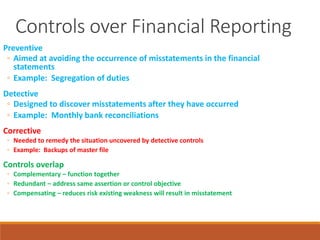
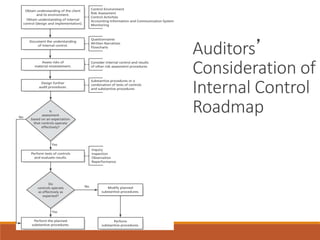
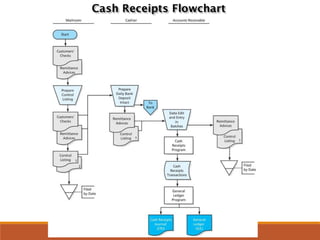
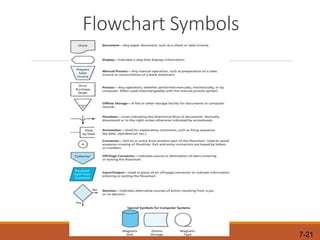
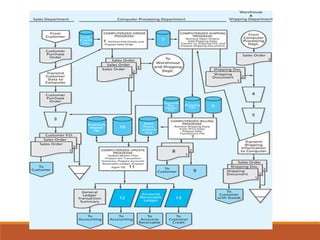
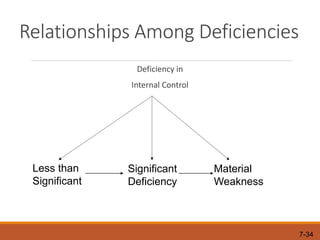
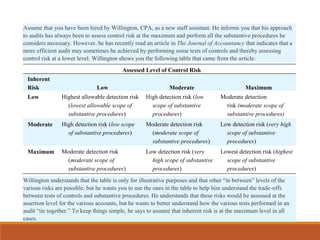
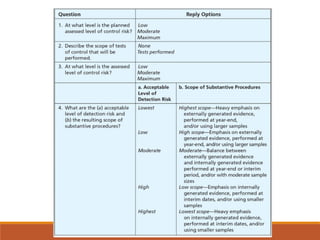
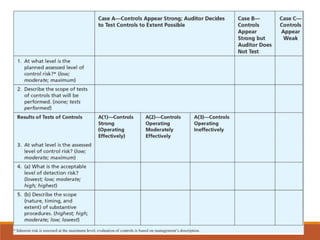
Here is how I would explain the trade-offs between tests of controls and substantive procedures based on the table:
If control risk is assessed at the maximum level, regardless of inherent risk, the auditor would need to perform substantive procedures with the lowest level of detection risk (highest scope). This means performing a high level of substantive procedures.
However, if the auditor performs tests of controls and determines controls are effective, they can assess control risk at a lower level. For example, if controls are effective in addressing some inherent risks, control risk could be assessed at a moderate level. In that case, for a moderate inherent risk, the auditor could perform substantive procedures with a moderate detection risk (moderate scope). This allows the auditor to reduce the