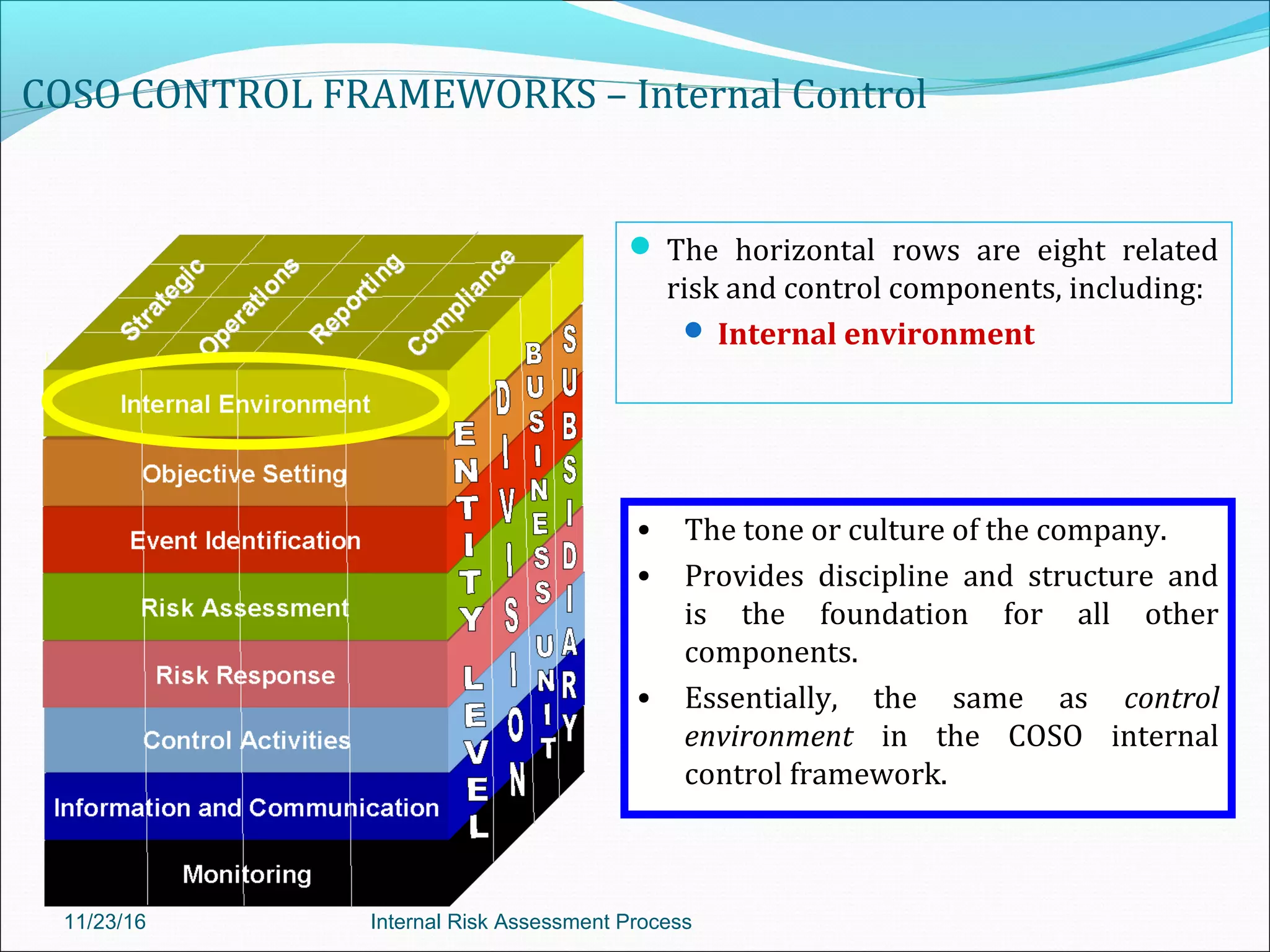
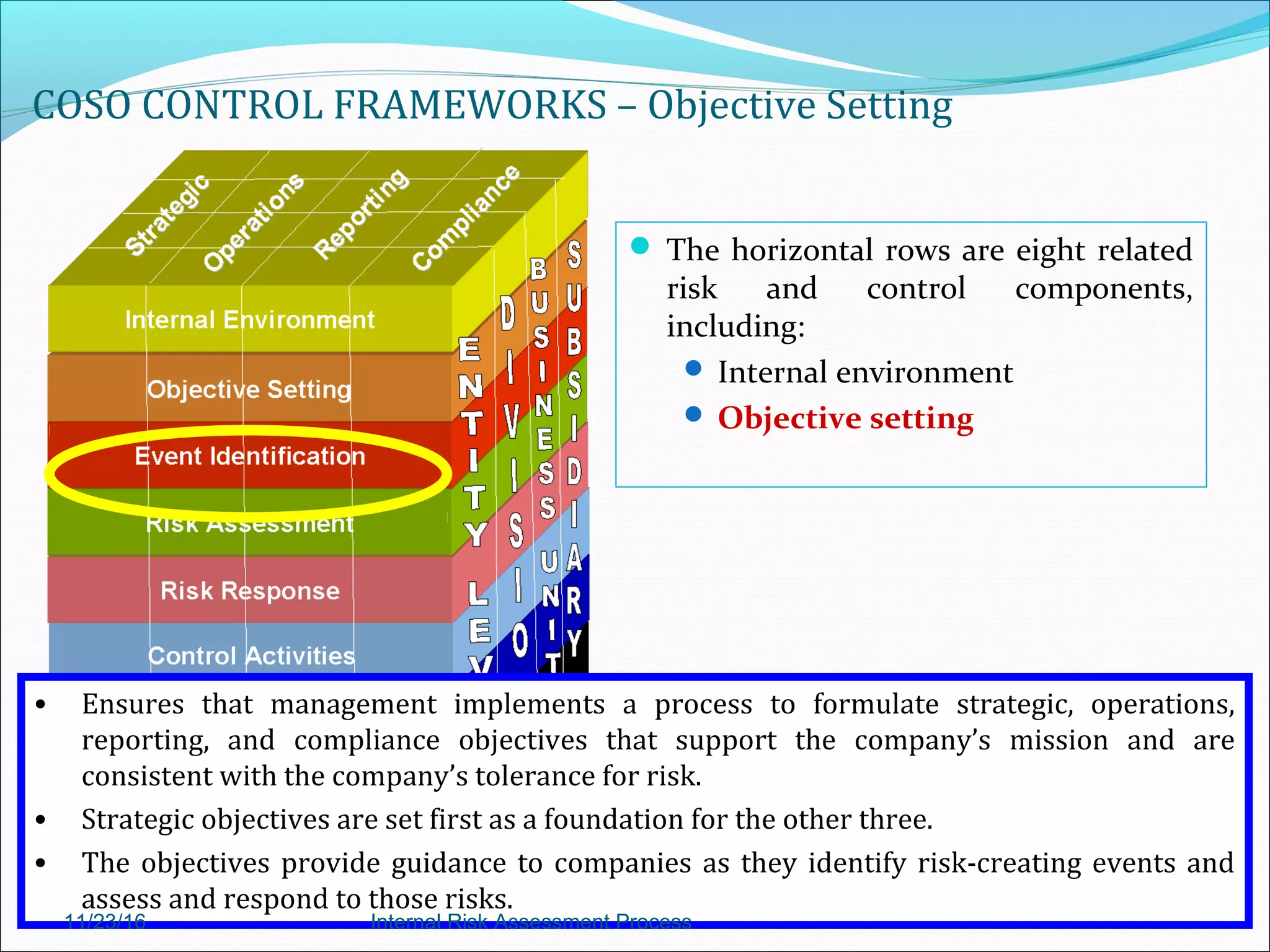
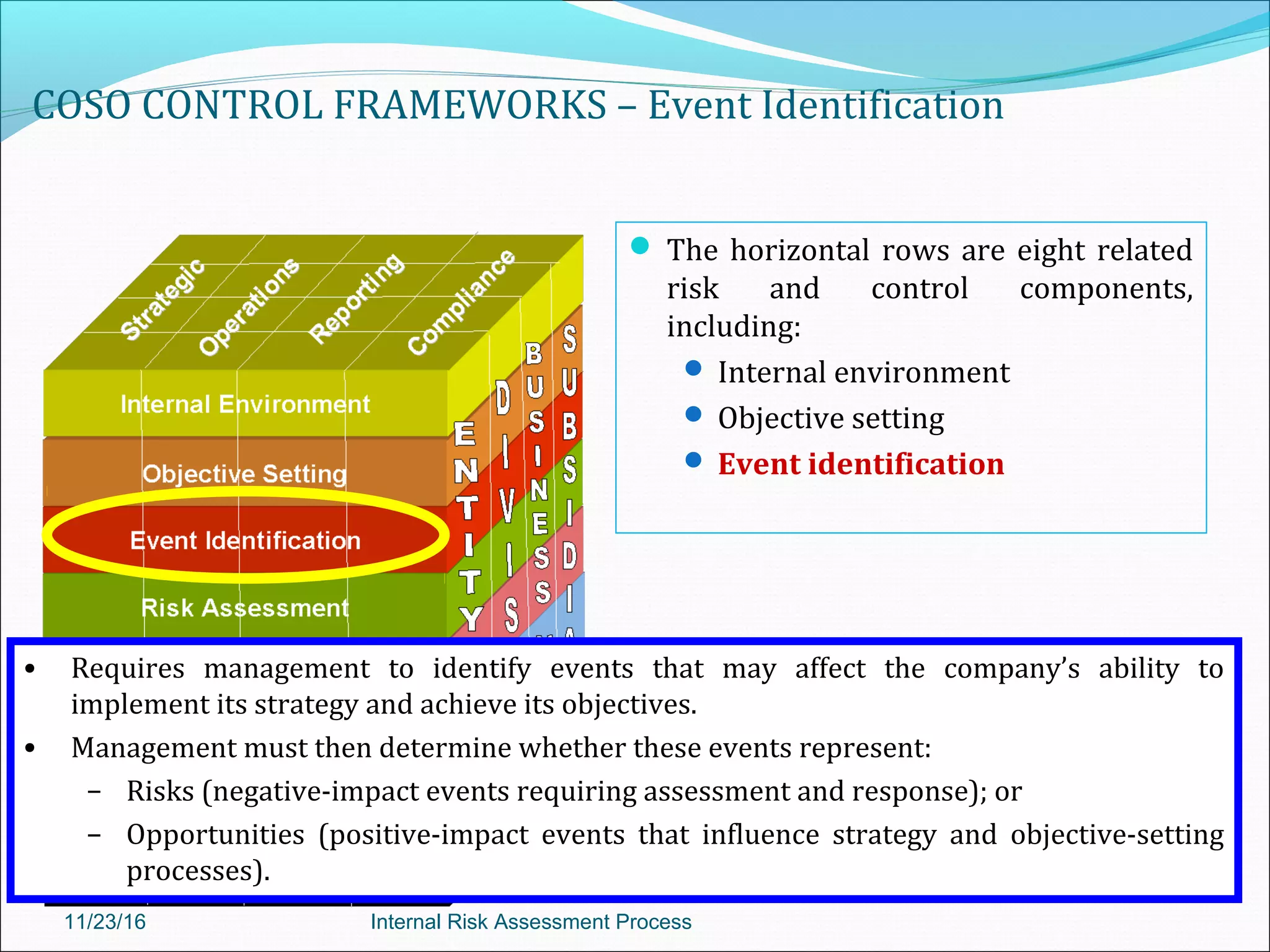
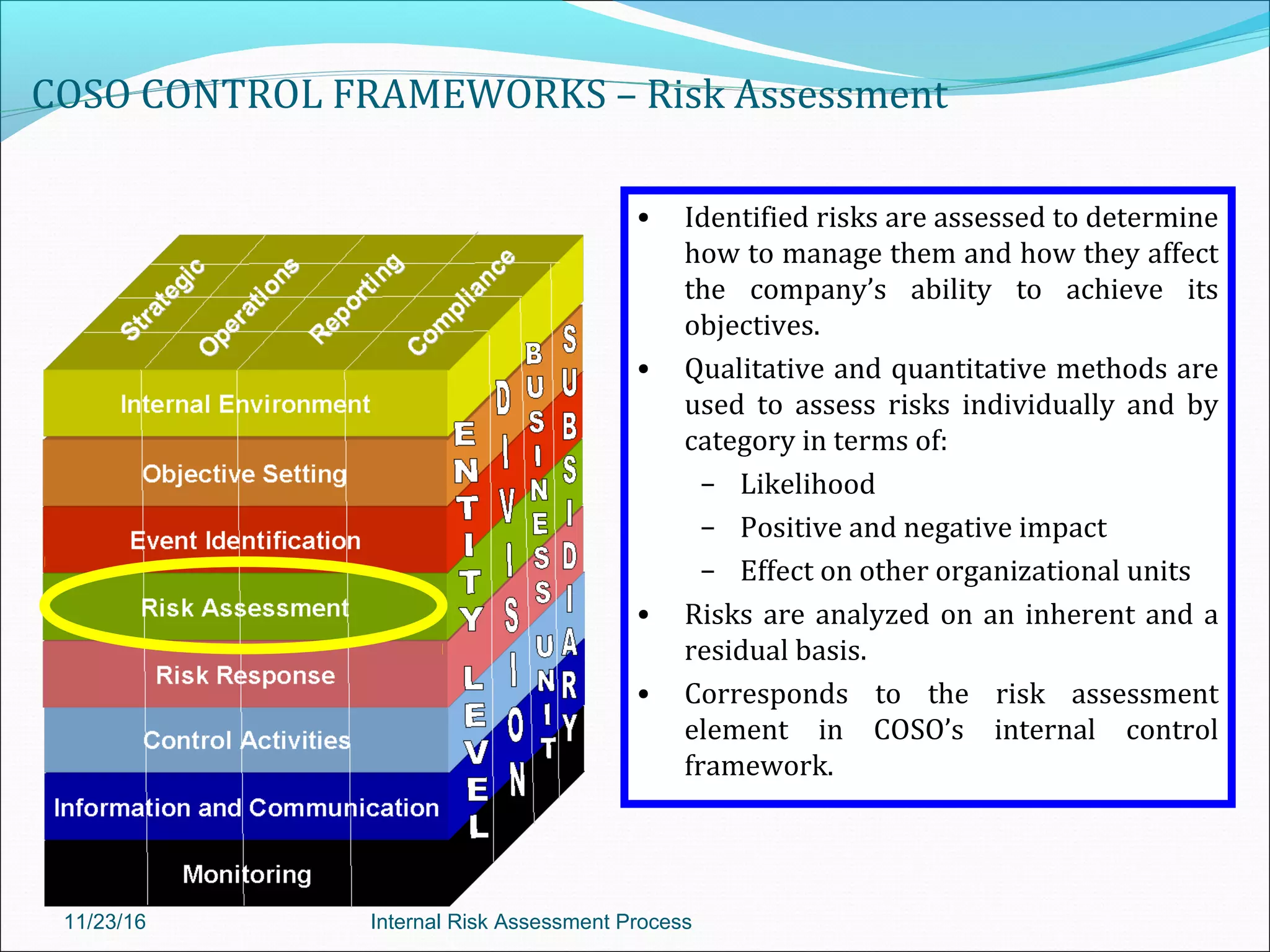
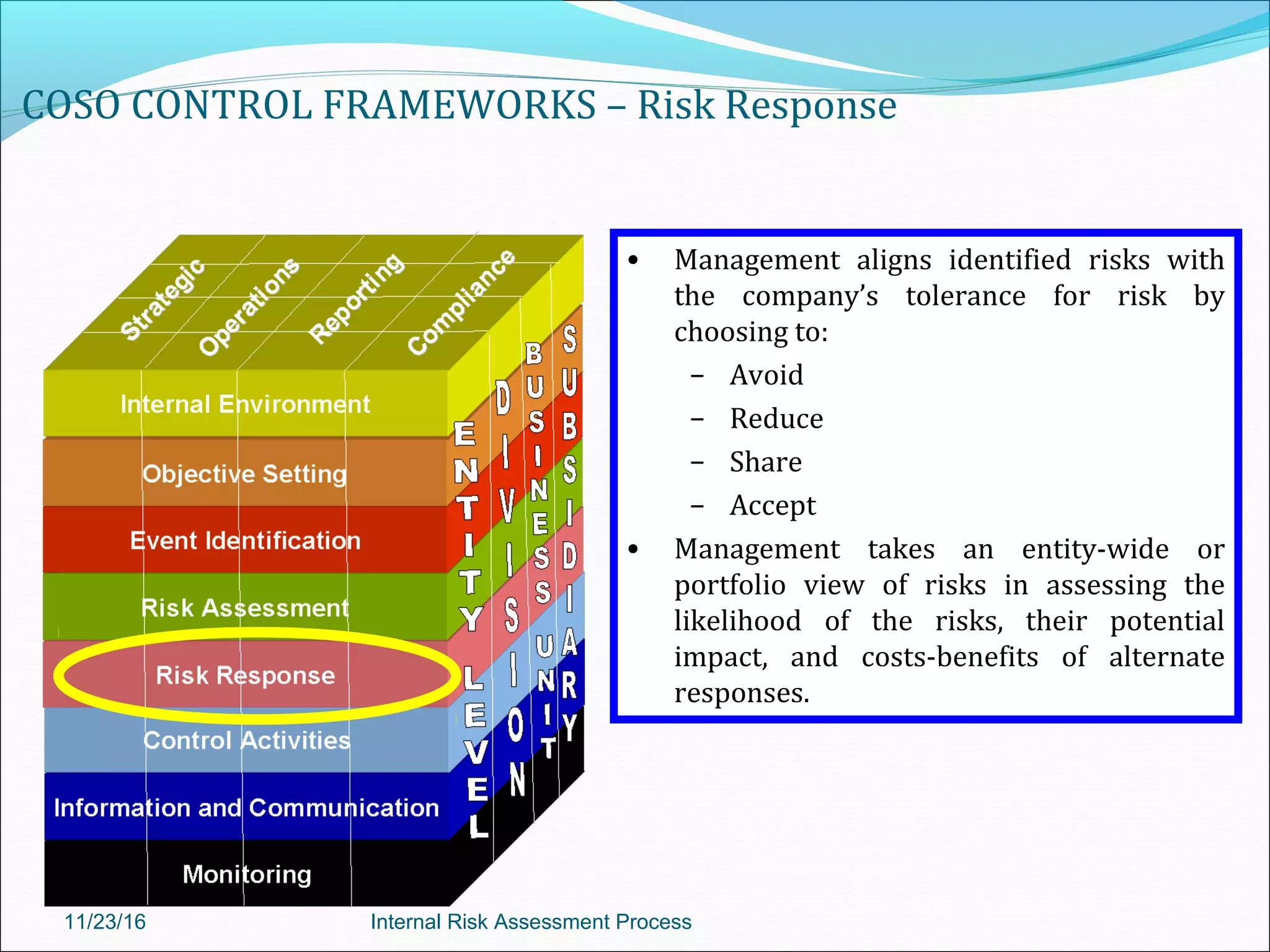
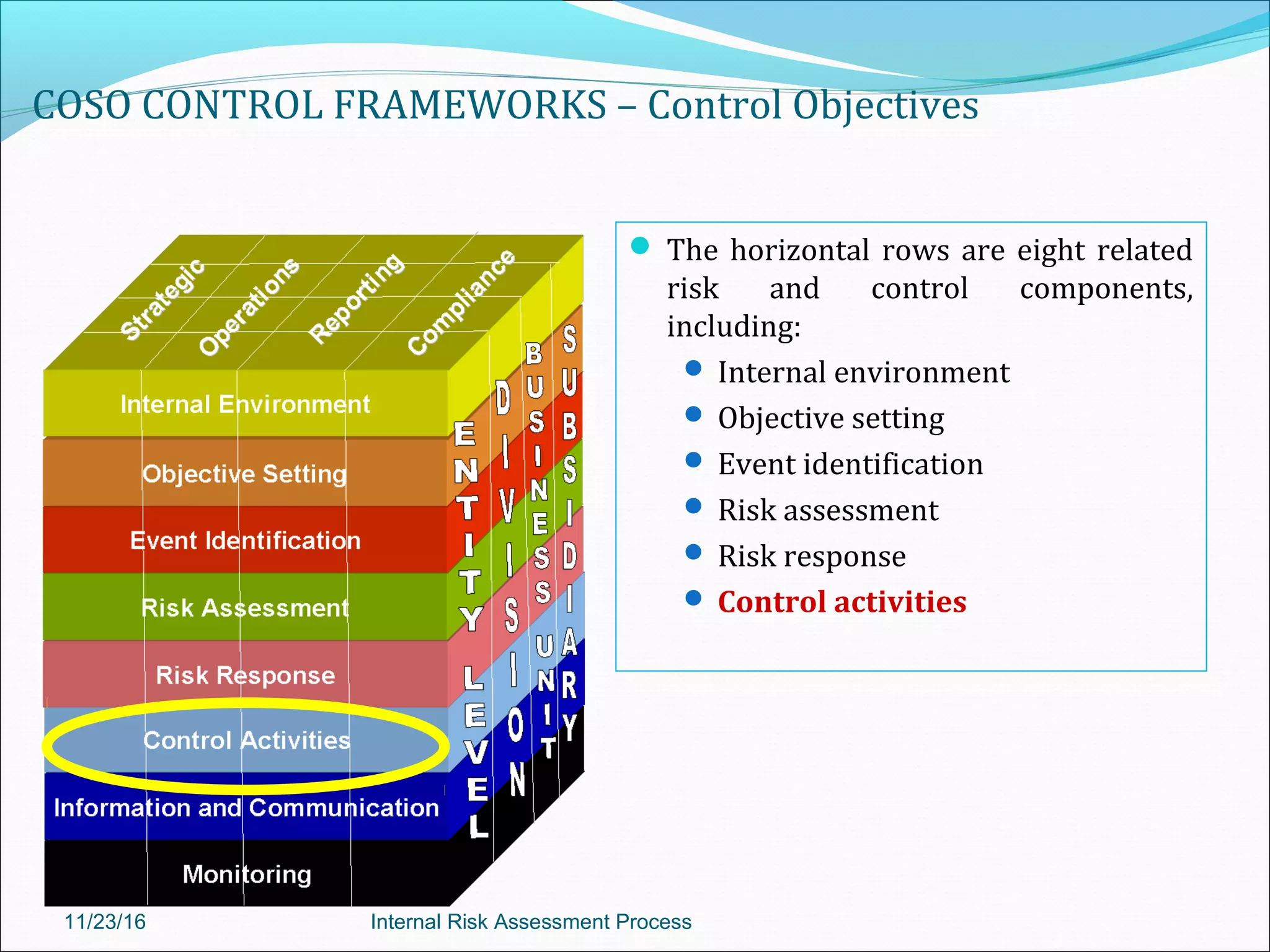
