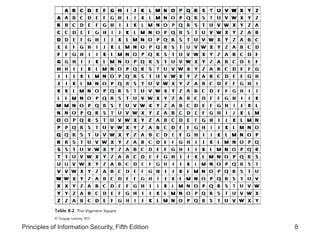
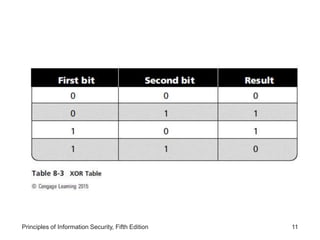
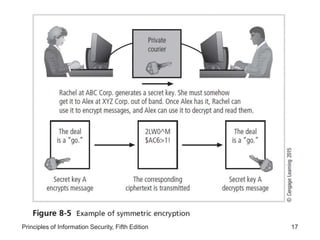
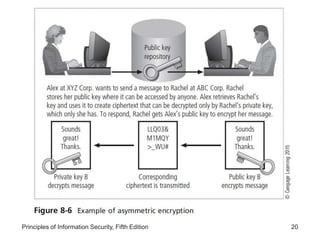
This document provides an overview of cryptography foundations and principles. It chronicles the history of cryptology and describes symmetric and asymmetric encryption algorithms. Symmetric algorithms like DES, 3DES, and AES use a shared secret key for encryption and decryption, while asymmetric algorithms like RSA use public-private key pairs. The document also covers cryptographic concepts like substitution ciphers, transposition ciphers, hash functions, and the importance of key size for encryption strength.