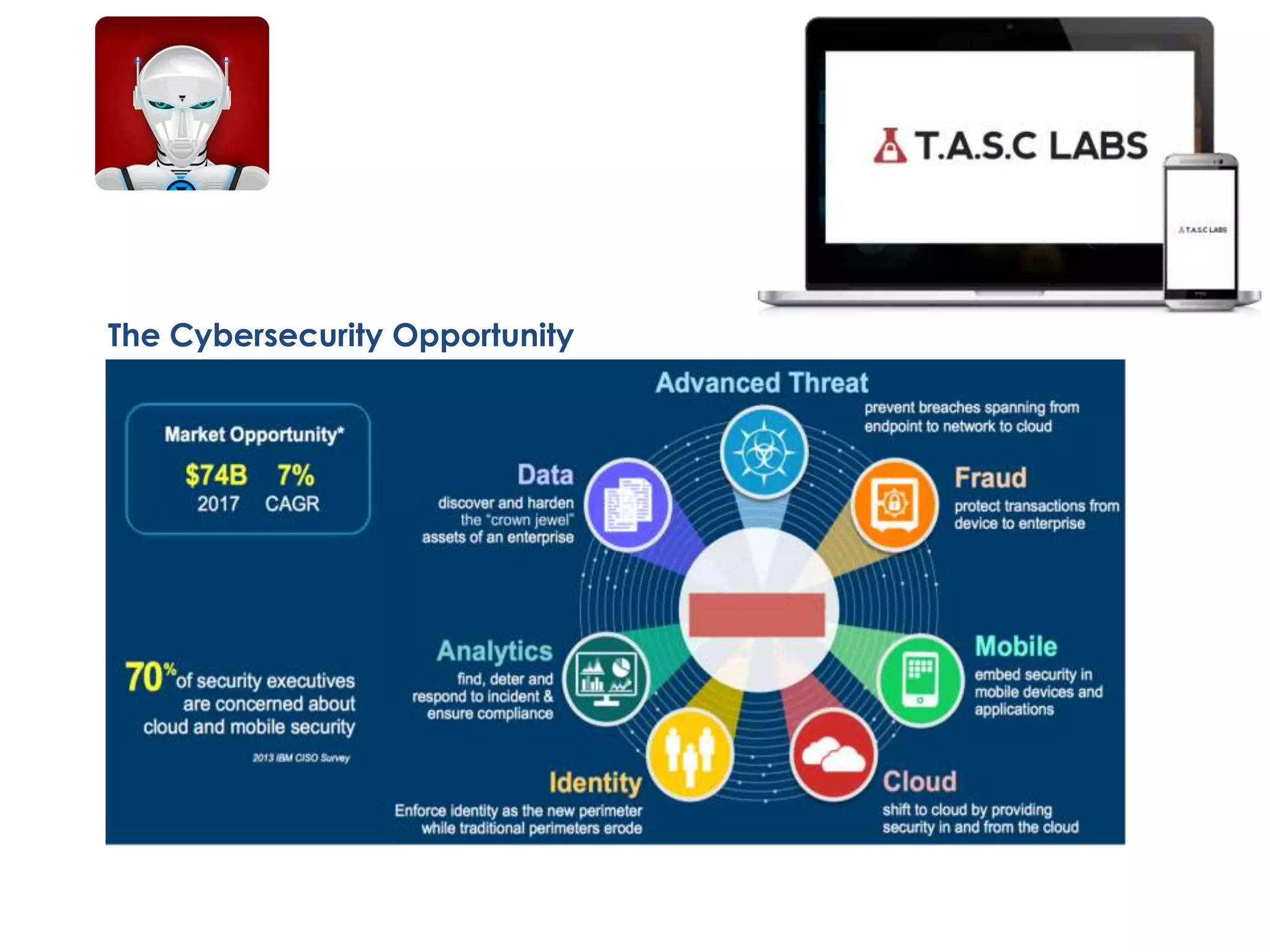
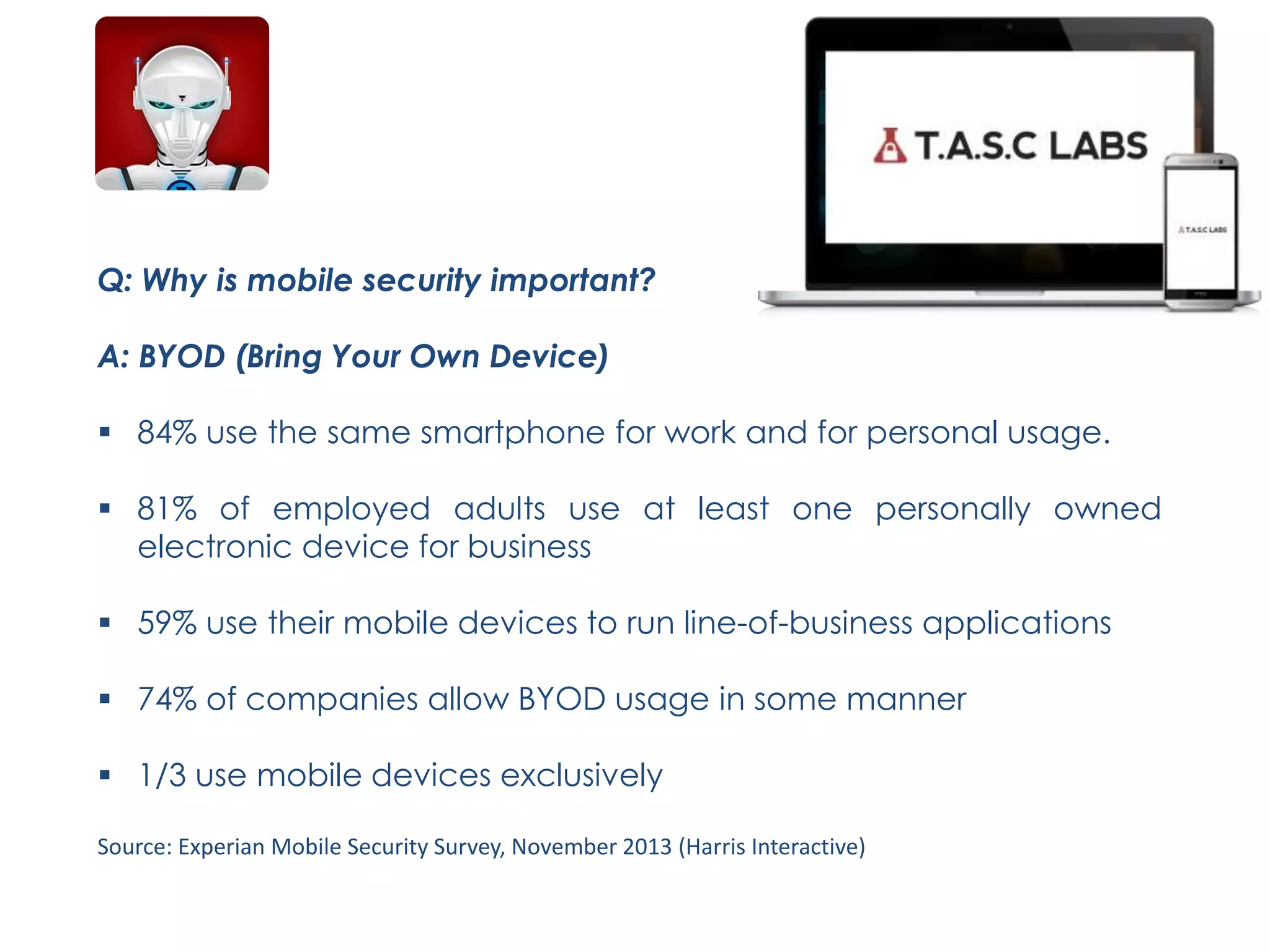
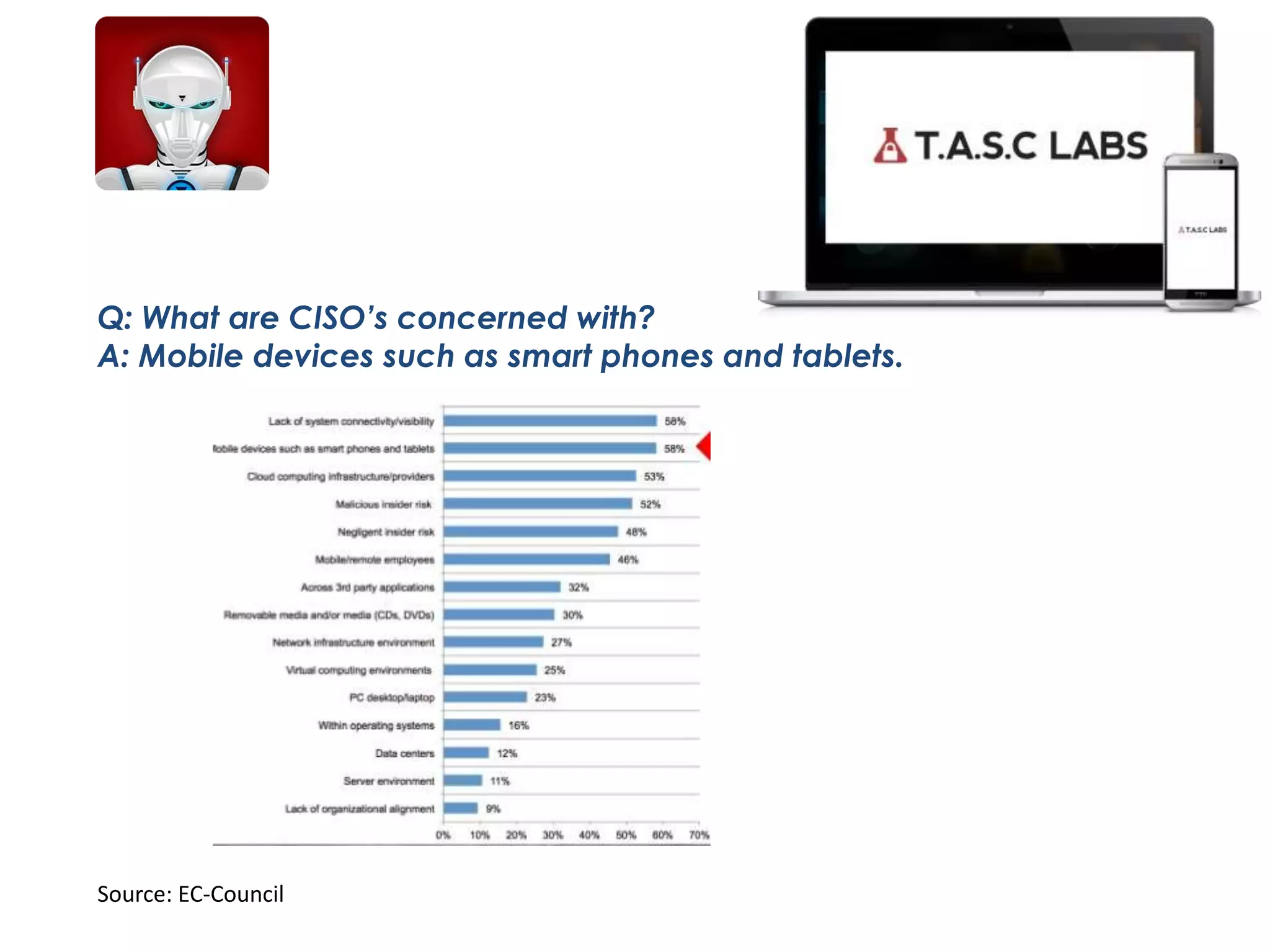
TASC is a cybersecurity dashboard that allows users to activate security apps to protect mobile devices. It provides anti-theft features to track and wipe stolen devices, as well as encrypted communication apps. BYOD trends show most employees use personal devices for work, increasing risks. CISOs and users are concerned about inadequate mobile security exposing companies to data breaches from lost or stolen devices containing sensitive information and malware. TASC aims to control mobile devices and minimize these threats.