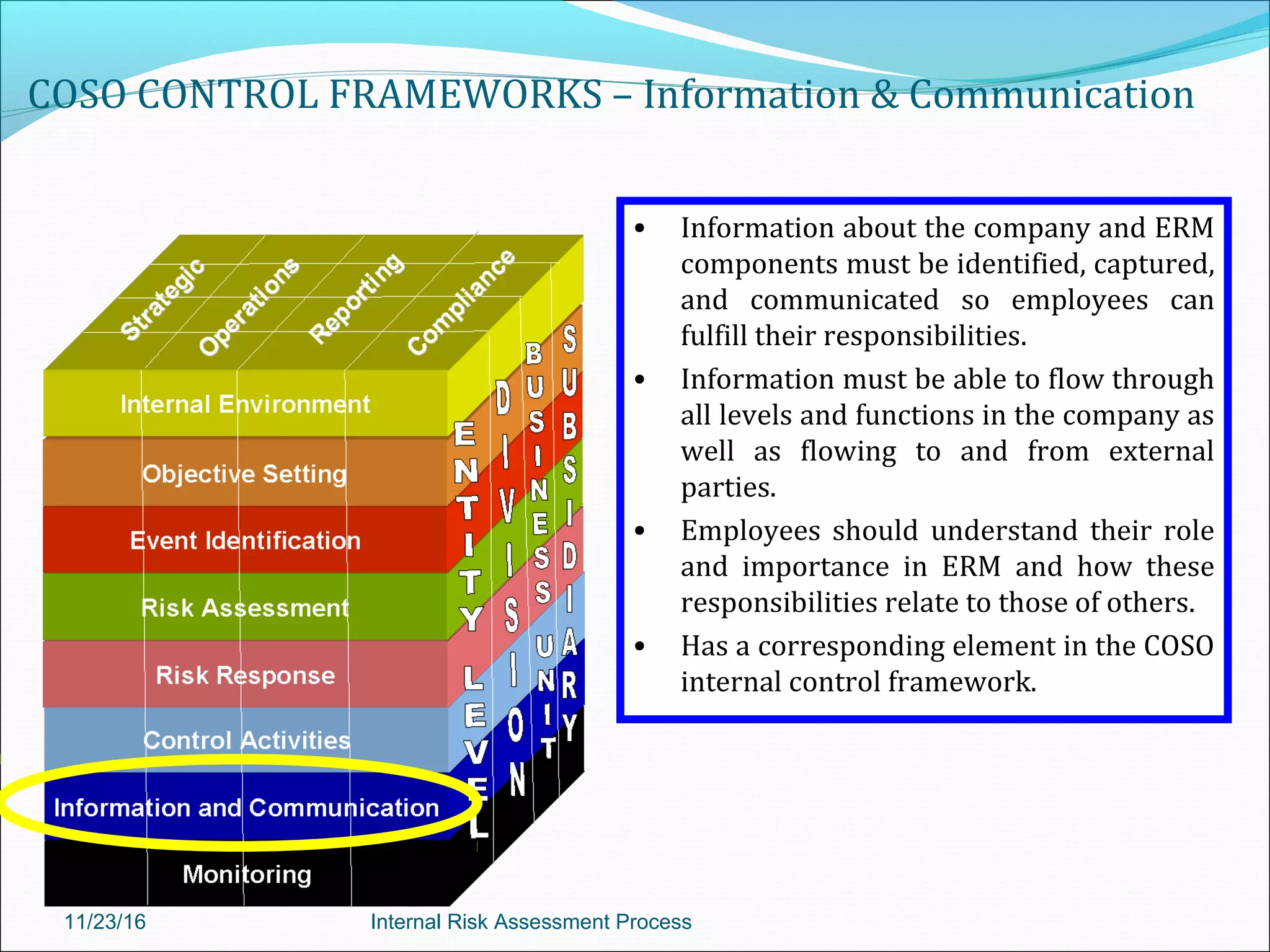
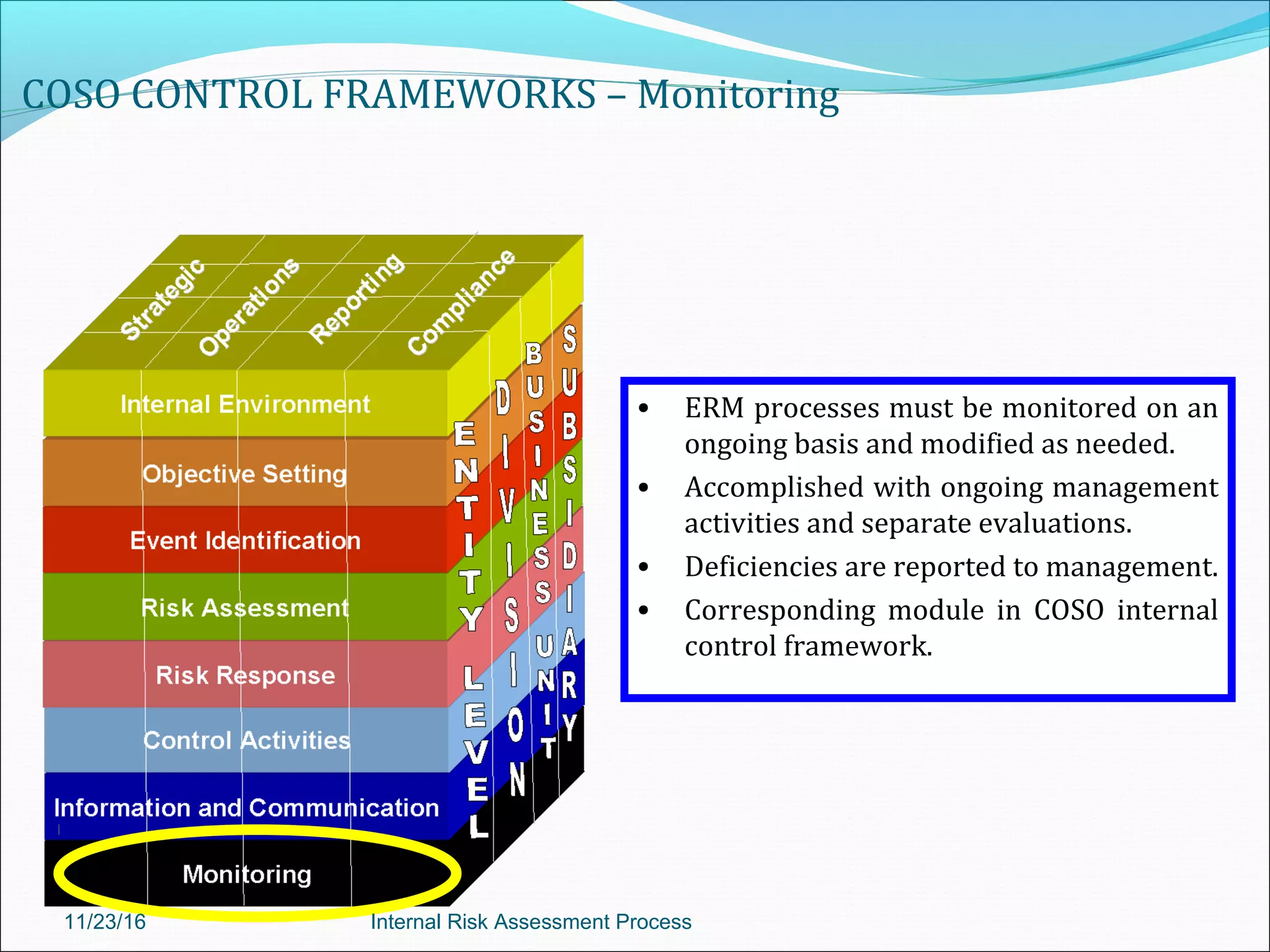
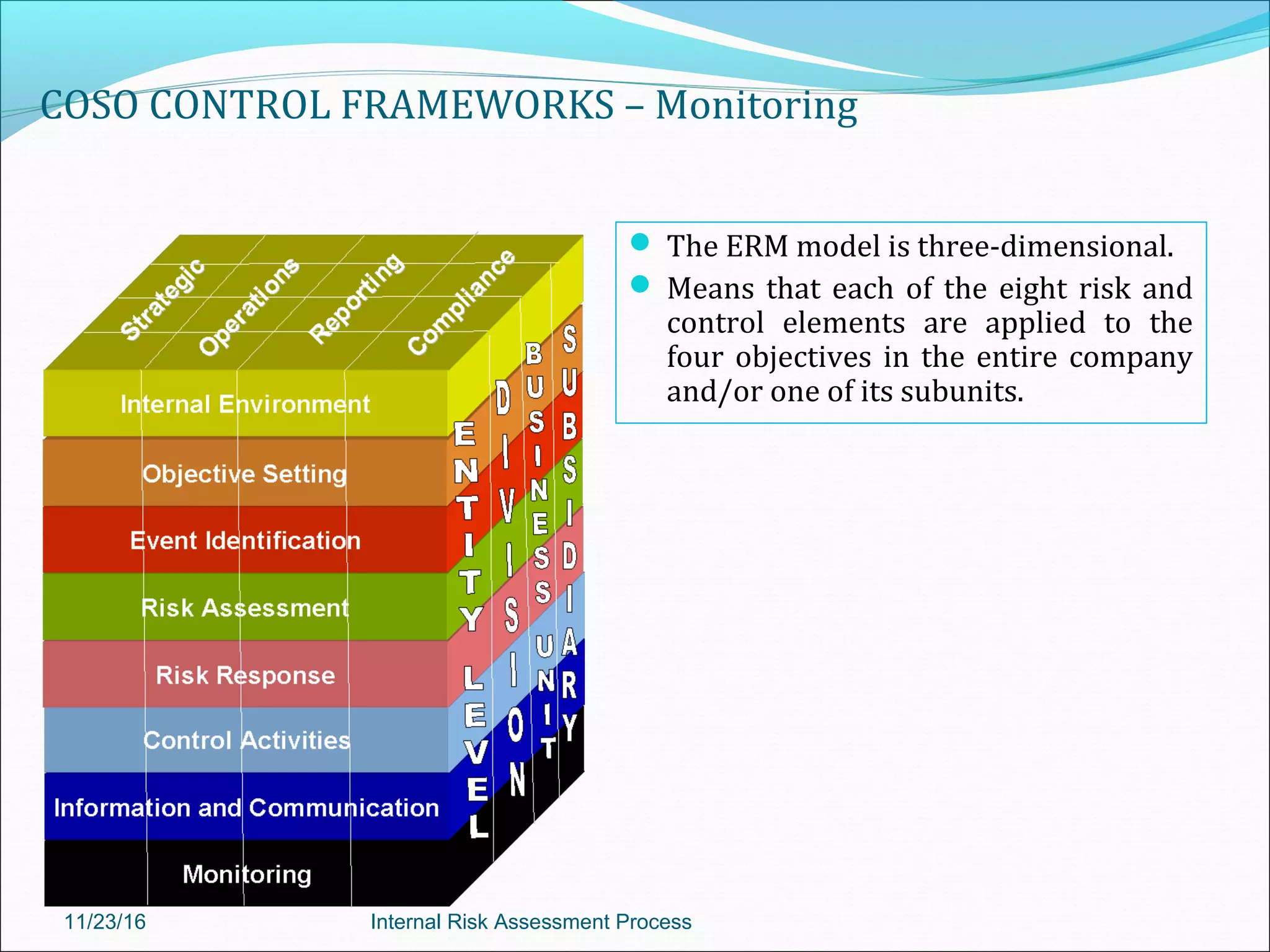
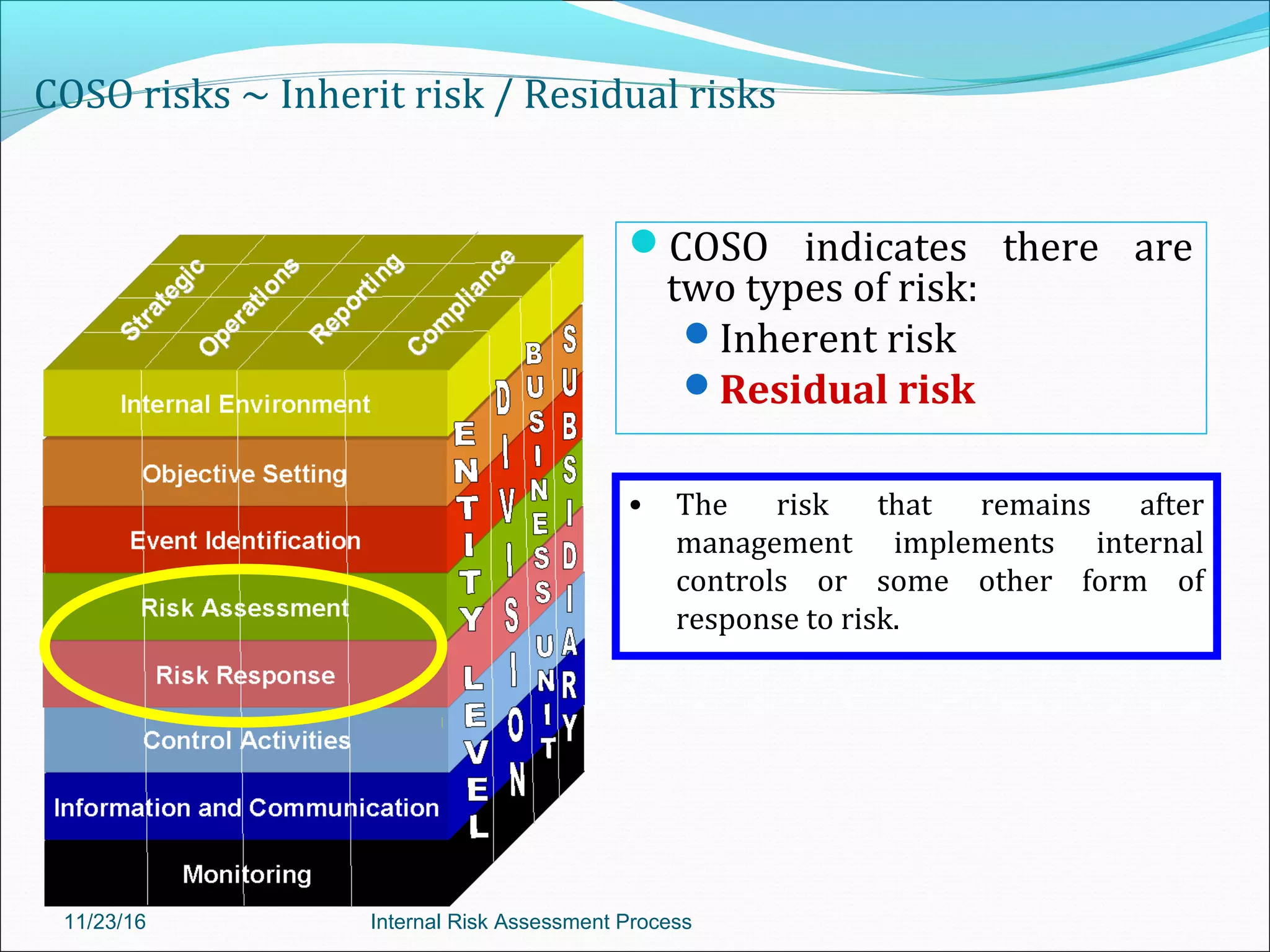
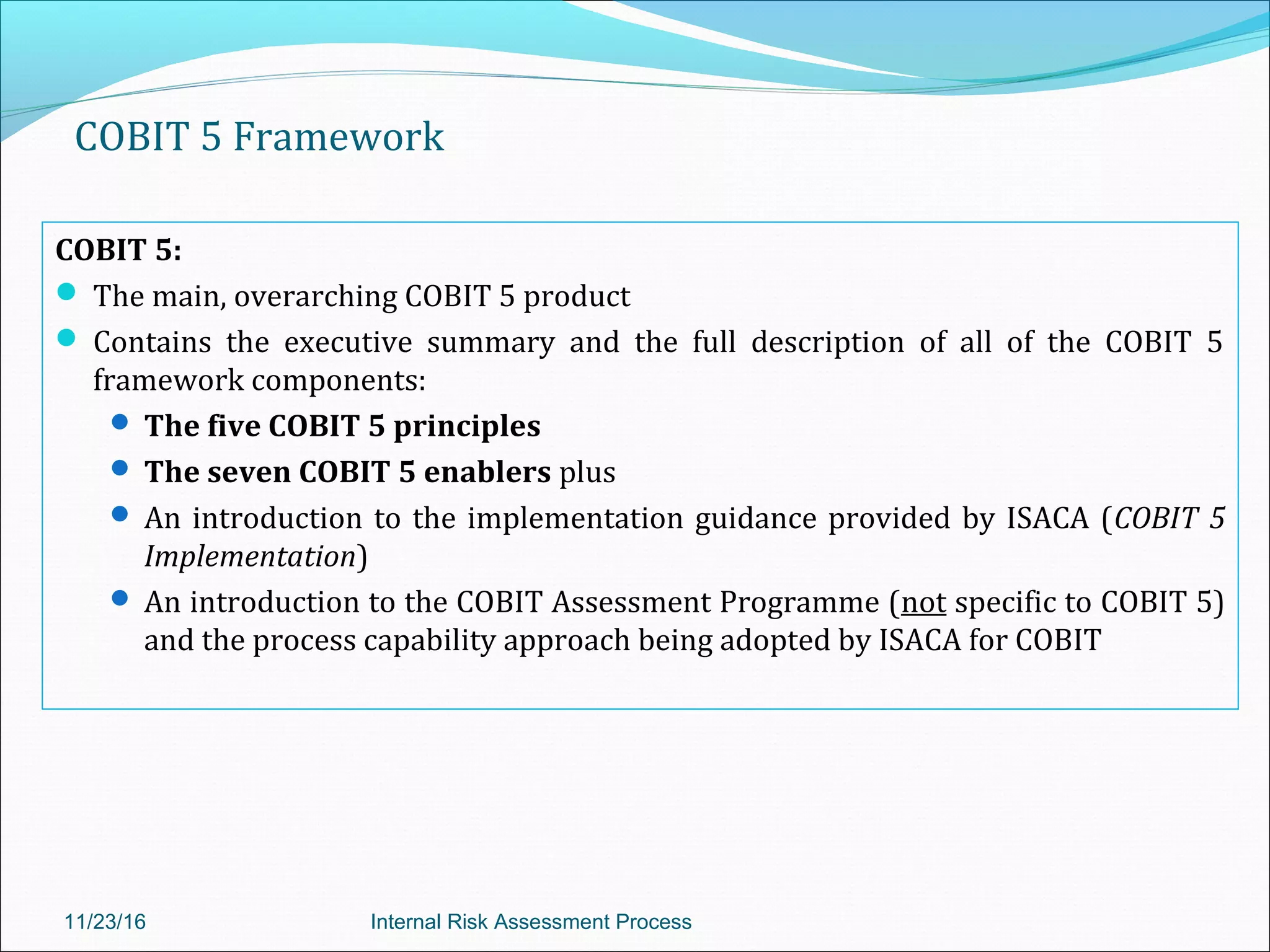
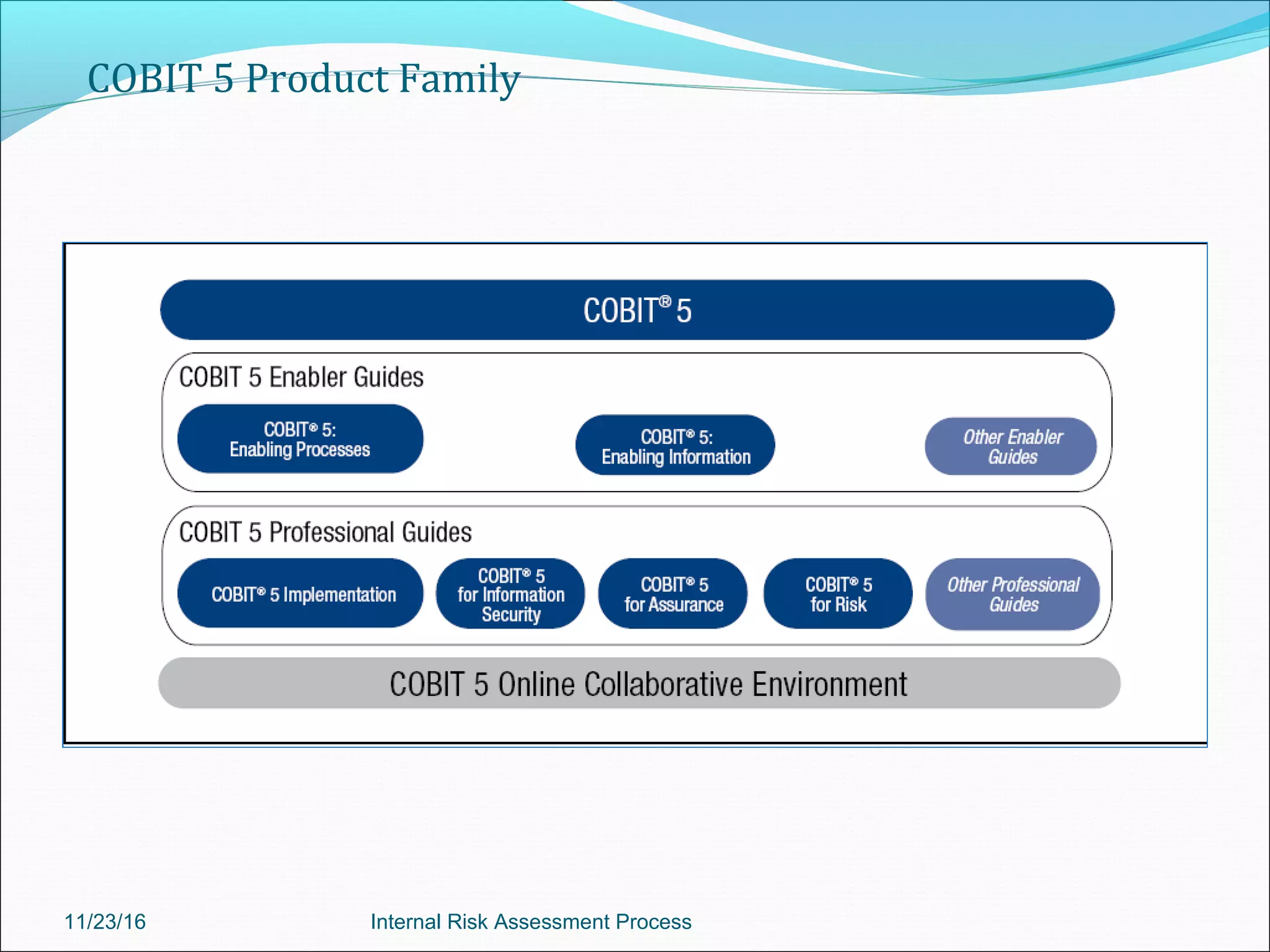
