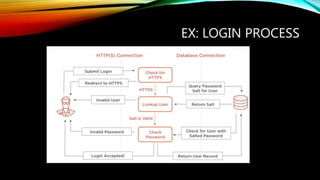
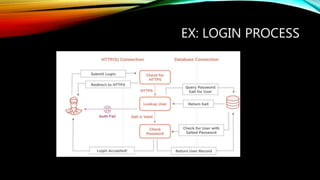
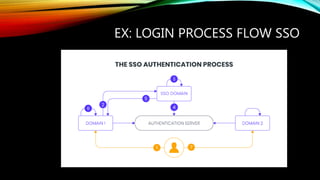
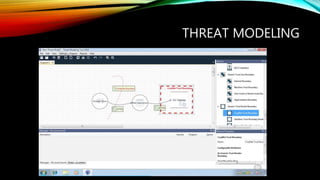
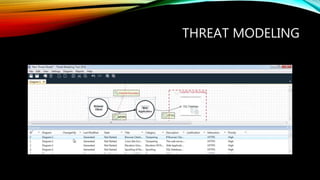
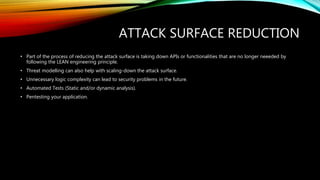
This document discusses security best practices for software developers. It covers topics like the secure software development lifecycle (SDLC), threat modeling, static code analysis, and resources for developers. The SDLC framework defines the process for building applications from start to finish. Threat modeling involves analyzing potential threats and vulnerabilities. Static code analysis tools can find security issues. Resources recommended include OWASP documentation and Microsoft's security engineering practices. The goal is to integrate security practices into development like training, requirements, testing, and incident response.