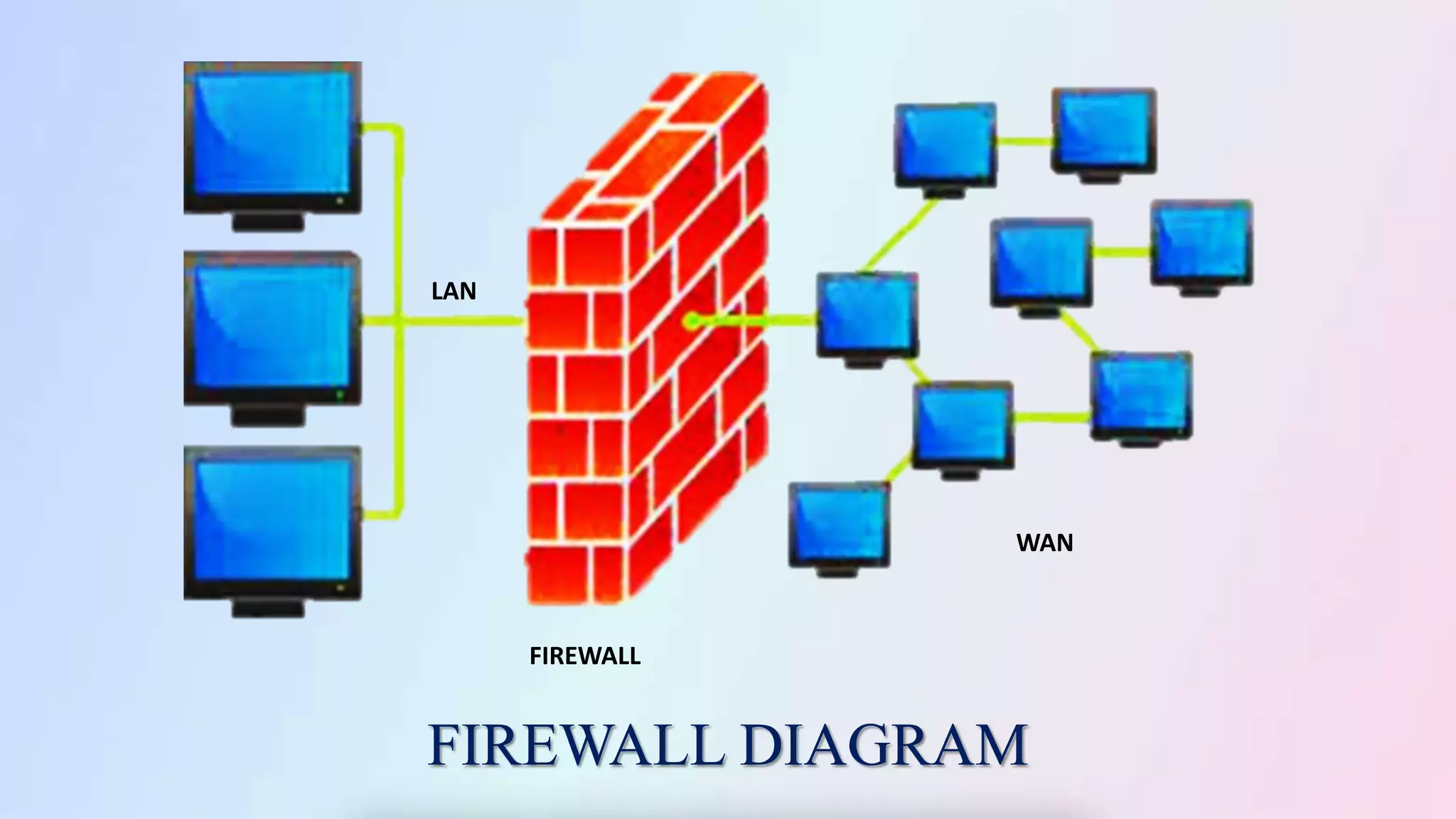
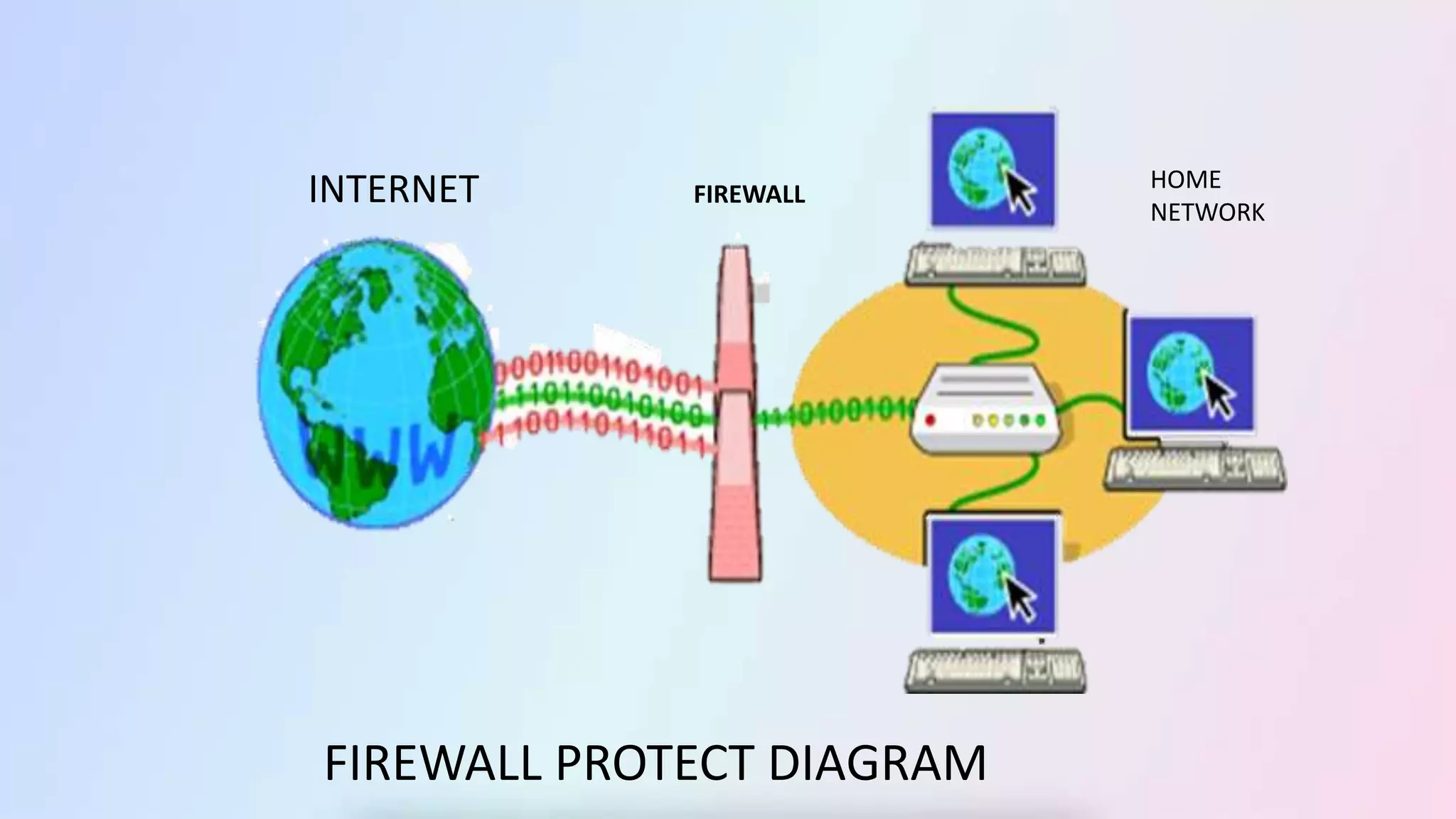
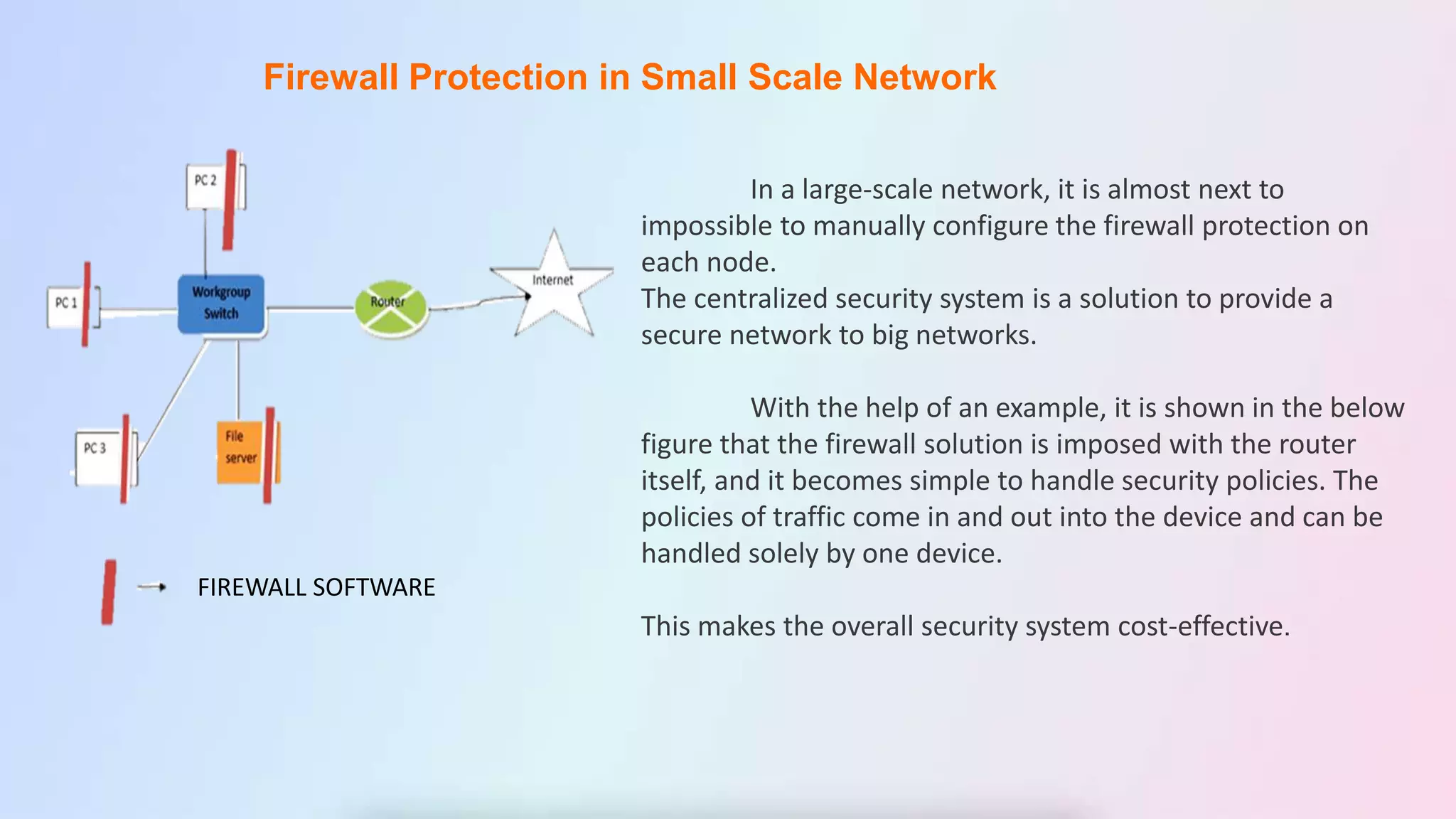
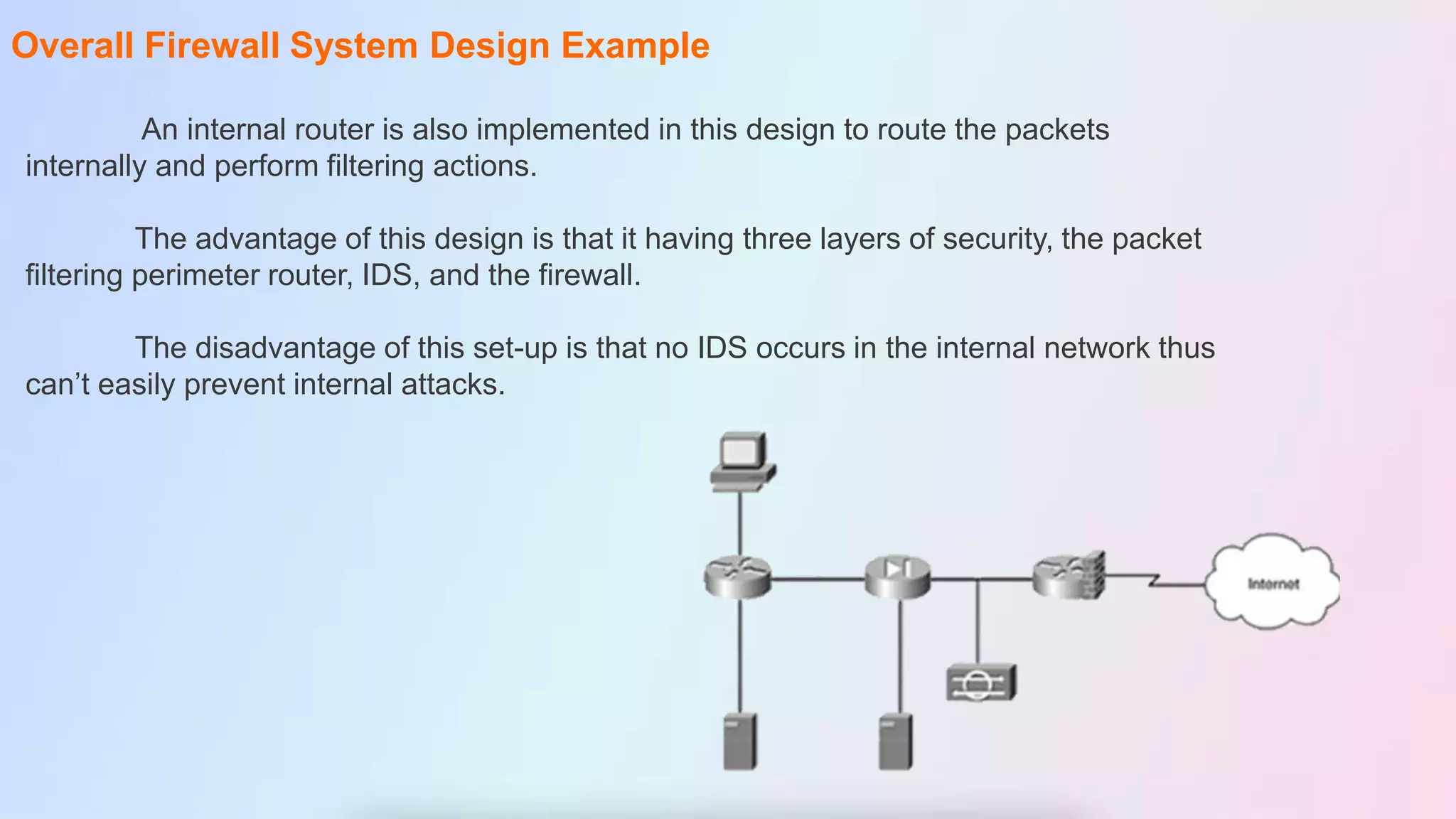
The document discusses firewalls, including their definition as devices that monitor incoming and outgoing network traffic based on security rules. It covers firewall protection in small and large networks, overall firewall system design, important design facts, categories of firewalls like packet filtering and proxy, types of firewall software, and benefits and disadvantages of firewalls. The conclusion restates that firewalls introduce network security by filtering traffic according to rules to protect against external and internal threats.