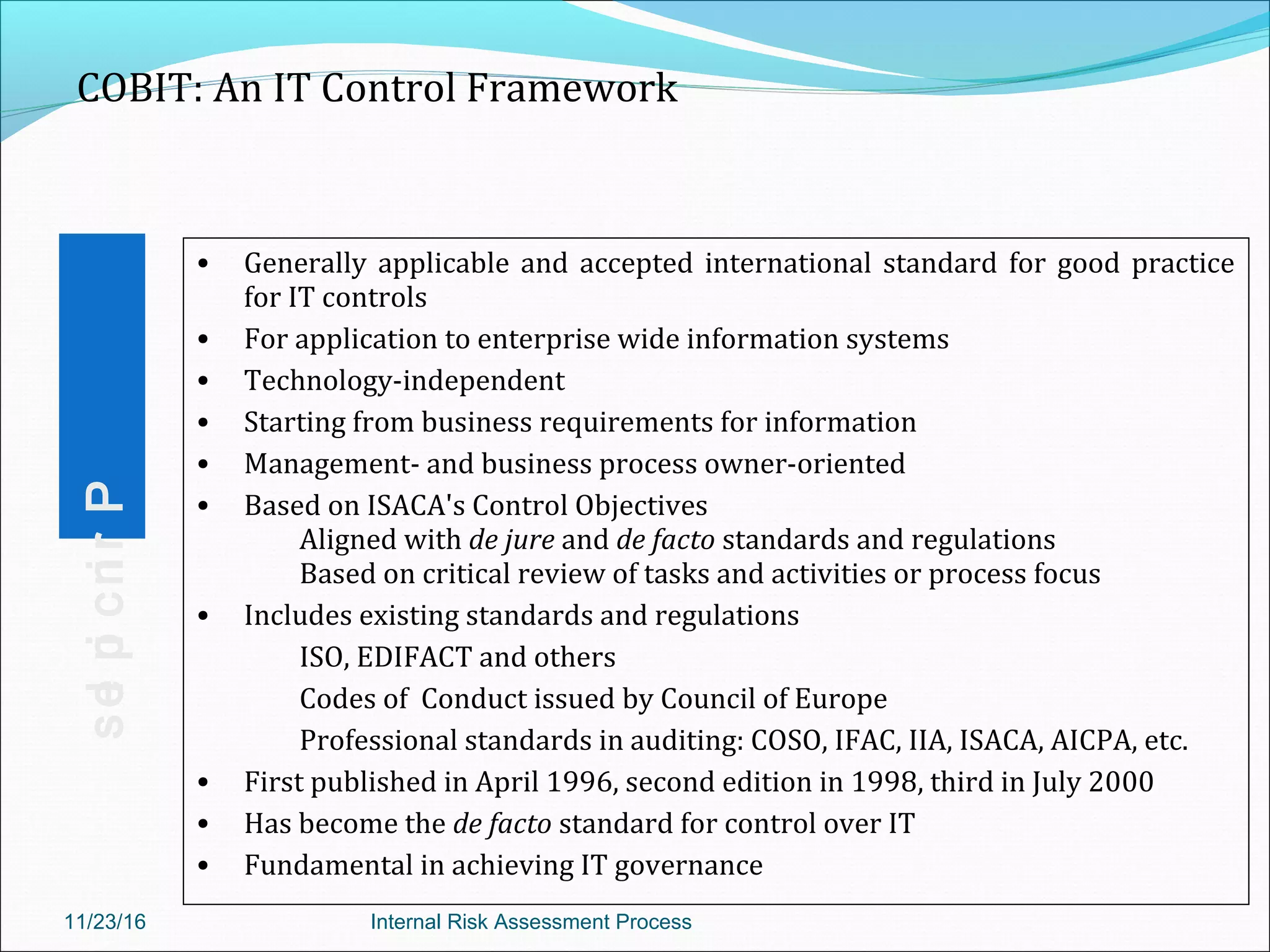
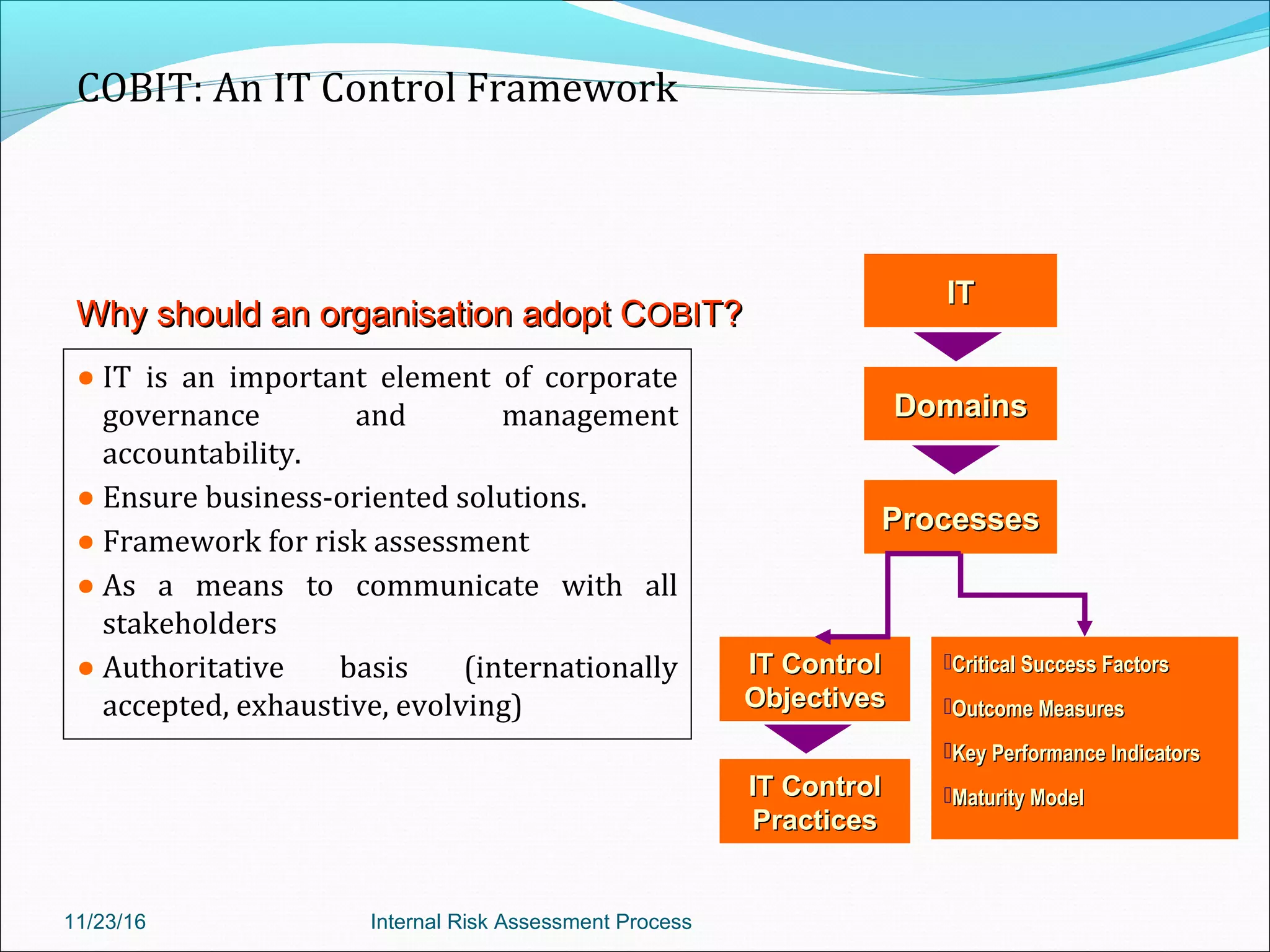
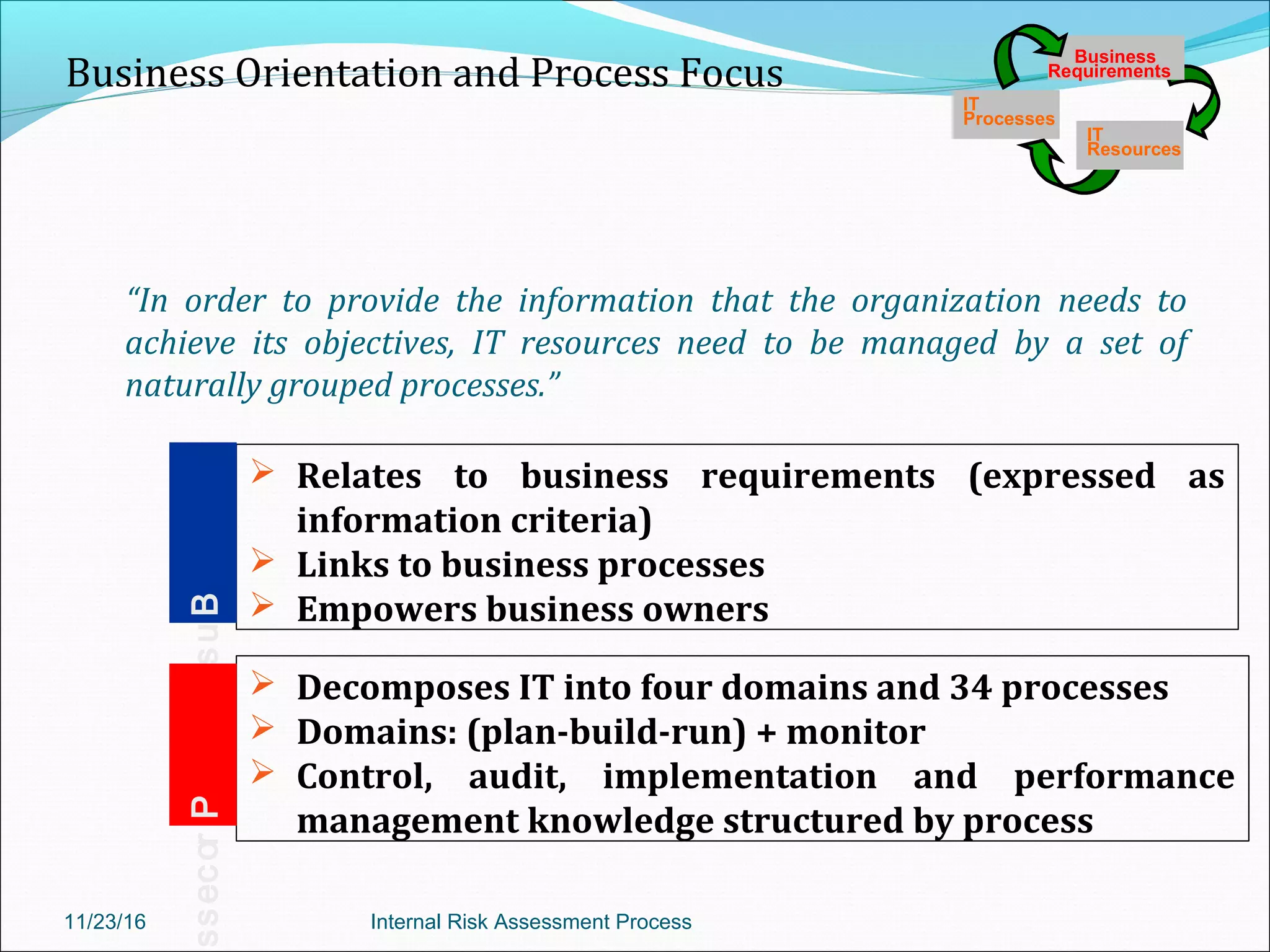
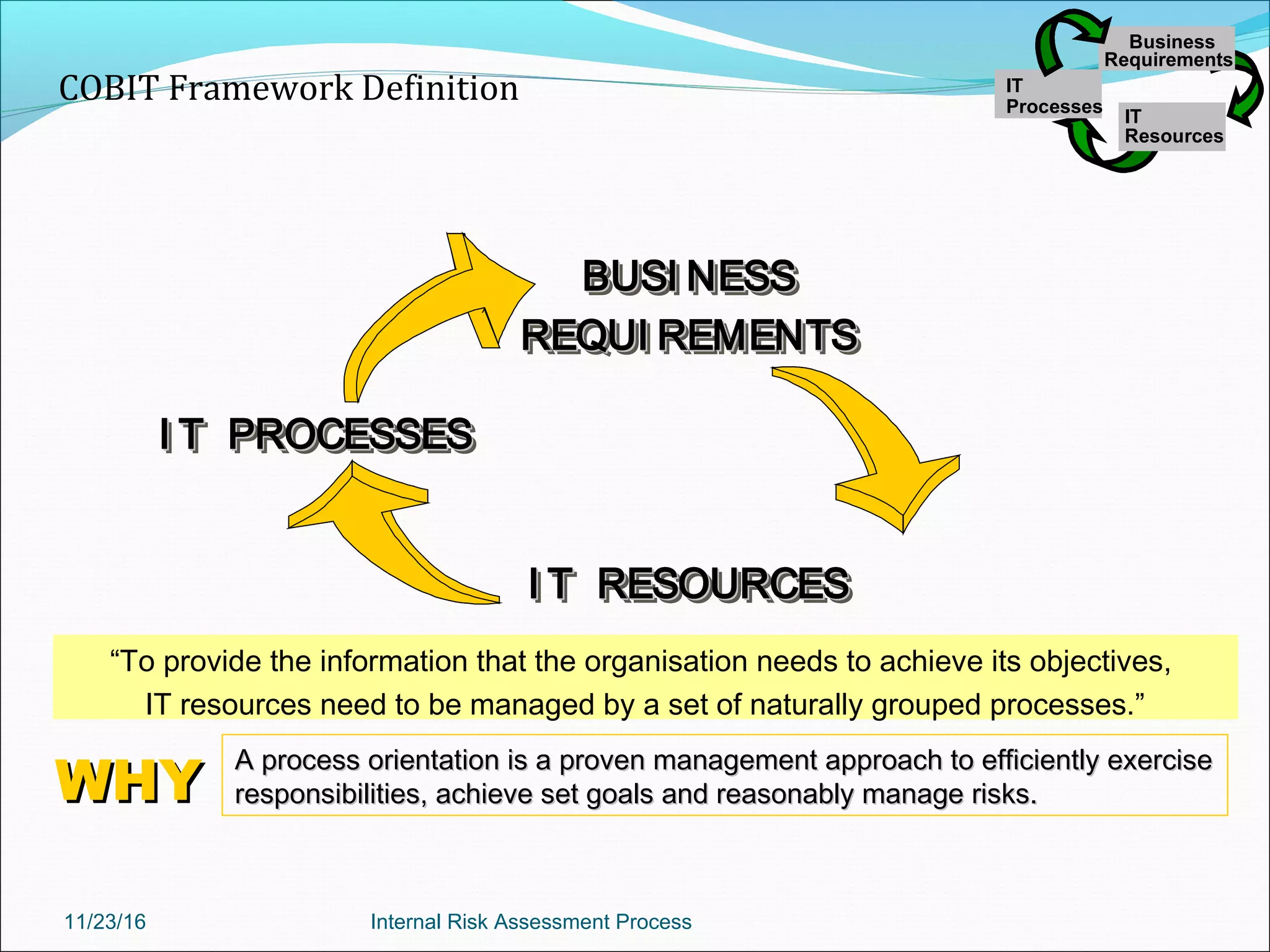
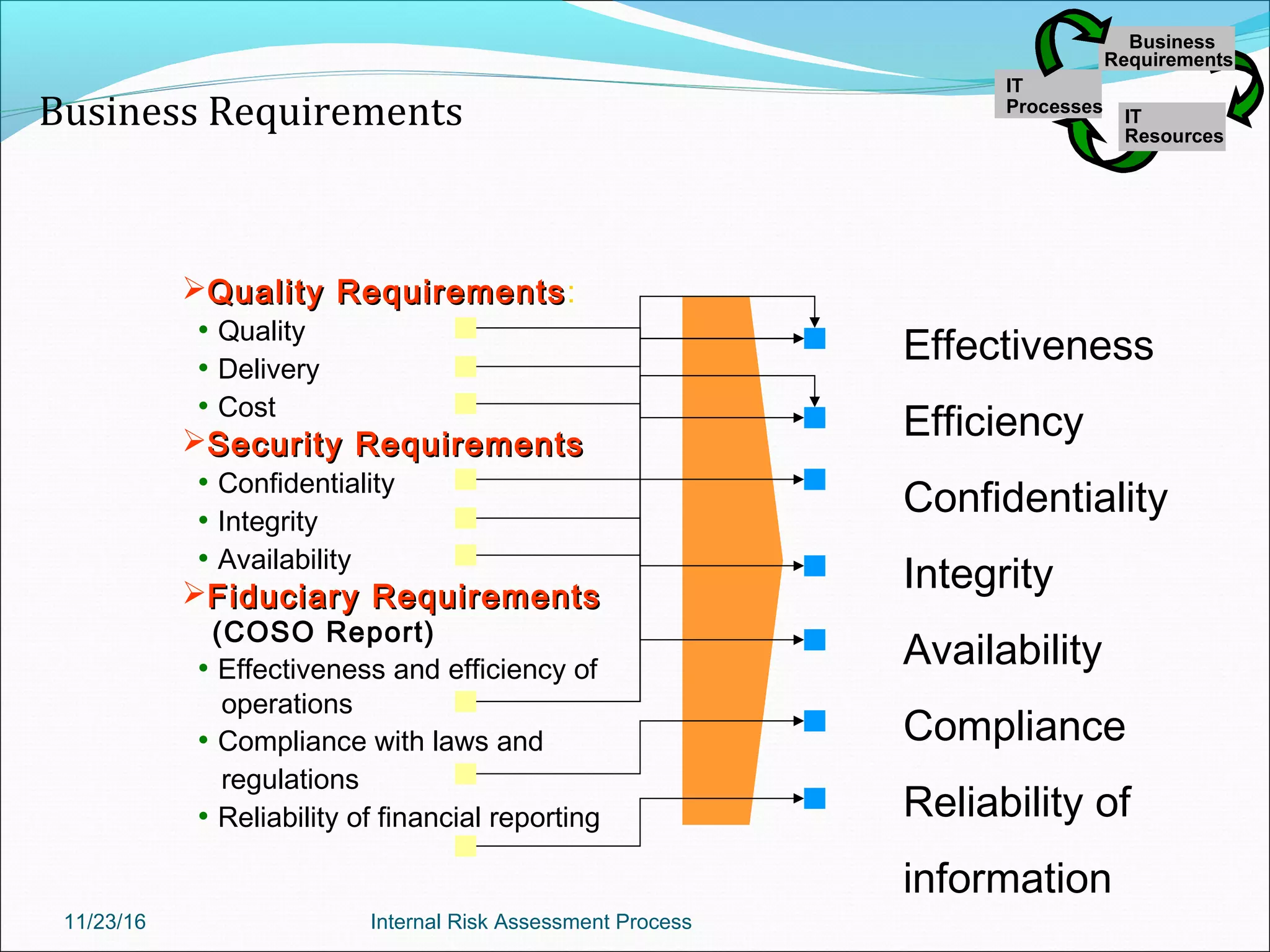
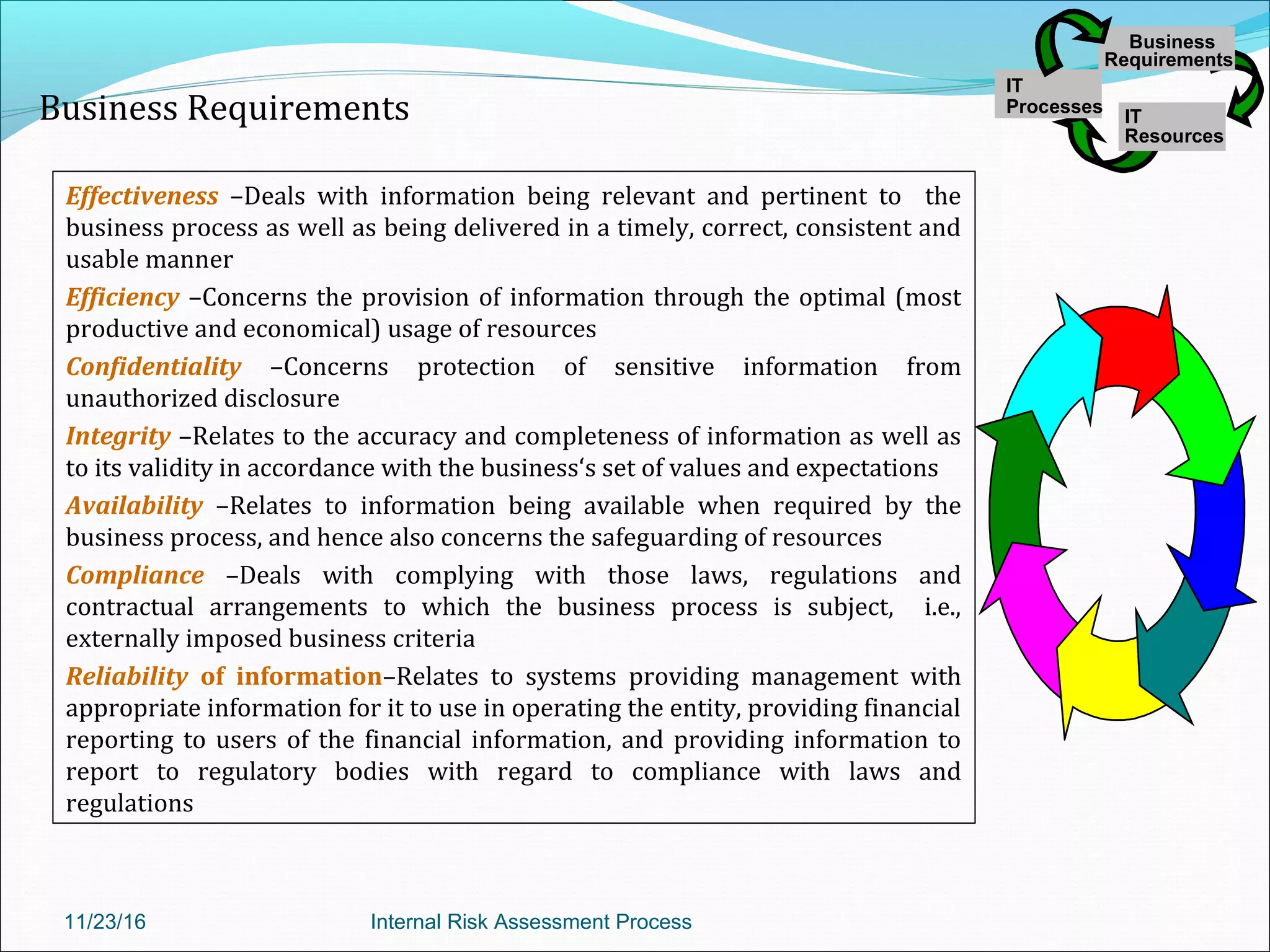
