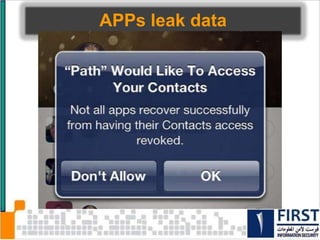
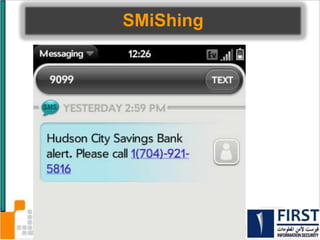
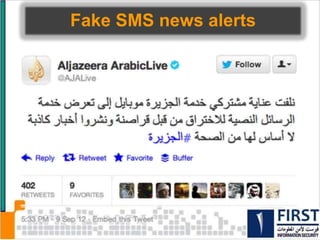
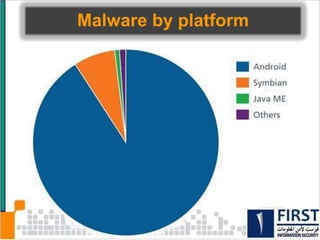
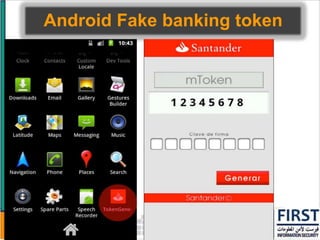
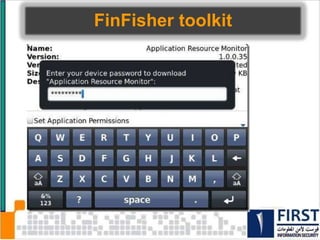
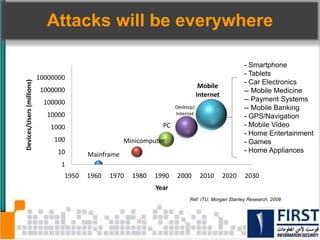
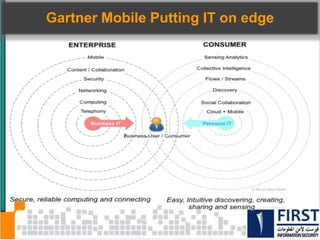
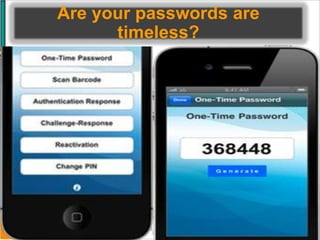
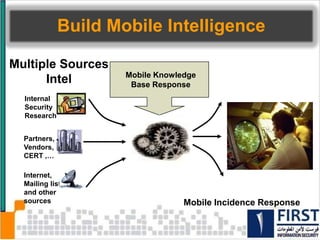
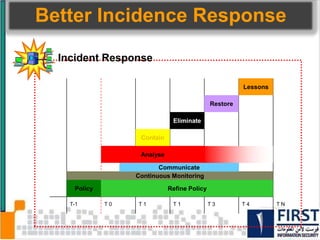
This document discusses the security risks posed by increased mobility and use of mobile devices. It notes that mobile malware is up 1200% and that many popular apps leak user data or have other security vulnerabilities. Common attacks on mobile devices include SMS phishing, location tracking without permission, and fake banking apps. The document advocates for building intelligence on mobile threats and improving incident response. It also promotes securing devices, applications, and communications to protect against the risks that arise from increased mobility.