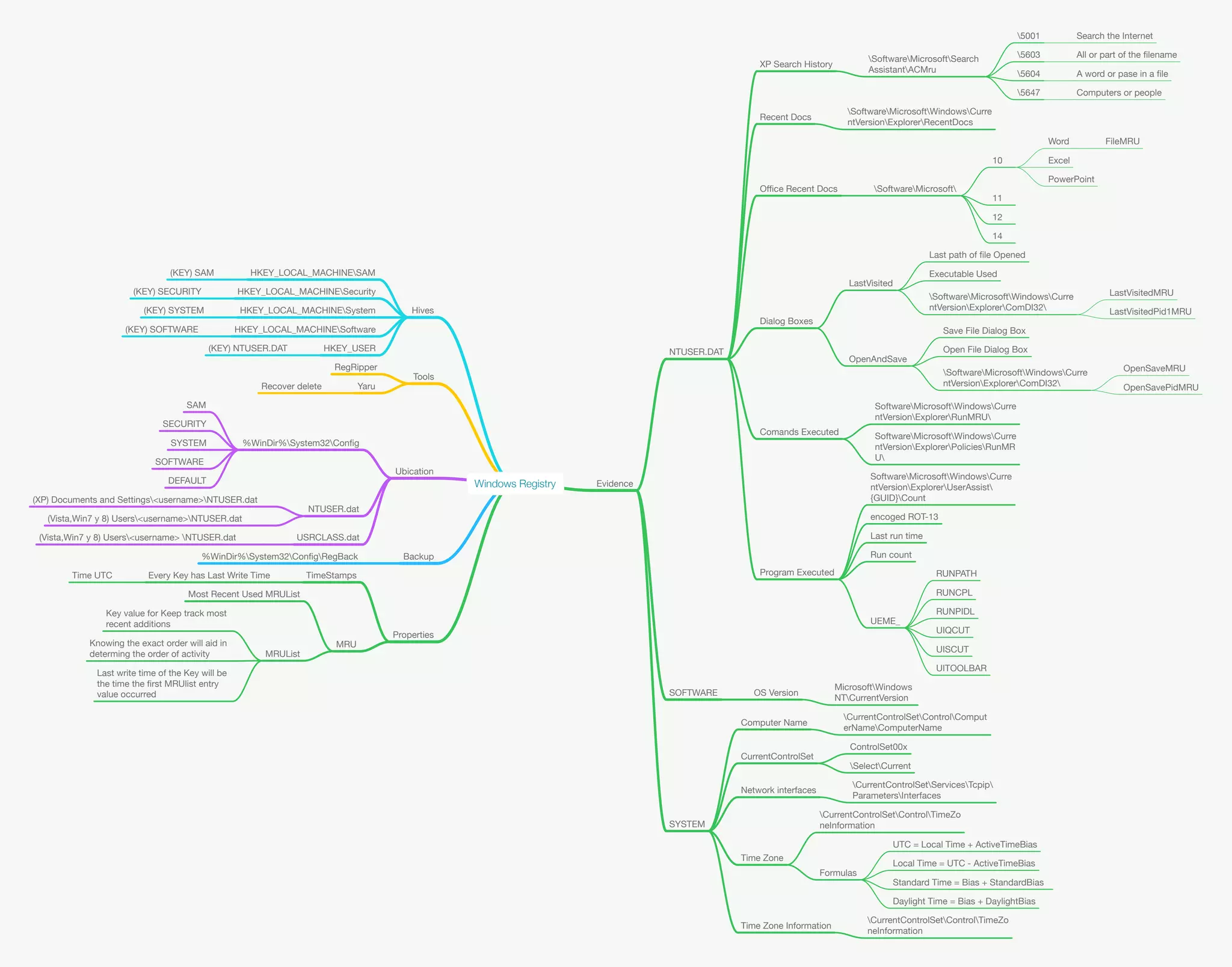
This document summarizes information about the Windows Registry including its structure, tools used to access it, locations of hive files, and types of evidence that can be extracted including search history, recent documents, dialog boxes used, commands executed, and software/OS versions. It explains registry hives like HKEY_LOCAL_MACHINE, keys with MRU lists that track recently used items, and how timestamps and MRU lists can help determine the order and time of user activity on a system.