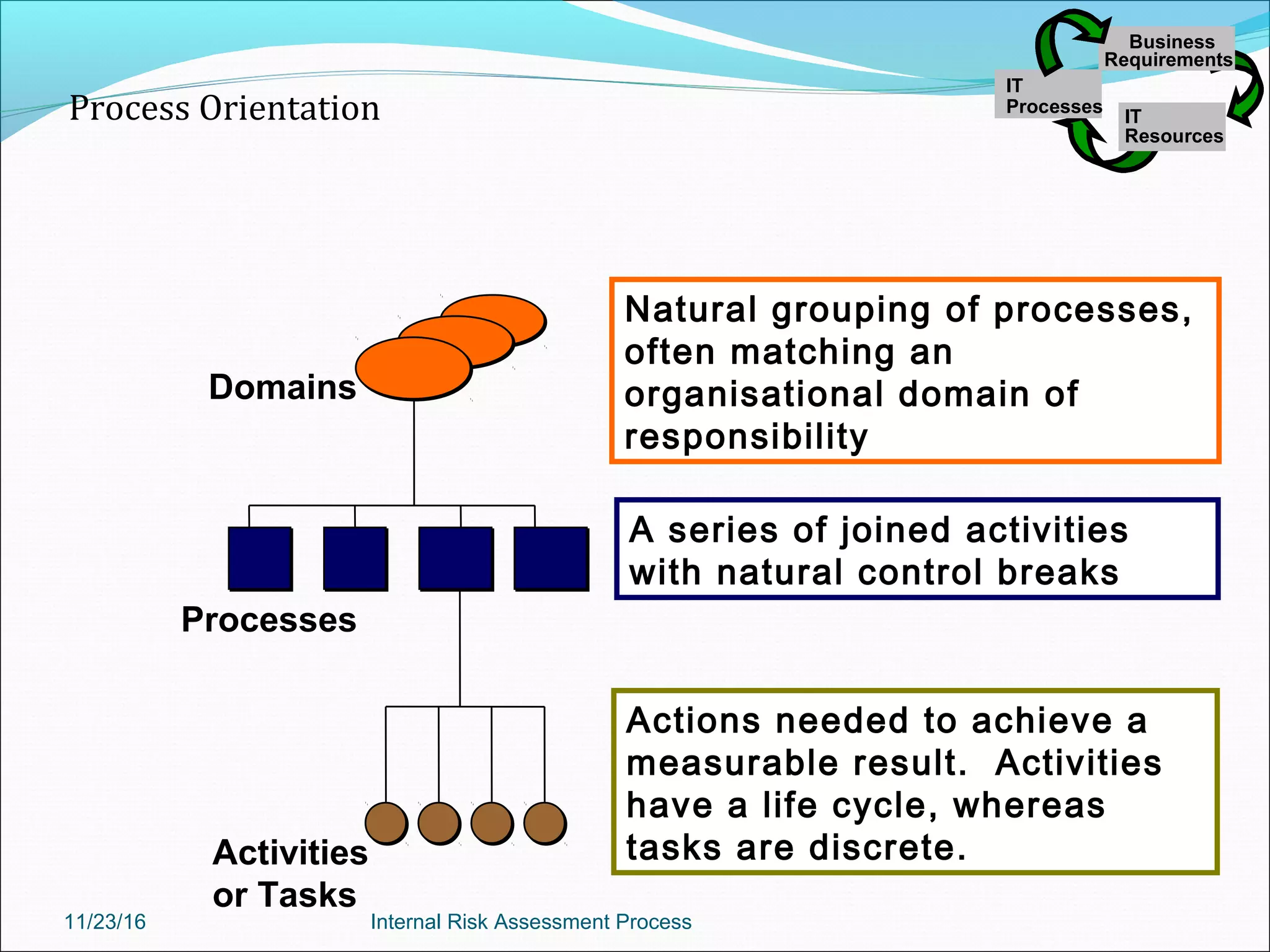
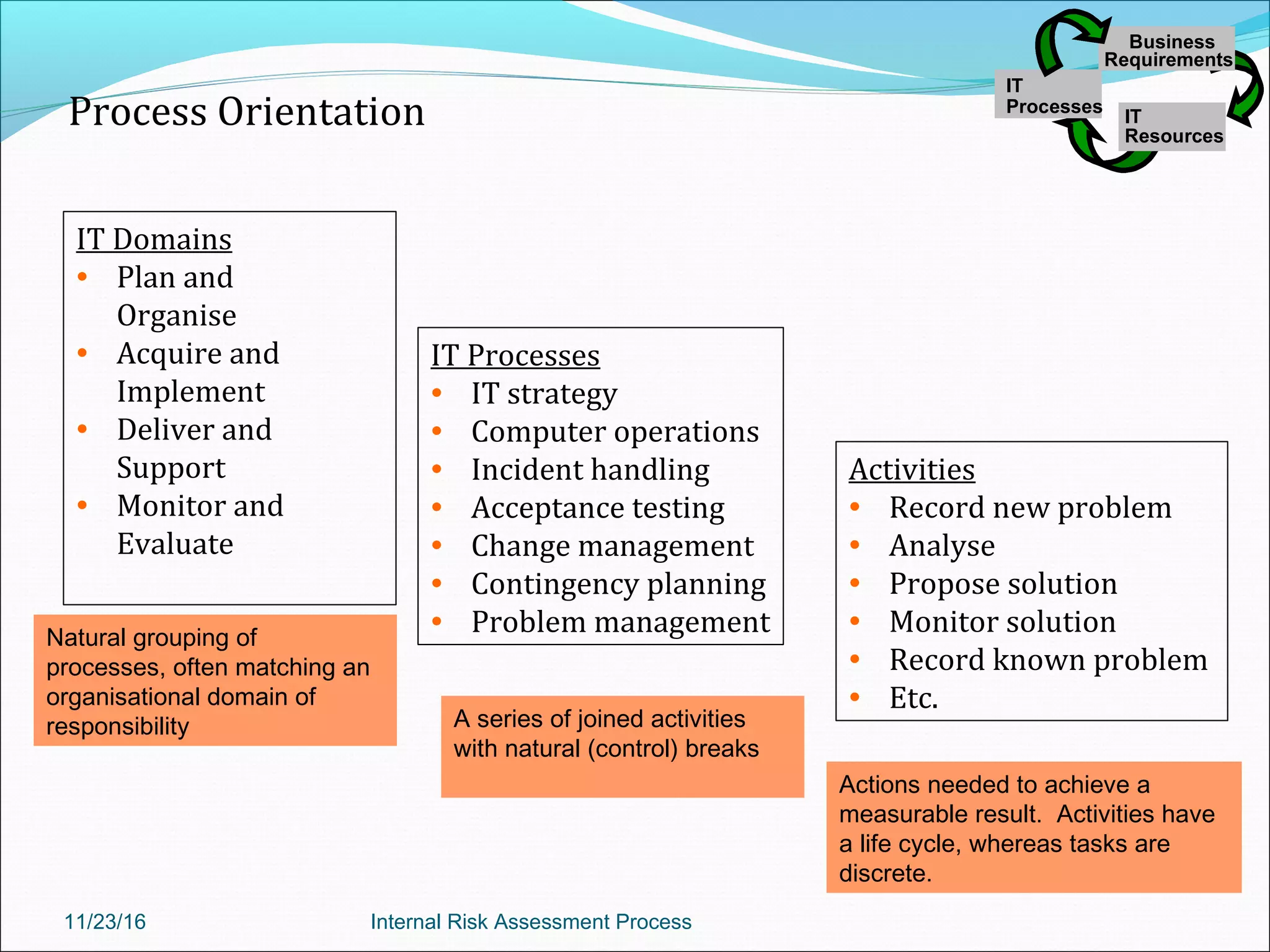
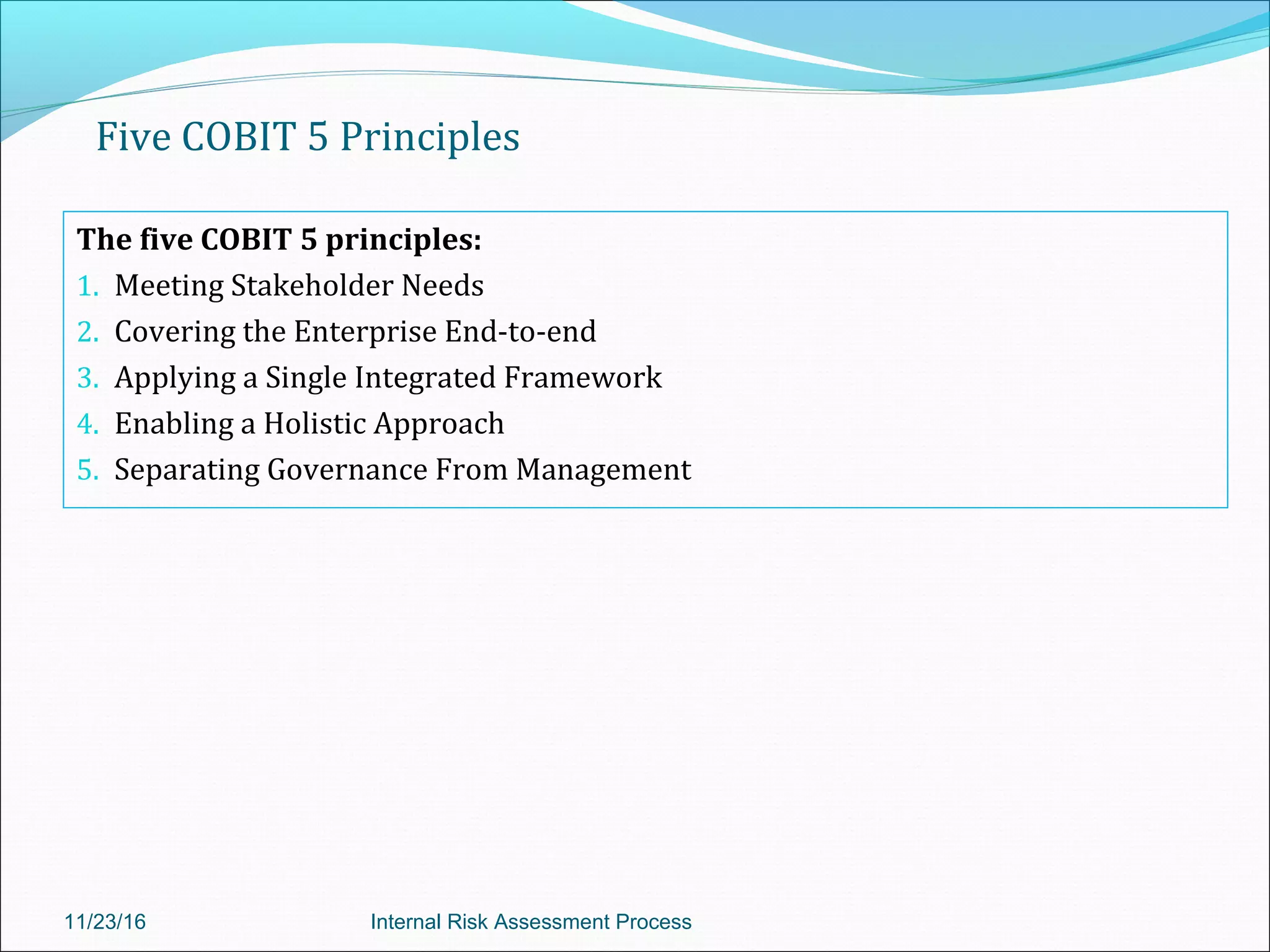
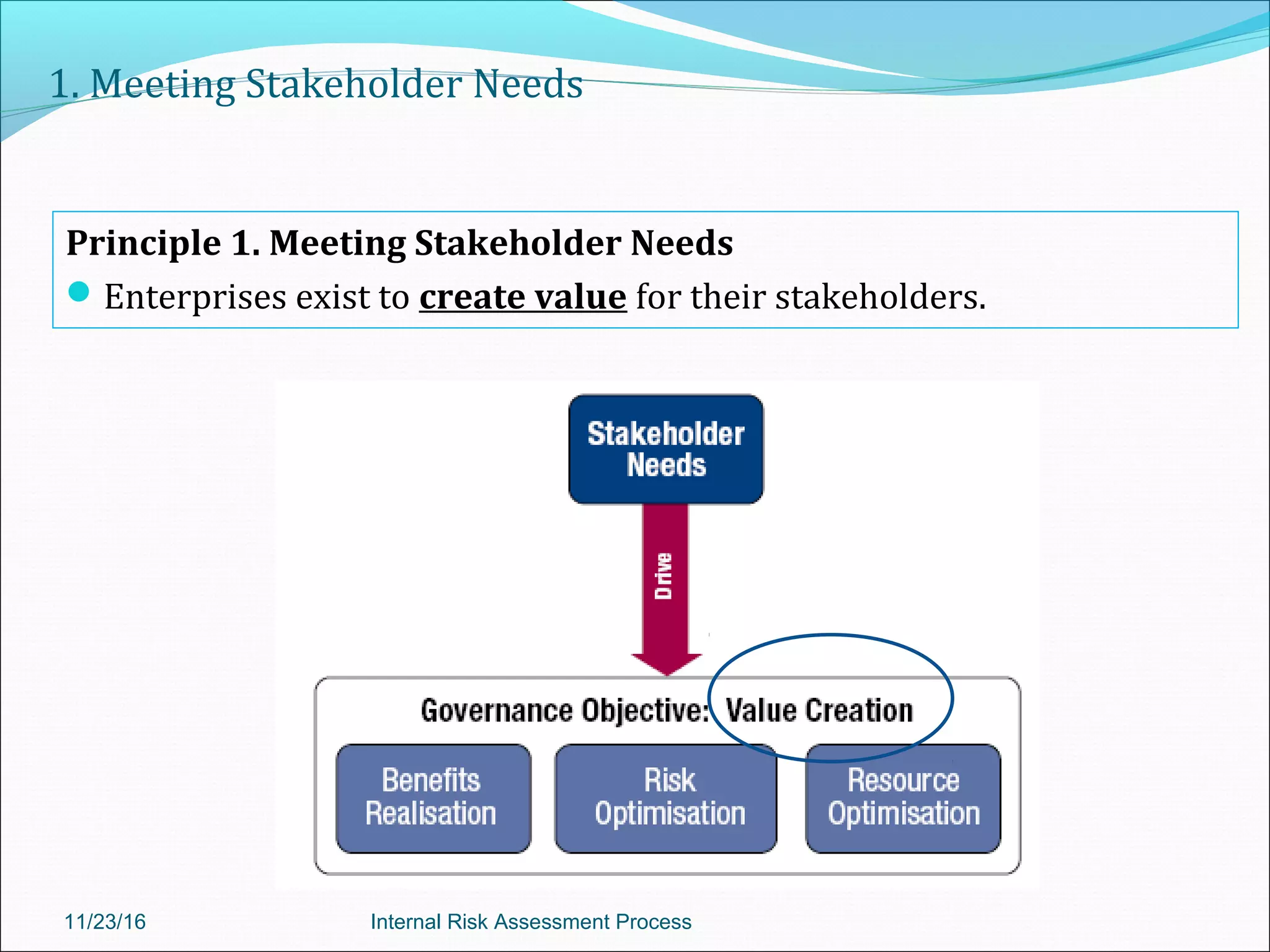
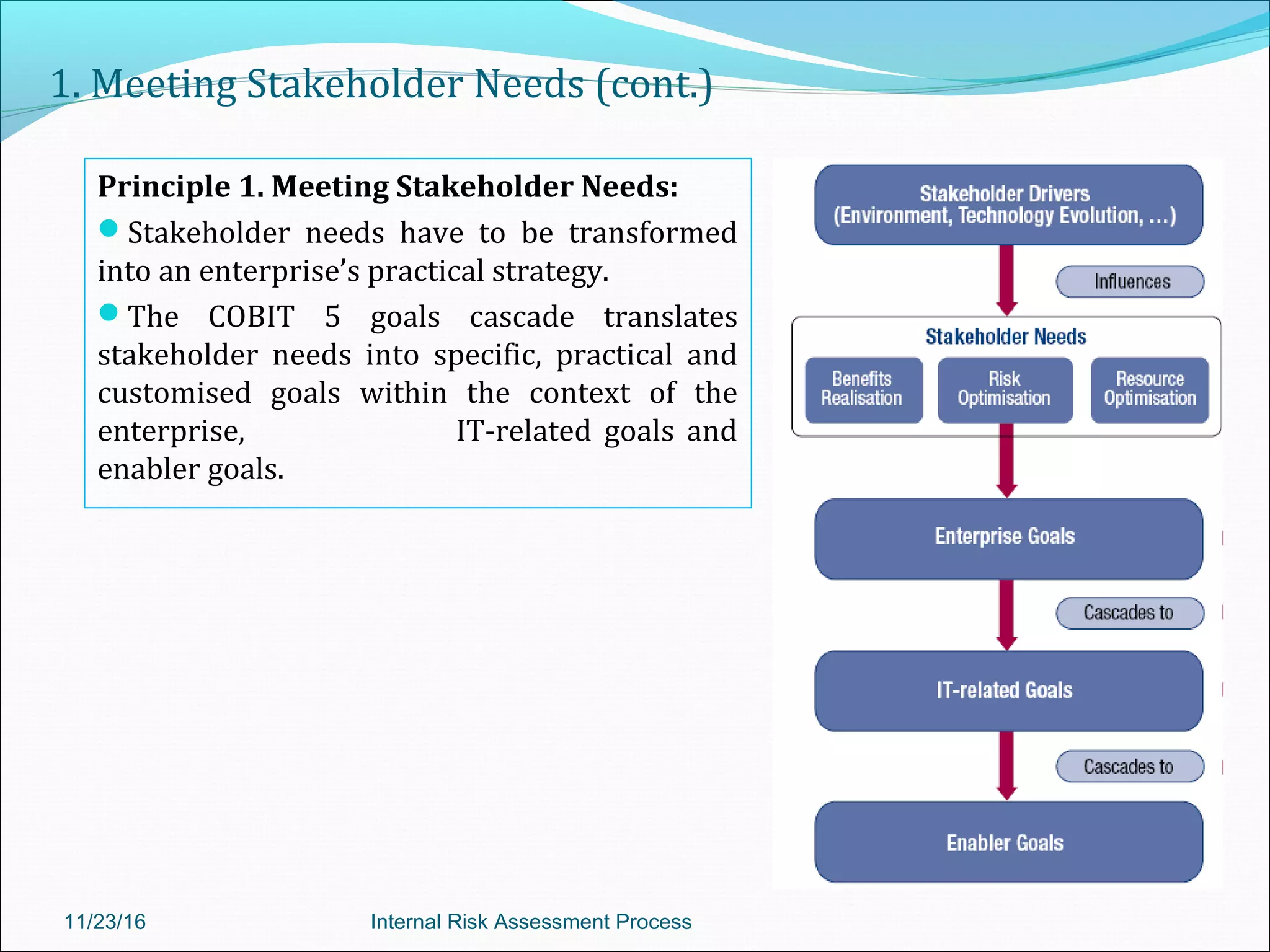
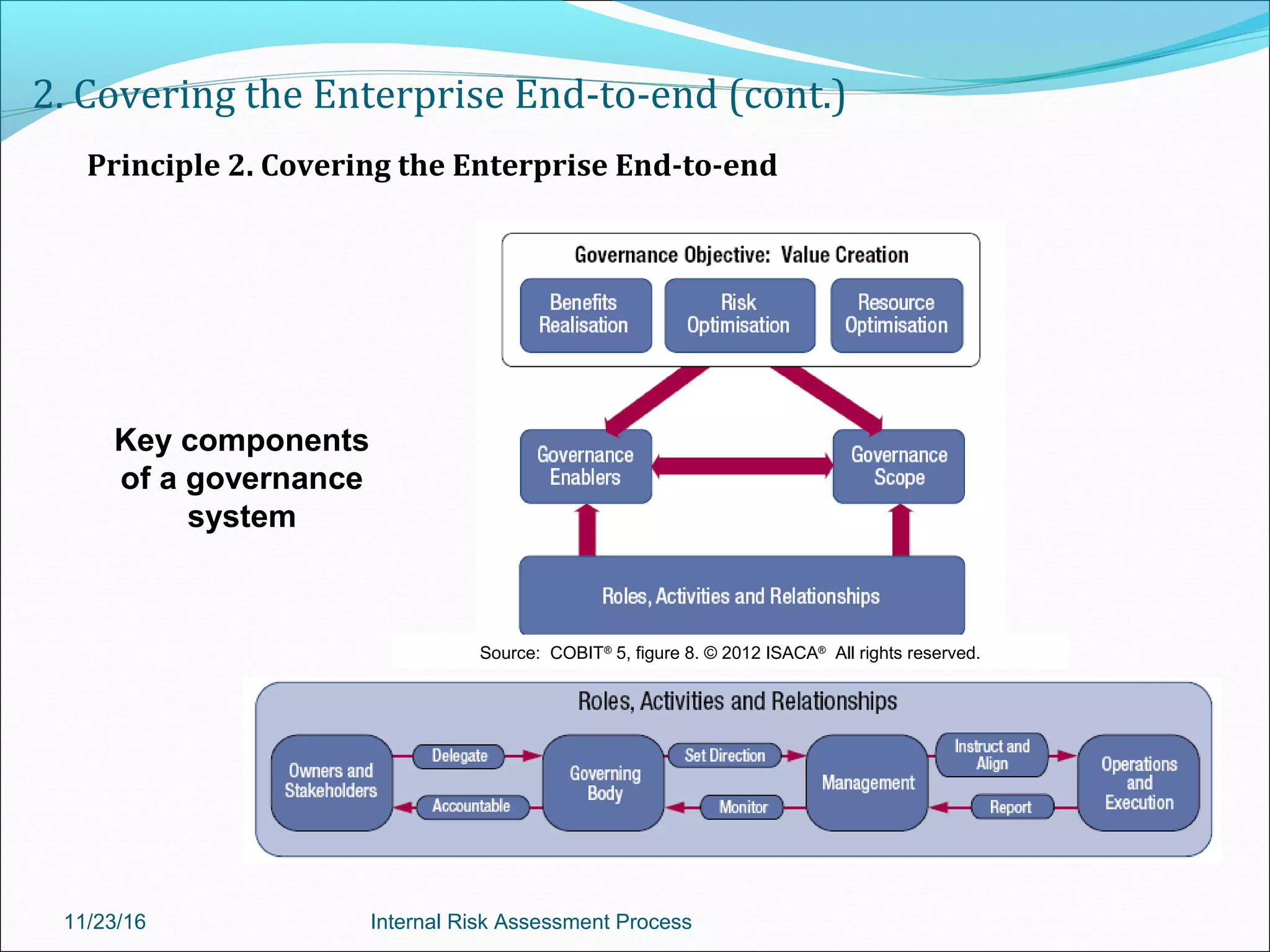
