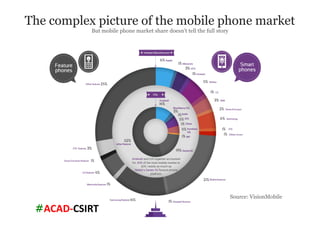
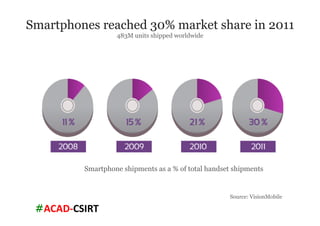
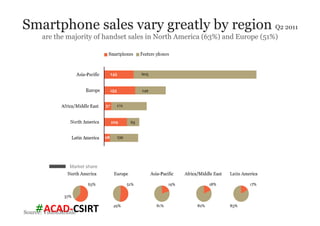
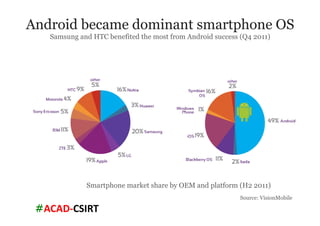
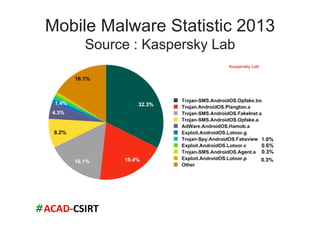
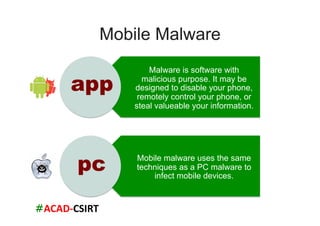
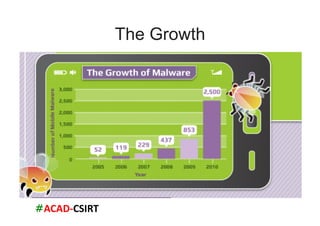
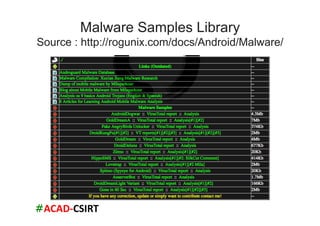
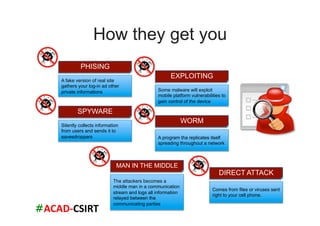
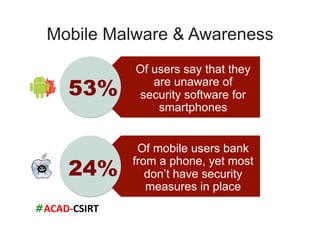
The document discusses mobile trends, the rise of smartphones, and mobile malware threats. It notes that smartphones reached 30% of the global mobile market in 2011. It also discusses the rise of Android as the dominant smartphone OS and how this benefited companies like Samsung and HTC. The document outlines several types of mobile malware and statistics on mobile malware infections. It details how mobile malware can steal private information or control devices. Finally, it provides tips on securing mobile devices and awareness of mobile security issues.









![#ACAD-‐CSIRT
References
• A window into Mobile device security
– http://www.symantec.com/content/en/us/about/media/pdfs/
symc_mobile_device_security_june2011.pdf
• http://www.continuitycentral.com/feature0919.html
• http://www.usatoday.com/tech/news/story/2012-03-22/
lost-phones/53707448/1]
• US-CERT Resource: Paul Ruggiero and Jon Foote,
“Cyber Threats to Mobile Phones”, http://www.us-
cert.gov/reading_room/
cyber_threats_to_mobile_phones.pdf)
• Top 10 android Security Riskshttp://
www.esecurityplanet.com/views/article.php/3928646/
Top-10-Android-Security-Risks.htm](https://image.slidesharecdn.com/seminarmalware2013ignmantra-130618124539-phpapp01/85/I-G-N-Mantra-Mobile-Security-Mobile-Malware-and-Countermeasure-20-320.jpg)