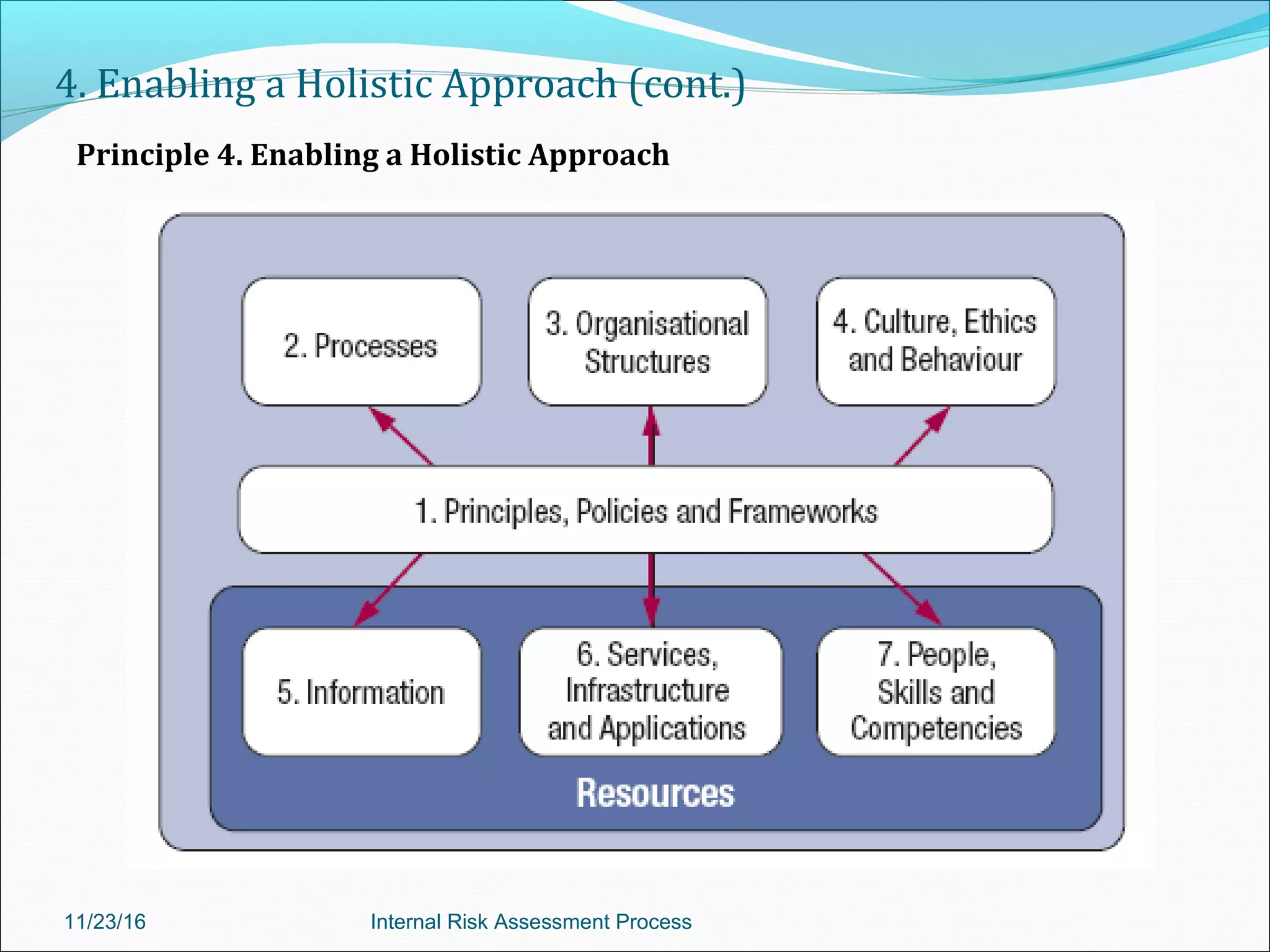
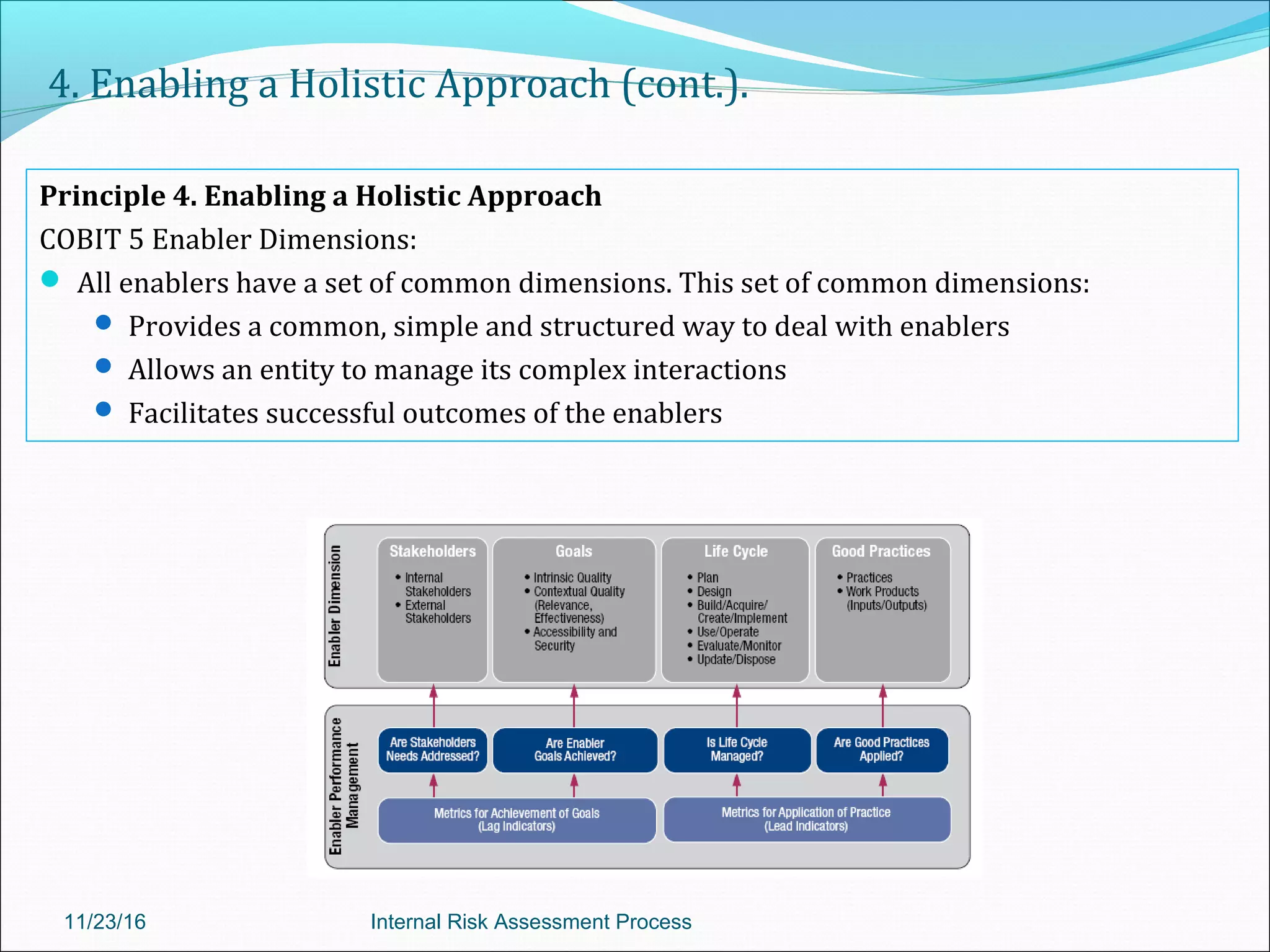
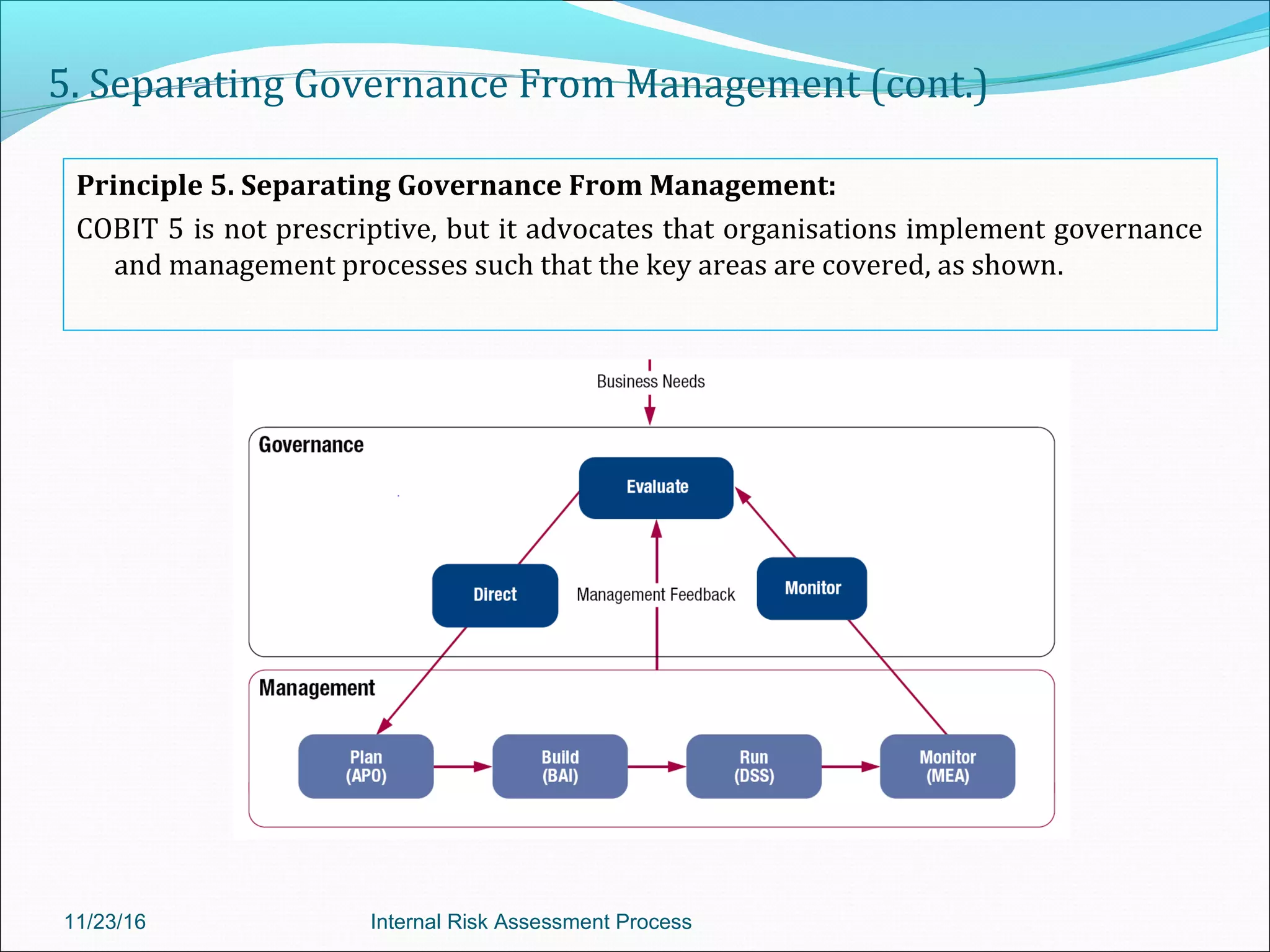
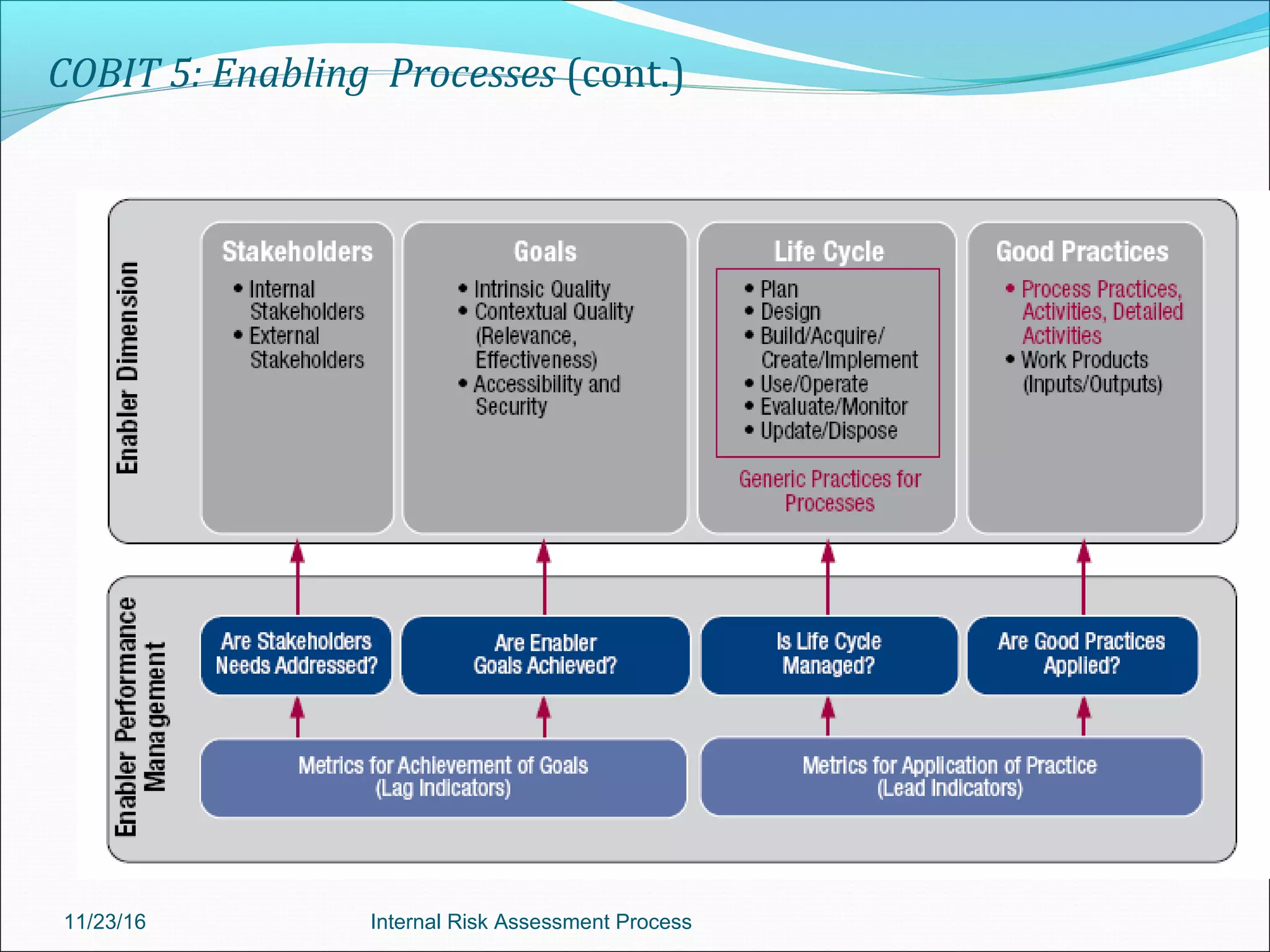
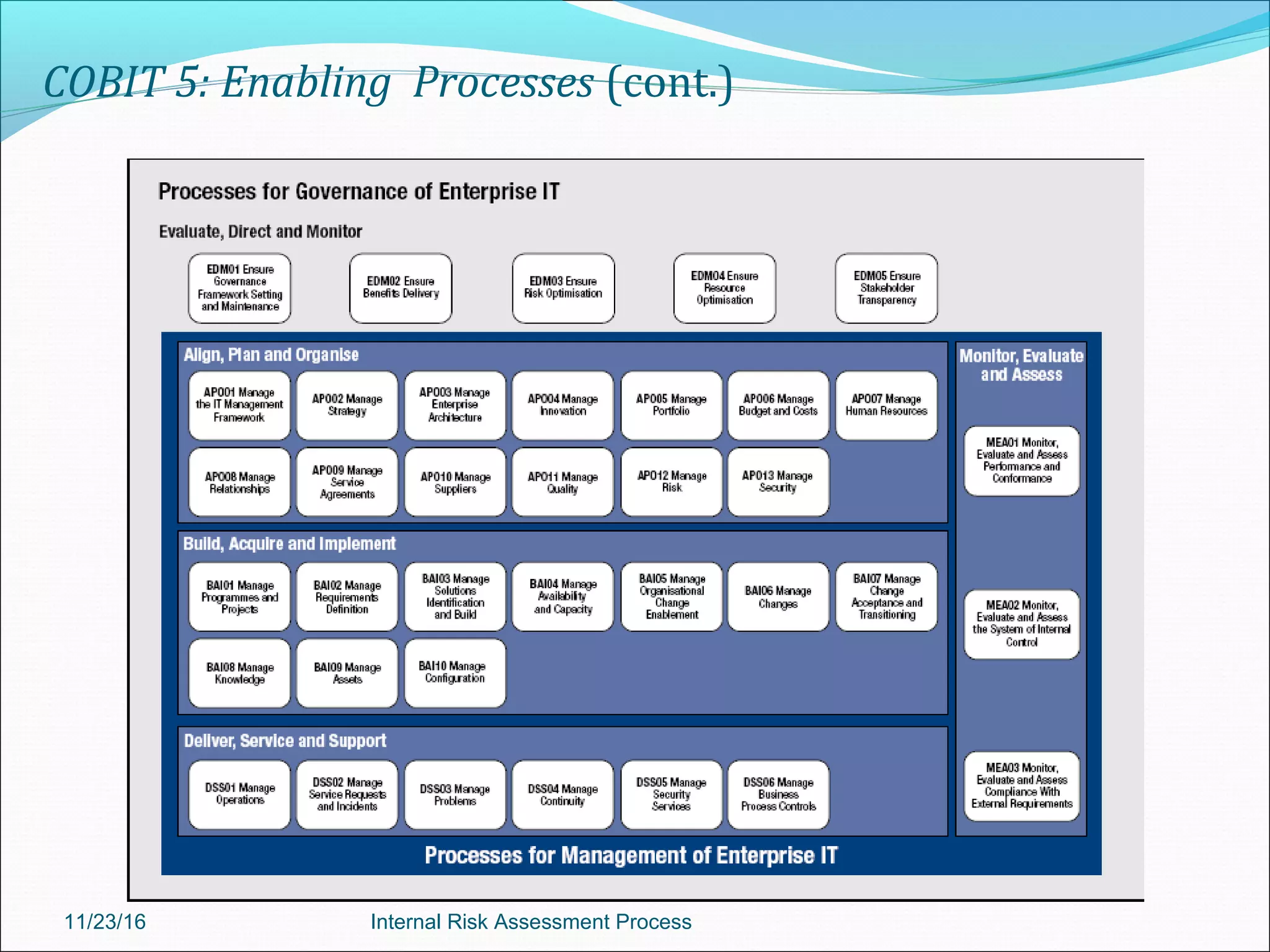
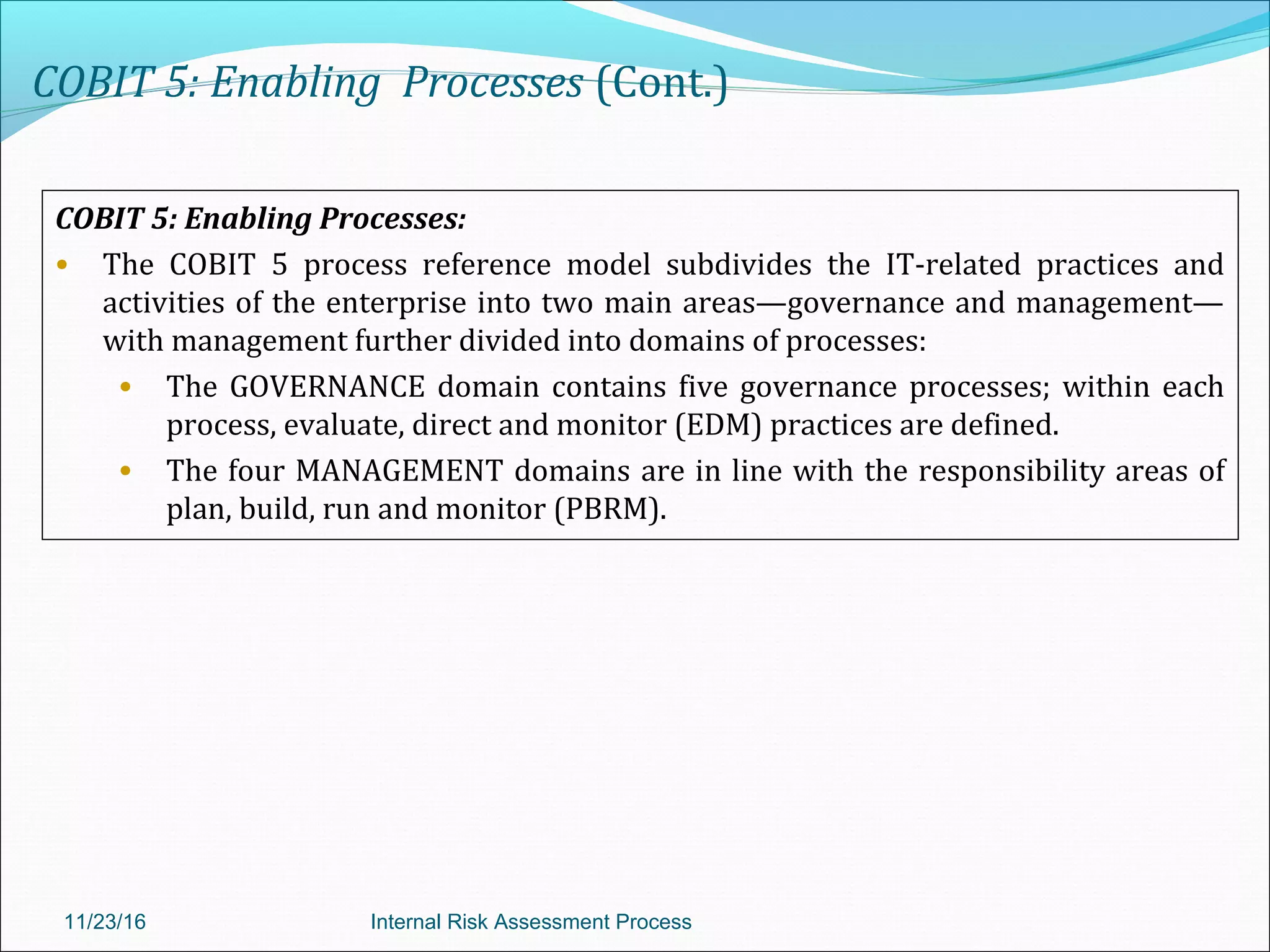
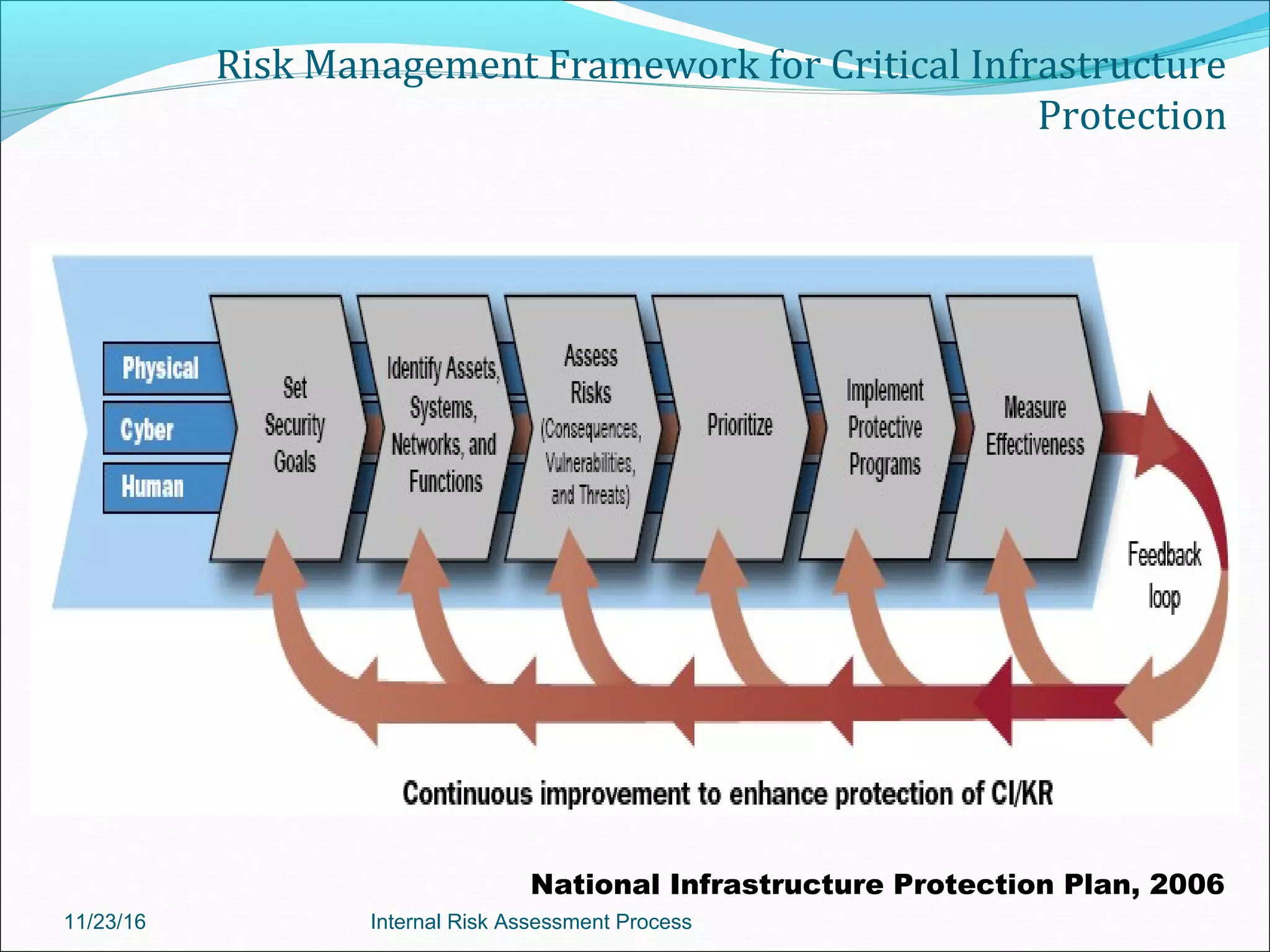
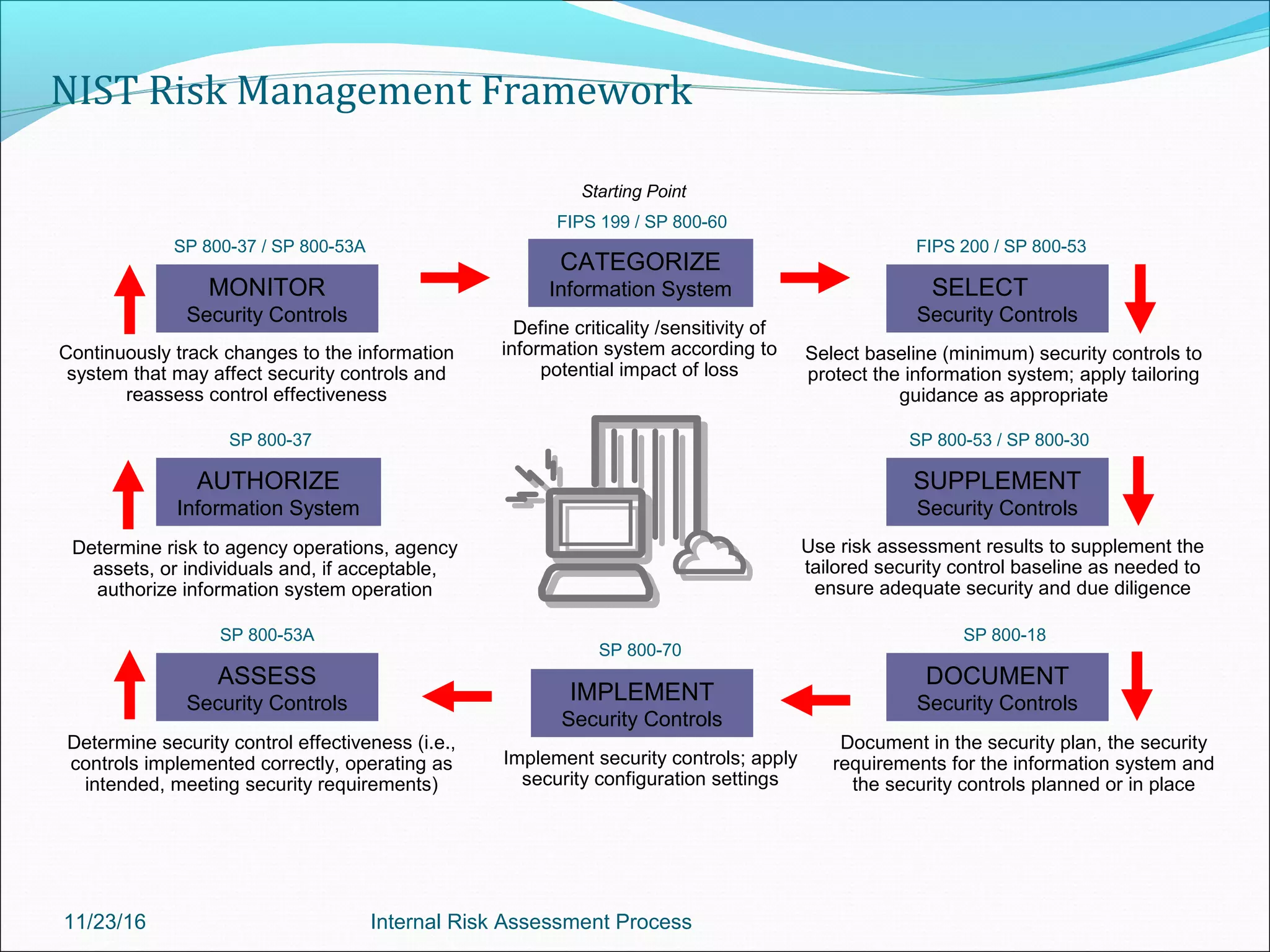
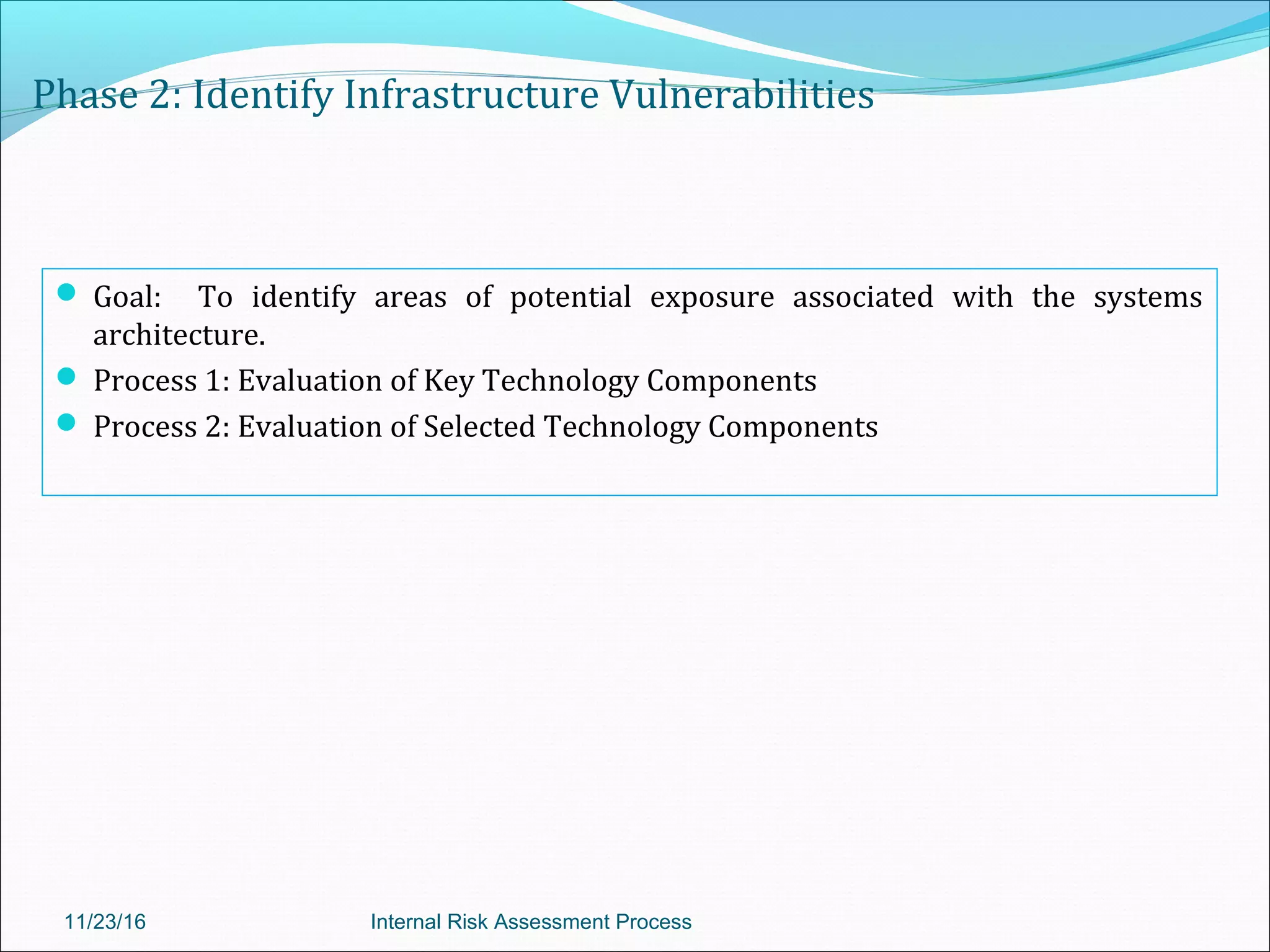
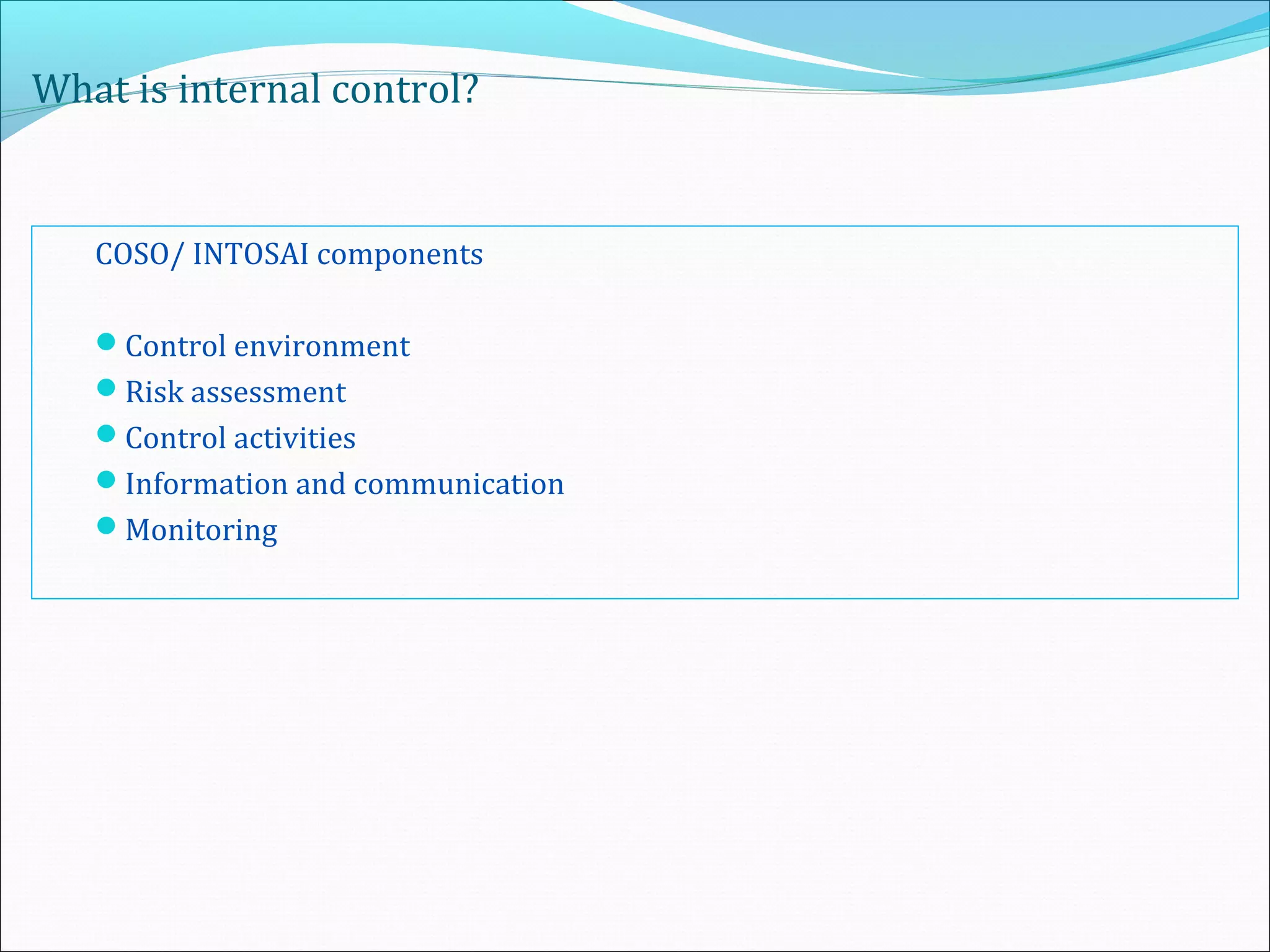
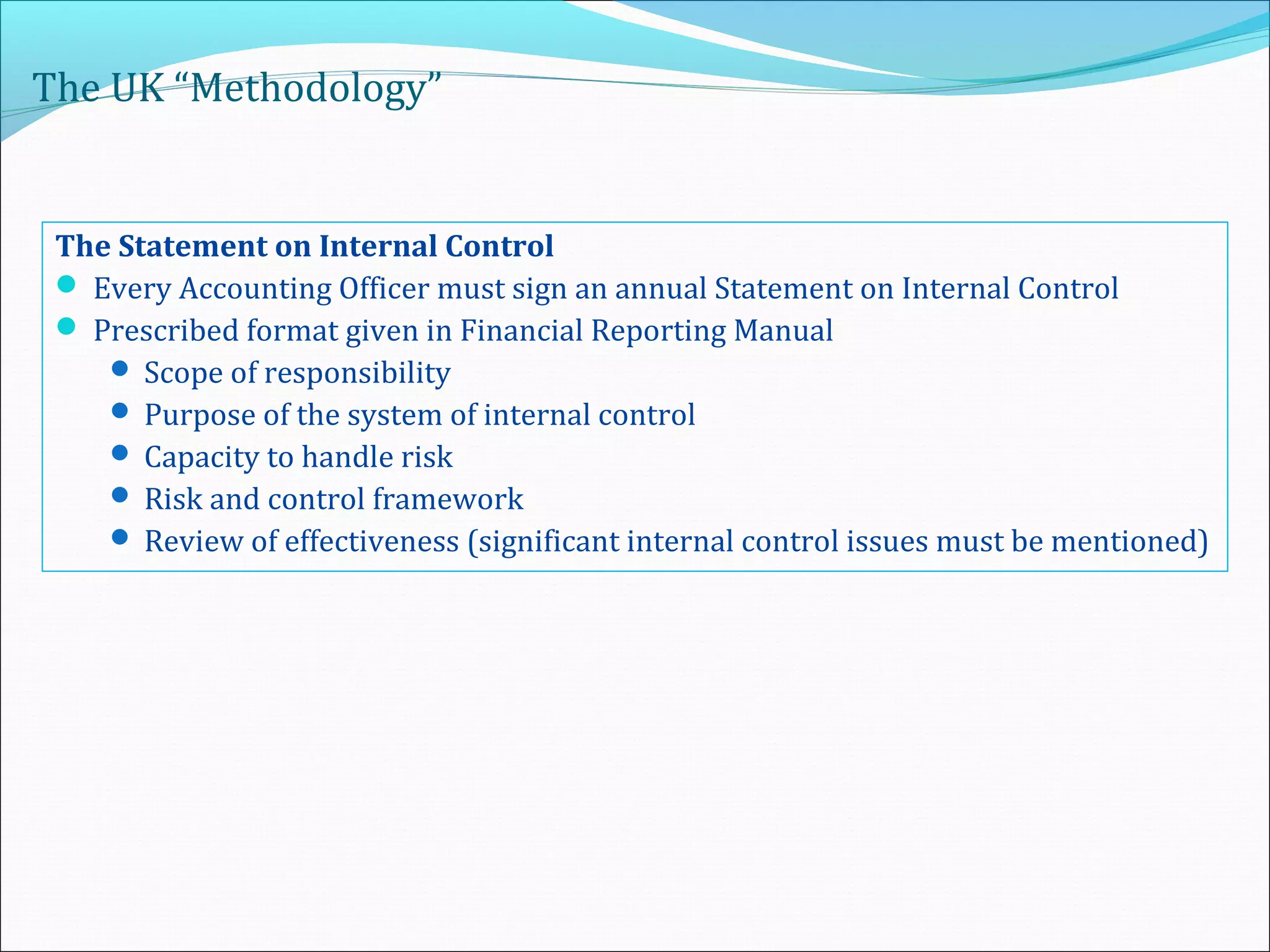
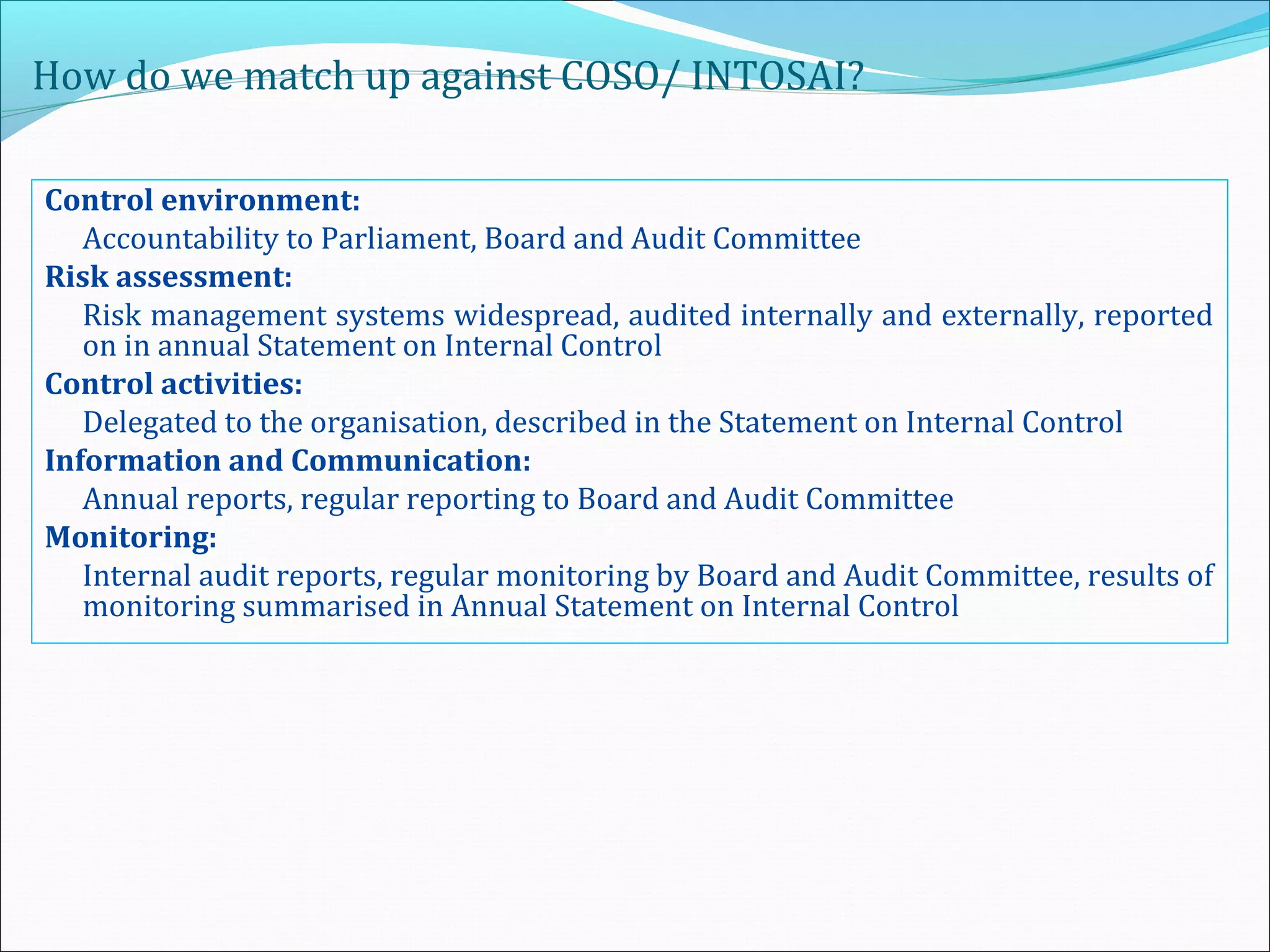
This document provides an overview of an internal risk assessment process presentation. It outlines the presentation agenda, which includes discussions of internal control frameworks like COSO and COBIT, risk assessment techniques, risk identification mapping, and the components of internal control. It also details the key aspects of each presentation section, such as defining internal control, its objectives, and management and auditor responsibilities regarding internal control assessment.